Connect iPhone or iPad to IPsec VPN with FortiGate
In this document, we'll look at the configurations needed to connect an iPad or iPhone device to a FortiGate IPsec VPN, with this we will be able to make the corporate applications of our iPad/iPhone work directly, ideal for putting on a softphone-type application and calling (or receive calls) directly from such devices, saving the costs of calls or being 100% Available,
We will be able to rely on these previous documents if we need, since in this document we will only describe the VPN part and we will not talk about whether they are local users of FortiGate or we authenticate against an LDAP:
i) Make a VPN with IPSEC in Fortigate and connect with FortiClient – HERE.
Ii) Using Fortigate Authentication Against Active Directory Using LDAP – HERE.
Requirements: we will need any FortiGate with FortiOS greater than or equal to 4.0 MR1 Patch 1 and any iPad or iPhone device with Wi-Fi or 3G connectivity.
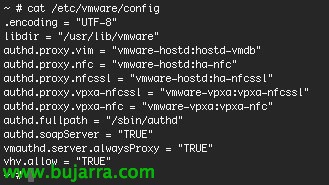
We will have to create the phase 1 and the phase 2 since “VPN” > “IPsec” > “Auto Key (IKE)”, First from “Create Phase 1” & a posteriori “Create Phase 2”,
In the Phase 1 We must give him a name, indicate that the 'Remote Gateway'’ Be “Dialup User”, we will indicate in 'Local Interface’ the WAN from which it will be accessed, the 'Mode’ Select “Main (ID protection)” in 'Authentication Method’ we will indicate with “Preshared Key” and indicate the key that will interest us. In 'Peer Options'’ Mark “Accept any peer ID”. In the advanced options we will indicate 'IKE version’ a “1”, in 'Local Gateway IP’ Mark “Main Interface IP”, In the first encryption, we will mark “AES256” & in authentication “MD5”; in the second encryption method “AES256” and in authentication “SHA1”; at 'DH Group’ Be “2”, the 'Keylife'’ “28800” Seconds. At XAUTH we dial “Enable as Server”, 'Server Type’ Be “CAR”, we add the group of users we want to connect to that VPN, we enable the 'NAT Traversal’ and the 'Dead Peer Detection'.
We created the Phase 2, We will select the phase 1 that we just set up. In the advanced options we will mark encryption and authentication in the same way, first will be “AES256” with “MD5” and second “AES256 with “SHA1”, enable 'Replay detection’ and 'Perfect forward secrecy (PFS), in the 'DH Group’ Mark “2”, Indicate “1800” seconds for the 'Keylife', enable 'Autokey Keep Alive’ and in 'Quick mode selector'’ in 'Source address’ and in 'Destionation Address’ Indicate “0.0.0.0/0”.
As usual, once the VPN is configured, we must create a firewall rule in “Policy” > “Policy”, especificaemos en 'Source Interface/Zone’ The newly created VPN, as well as in 'Source Address’ the network we have defined for the VPN; in 'Destination Interface/Zone’ we will indicate where we want them to connect and in 'Destination Address’ the network they will connect to. We will indicate when we want them to connect in 'Schedule’ and in 'Service’ the services/ports we want to allow, finally in 'Action’ We will mark “ACCEPT” & “OK” To save.
If we have more FW rules, we will have to place it at the top to give it more priority.
And we set up DHCP for the command-line VPN, with:
Config VPN IPSec phase1-interface
edit NOMBRE_PHASE_1
Set mode-cfg enable
Set IPv4-Start-IP IP_ORIGEN
IPv4-End-IP IP_DESTINO Set
Set IPv4-Netmask MASCARA_DE_RED
Now, from an iPhone or iPad, since “Settings” > “General” > “Net” > “VPN” We will set up the new connection from “Add VPN Settings…”
And we enter the necessary data to connect, A description, VPN server (Public Name) to which we will connect, a user with permissions to connect to the VPN next to their password and in the 'Secret'’ we will indicate the Preshared key entered in the VPN config.