Implementing FSSOs to integrate Fortigate with Active Directory
In any organization where there is (at least) a Fortigate and also an Active Directory, This is a must. This integration will allow us to, among others,, as adding AD users or groups to firewall rules, or at the record level, Audits, Threat Prevention… Well, having the user's detail.
What I said, if you have Fortigate and Active Directory and haven't integrated them yet, We are going to try to show the necessary steps in this post. We will install the Fortinet SSO Collector Agent on the domain controllers that we have, or more we knew as FSSO. This agent will allow us several things, among them and very interesting, be able to create firewall rules specific to Active Directory users or groups of the type: If you're not So-and-so, you don't get to that server, Navigation Controls… And another benefit that we will have will be that every time a log is generated in our firewall, will register the user who generated it. Required in any organization.
Eye, a VERY important thing, if you have a Remote Desktop server or Citrix VDA machine where users share an IP address, We will then have to install a particular agent on these machines. We will see this at the end of the post.
Installing the Fortinet SSO Collector Agent,
First of all, as we indicated, will be to install the FSSO Collector Agent AD on our domain controllers. We can download the FSSO Agent from the Support website by Fortinet.
We install the agent, It doesn't have much mystery, “Next”,
We accept the terms of the license, “Next”,
Default Path Installation 'C:\Program Files (x86)\FortinetFSAE', “Next”,
We must indicate an account with administrator privileges to start the service, Please, Create a specific user, Don't use the domain manager for this. In this website You have some tips to secure this account. “Next”,
We confirm that we have both options checked, and we are still in the advanced mode, “Next”,
Come, ready, “Install” to start installing,
… Wait a few seconds…
And “Finish” but ensuring that we are going to start the FSSO assistant.
Configuring Fortinet Single Sign On,
We must indicate the IP address of this domain controller, the IP and port that the Agent will listen for. “Following”,
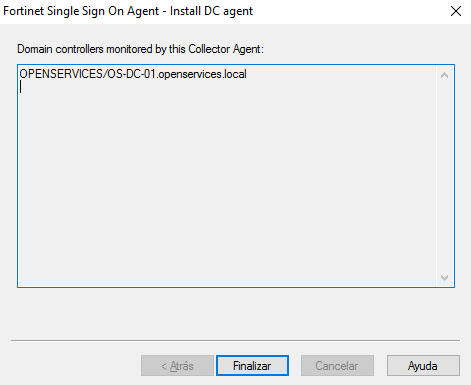
Select the domain from the listing to monitor, “Following”
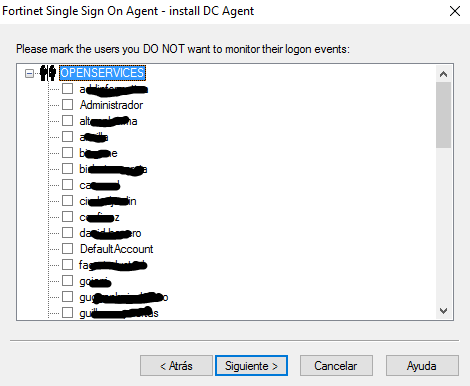
And if we want to avoid collecting logs from a particular user, we can mark it now, “Following”,
Mark “DC Agent Mode”, this will require the agent installed on the DC and be careful that it will restart the DC; or “Polling Mode” if we don't want or can install the Agent on all DCs.
