VPN with Citrix NetScaler III – Authentication with certificates
I really like this post, in today's paper we will look at how we can get our dear and beloved users to access NetScalet Gateway through their own SSL certificates and not in the traditional way; making it more agile and with a Smart card (USB or NFC) they will enter more safely.
So continuing this series of posts of setting up a VPN through NetScaler Gateway, today we will force access to the environment through personal certificates that we will have previously generated in our Active Directory, as well as distributed to our users in physical or digital format.
This post is structured as follows:
Configuring in NetScaler to require certificates on the logon
Creating the Authentication CERT profile
We create the authentication profile to require certificates from, “Citrix Gateway” > “Policies” > “Authentication” > “CERT” > “Profiles” > “Add”, We give you a name and choose the attribute with the username field, “Create”,
Creating the Authentication CERT Policy
We now create the policy and link it to the newly created profile, since “Citrix Gateway” > “Policies” > “Authentication” > “CERT” > “Policies” > “Add”, indicating a name and the expression 'ns_true'. “Create”,
Linking the policy to NetScaler Gateway
On the NetScaler Gateway's Virtual Server, the certificate from the organization's CA is binded to it (If we haven't done it already),
On the Gateway's Virtual Server in “Basic Authentication” we must add a new one, We select a policy of type 'CERTIFICATE'’ of the 'Primary' type’ and click on “Continue”,
Select the previously created policy and click on “BIND”,
'1 Cert Policy' is now associated, Click on “Donate”.
By the way, take into account in the LDAP server the 'Server Logon Name Attribute’ since by default it is 'sAMAccountName’ And that would be something like Hector.Herrero and wouldn't allow me to log in like ‘I************@**********es.local‘ which is how the user that is issued in the certificates appears.
Testing
We open the Citrix NetScaler Gateway website again, If we do not have our certificate, we will not be able to log in.
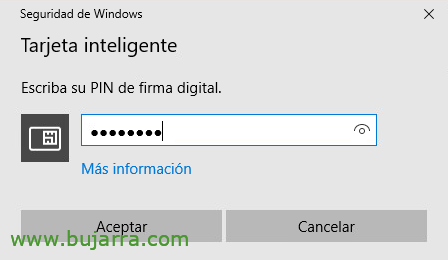
On the other hand, if we have our smart card or certificate installed, when you enter the Citrix NetScaler Gateway website, it will already ask you for the PIN to access your certificate and will show you the web portal loading…
Later it will launch Secure Access and ask for the PIN…
And it will ask for the password, The user will take it from the certificate and it cannot be modified. This happens to us because we still have the LDAP policy linked.
And after entering the credentials we will be able to access as usual!
Smart Card Simulator
In this final part we will talk about how to generate a user certificate and how if we don't have a USB Smart Card reader we can simulate it with software. In a previous document, we have already seen how certificates can be generated for the users of our Active Directory, You can follow those steps. Or these using a simulator software called EIDVirtual Smart Card, for use in MVs and LABs can come in handy, we have 30 trial days and can be downloaded from here.
We install the software, which doesn't have much mystery and then we launch the configuration wizard. We plug in a USB flash drive and it will use it for it, we indicate our pen drive letter and a PIN, will format it for this. We can then save certificates in it 😉 “Format”,
“Yes”,
It's normal, Not detecting the card, You have to unpuncture the pen drive and plug it back in…
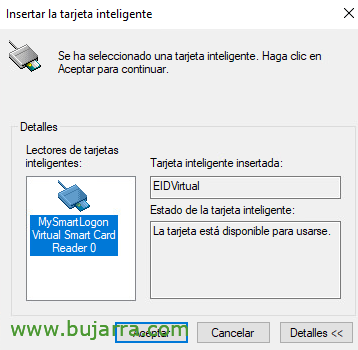
List, detects it, Accept!
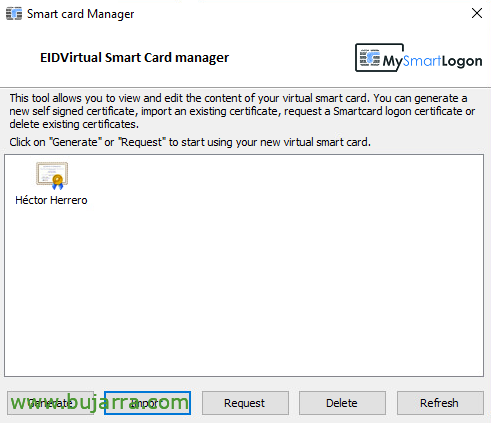
The Smart Card Manager now loads, What is used to manage this pen drive?, that is, this SmartCard, and install certificates, We can import them… open the utility as an administrator if we are going to import PFX. If we want to request from here to the AD a certificate for the user with whom we are logged in, we give Request.
Enter the PIN of the card,
We select the CA of our AD & Accept,
And ready certificate requested and generated in this simulator or virtual smart card, we can install them manually…
I hope that this type of post encourages you to increase your security a little, apart from the convenience of working with Smart cards and certificates; =) As always hoping that it goes VERY well =)