“End”,
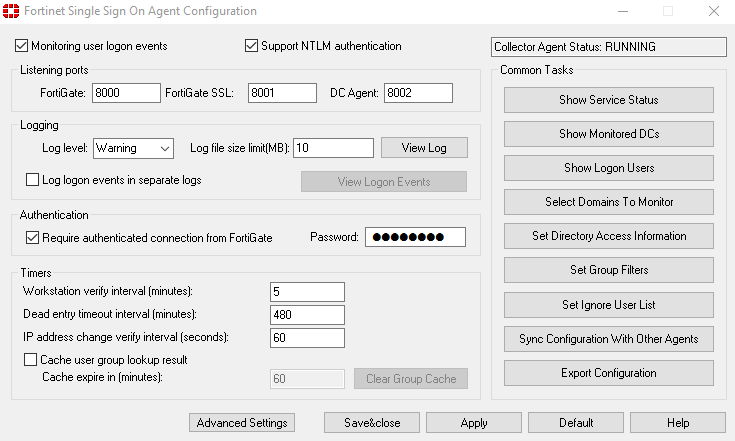
After the wizard is finished, We'll open the “Fortinet Single Sign On Agent Configuration”, we verify that the service is running, We review if we want to modify any parameter, among them “Require authentiated connection from FortiGate” where we can put a password that we will use next,
Creating the connector against the AD,
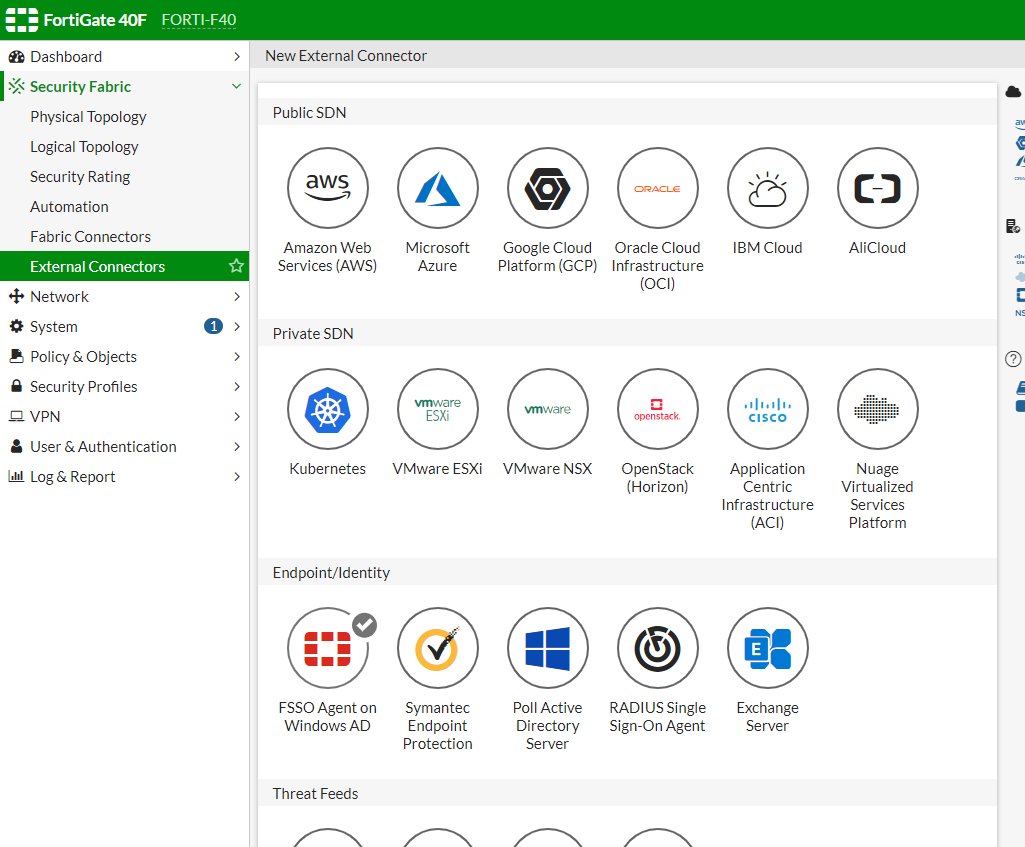
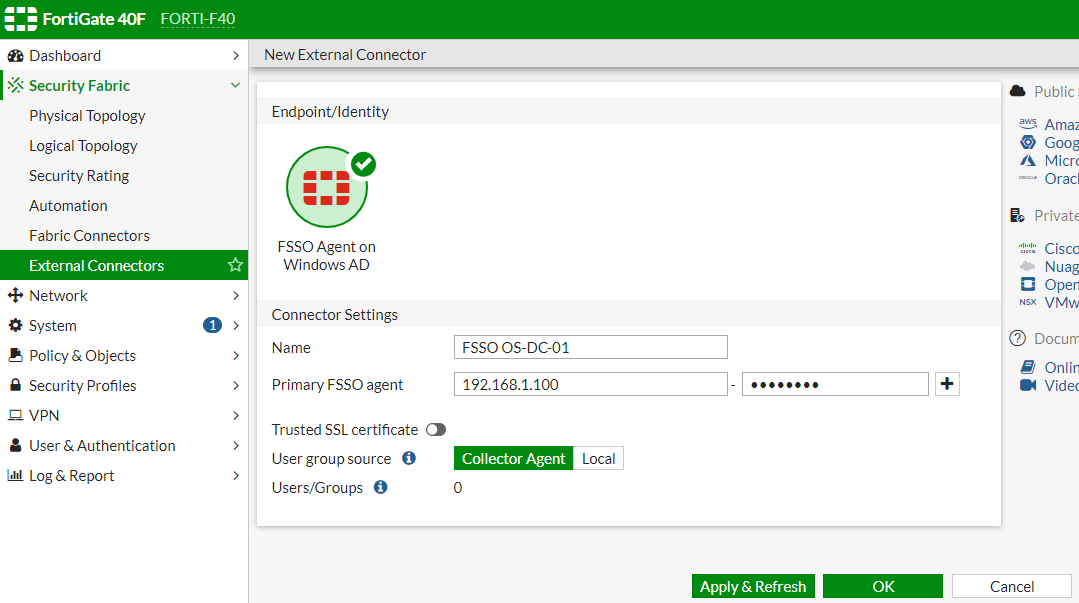
It's time to go to our FortiGate and create the connector that will join you to our Active Directory, We're going to “Security Fabric” > “External Connectors” > and search for 'FSSO Agent on Windows AD'.
Selecting it will give the connection a name and indicate the machine(s) that have the FSSO agent installed, next to the password we set for you two steps ago, Click on “Apply & Refresh”,
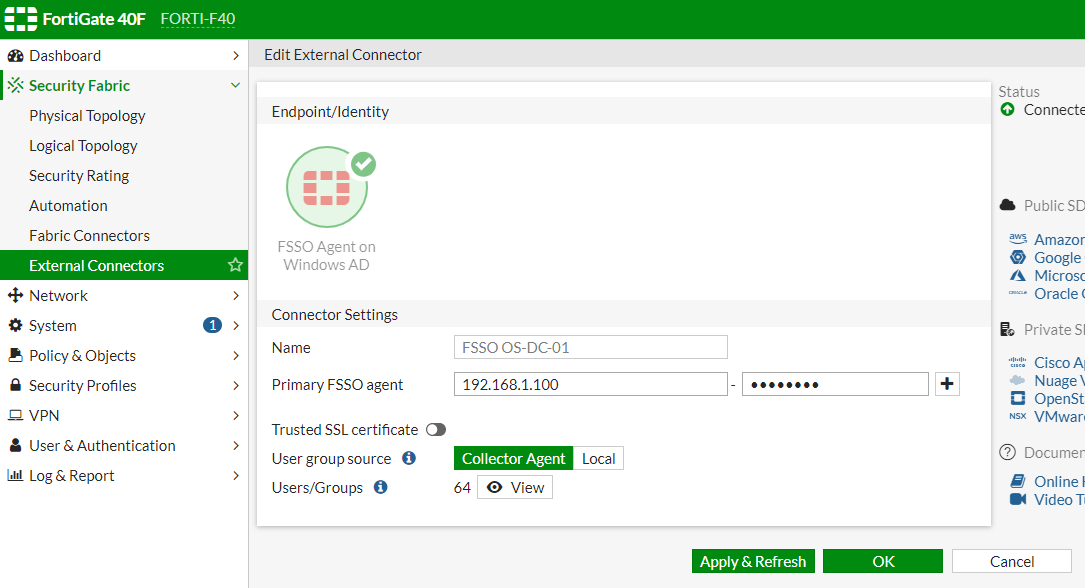
And we will see how it already detects several objects of type User or Groups, “OK”,
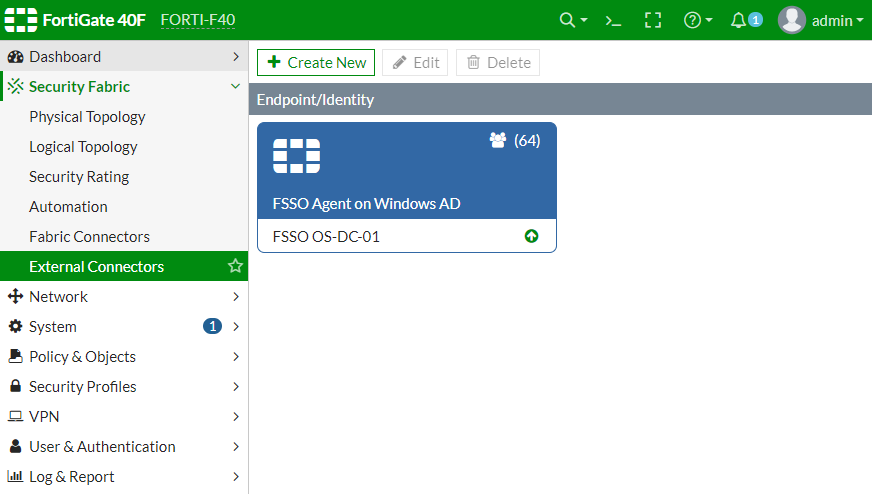
We verify that the connector is now up,
Validating FSSO,
And now we can start defining the groups of our Active Directory in Fortigate, since “User & Authentication” > “User Groups” We can create a new group, tell you that it is of the “Fortinet Single Sign-On (FSSO)” and in the members we will be able to directly add the Users or Groups that interest us from the Active Directory.
These Users or Groups that we define can come in handy, for example for this, to edit or create firewall rules where we indicate that if you do not belong to a, because you don't access the Internet, to give an example. In the rule, at the Source, apart from how we know we can put IP addresses or network ranges, now we can choose these users or groups from the Active Directory. Fabulous!
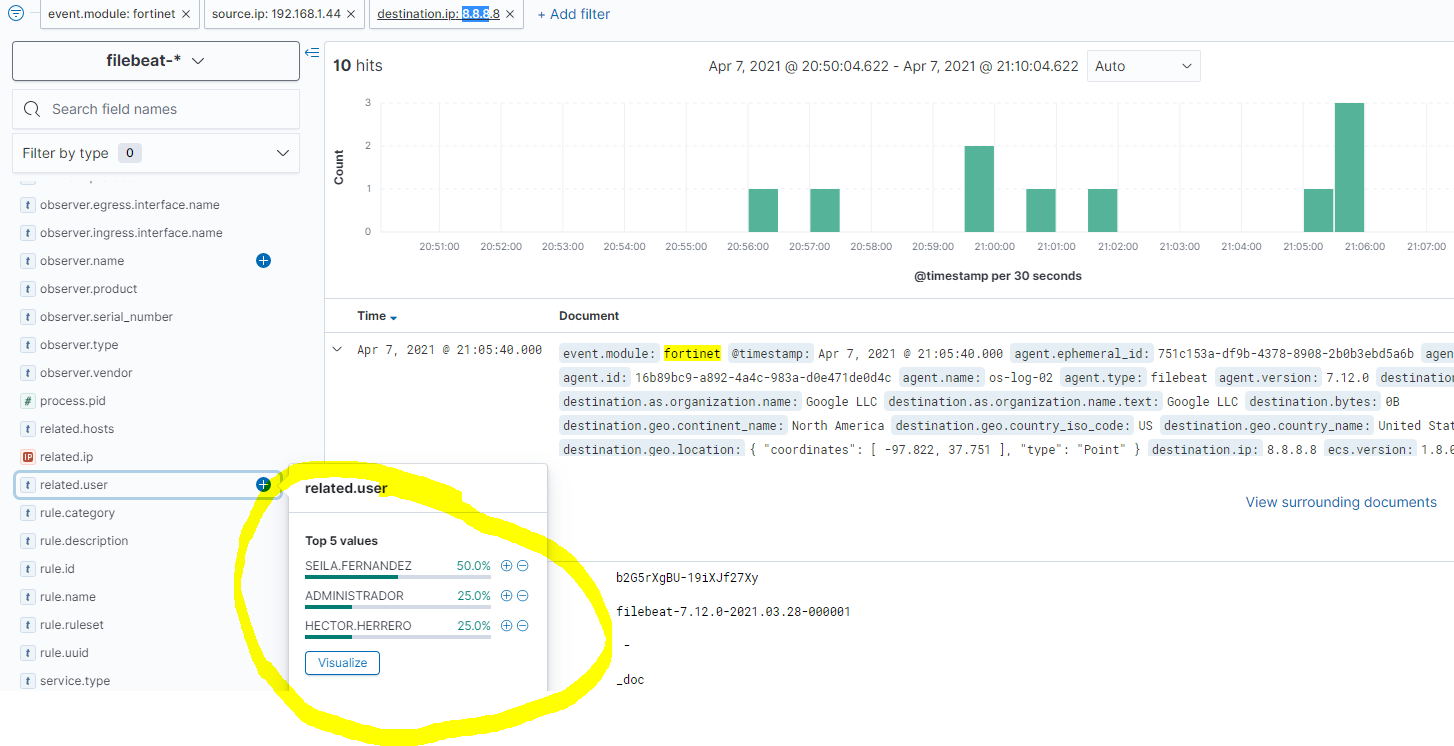
¿And this? A marvel, Now in the firewall logs a new field will appear with the data of the user who has generated the log! We will now be able to know which users visit which websites! 🙂
And as always, If we have a log collector, It will be quite a useful field, since it will allow us to pursue at the user level any details that the FortiGate firewall registers!
FSSO Agent Installation on Remote Desktop Servers or Citrix VDA,
What I said, if you have a machine where multiple users work under the same IP address, usually over Terminal Services servers or Citrix VDA servers, On these machines it will be necessary to install another agent that we will also have to download from the Support website by Fortinet.
On each server we must install the Fortinet SSO Terminal Server Agent, “Next”,
We accept the license agreement & “Next”,
Same as before, Default path “C:\Program Files (x86)\FortinetFSAE”, Pressed “Next”,
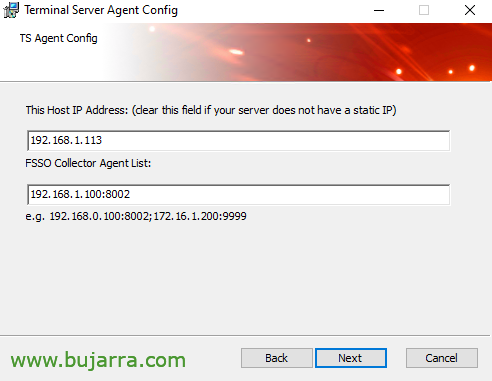
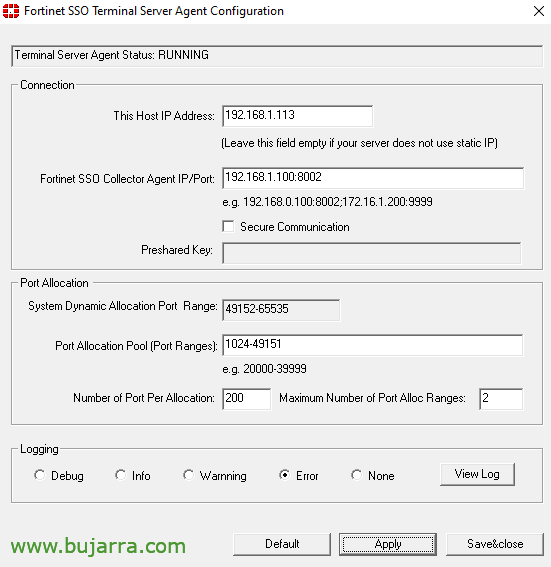
We indicate the IP address of the server itself, the IP we have and additionally we must indicate the IP address of the FSSO Collector Agent, if we have more than one we must add them. “Next”,
Pressed “Install” to begin installation,
… Wait a few seconds…
“Finish”
And if we want to open the configuration console “Fortinet SSO Terminal Server Agent Configuration”, but in principle we would not have to make any changes.
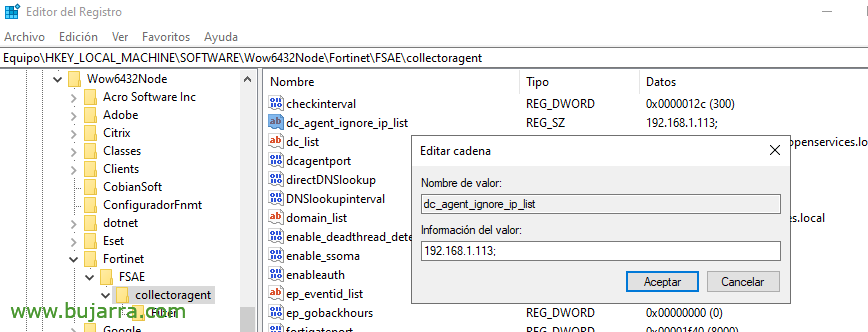
In the FSSO Agent of the DC(s) we must edit a registry key to ignore the IPs that have the TS Agent installed, so we will not duplicate what we collect from those machines, if not only the TS Agent in them.
We edit in the key “HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeFortinetFSAEcollectoragent” The cadeba 'dc_agent_ignore_ip_list’ and indicate the IP addresses of the TS Agent.
And if everything goes well, then in the FSSO tool we will see in “Show Logon Users” which comes out as 'TS-Agent’ in the 'Type' column.
Well, Here we end for today, as always hoping that someone can find it useful, which is not only to put a FortiGate in companies and that's it., that there are many things that can be done to make a consistent use of it, I'd bet my right hand (The good one) that half of companies don't even use UTM in their rules, And I bet it from experience, so I find myself in the worlds of God…
Well, that, integrate your Forti firewalls into Active Directory and be good!
Take care of yourselves, May it go well, Hugs,