Monitoring Crowdsec with Centreon
If you have implemented Crowdsec and Centreon in your organization, I imagine that apart from being happy and resting, You will have everything quite under control; but, and… What if I tell you that from Centreon we can monitor the bans that Crowdsec gives us?? Effectively, when Crowdsec adds an IP address to the blacklist we can alert ourselves via Centreon!
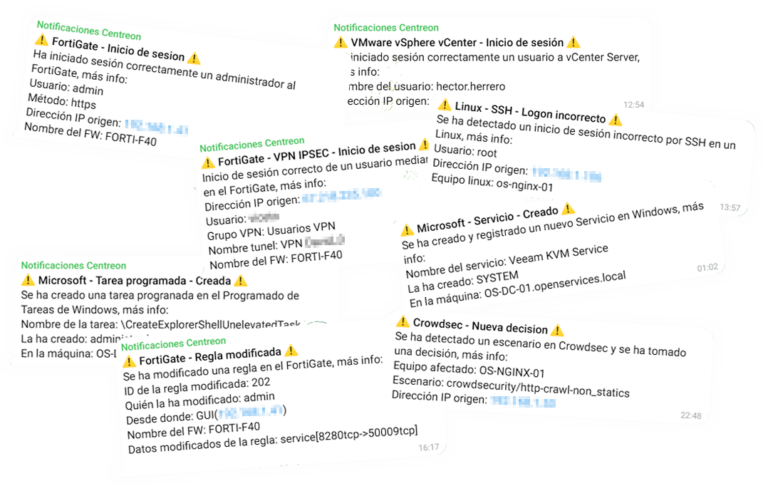
I think that many of you already know how Crowdsec works and the advantages of using it in any organization and even personal spheres, The idea is that as we know, Crowdsec detects threats, any attack or 'weird thing'’ that may suffer from any service that we have published on the Internet. We know that Crowdsec itself can notify you when it adds the IP address of any attacker via email, Telegram, Slack, Teams… But by having all IT notifications centralized, Well, maybe it's a good idea that Centreon can take care of this too, Not just to know when someone is blocked, if not to have that control, have that data stored…
So we'll make a Command that will be executed in Centreon to check on our Crowdsec Central API server if any Crowdsec machines have been attacked, that Command as always we will associate it with a Service in Centreon and it will be ready. First, in our Crowdsec central API server we will have to register a new bouncer to be able to use its Token and perform the queries by API:
cscli bouncers add CENTREON-MONITORIZA API key for 'CENTREON-MONITORIZA':
uz0Oxxxxxxxxsdfsdf Please keep this key since you will not be able to retrieve it!
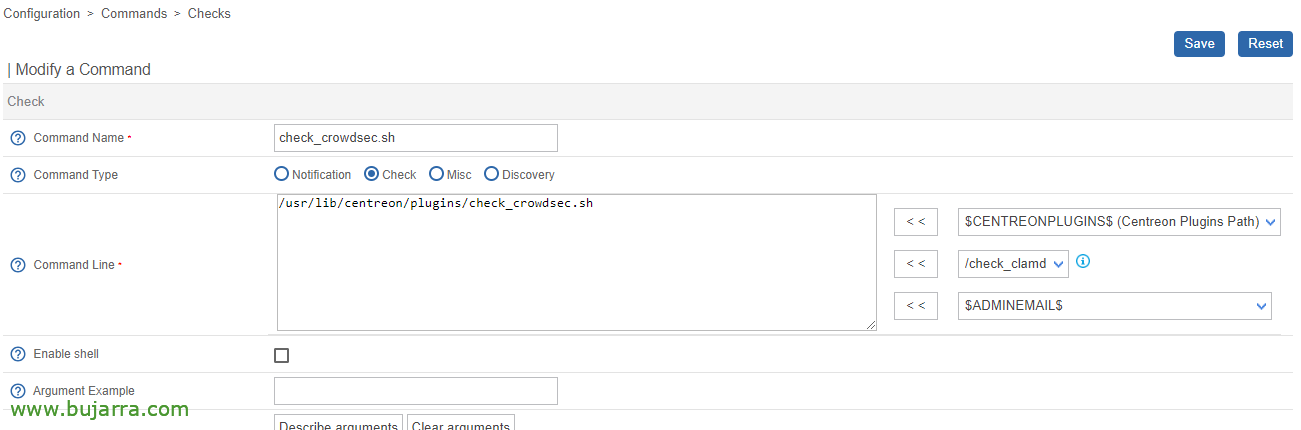
In the Centreon Central or Poller we will therefore create a script to monitor it, For example, called something like /usr/lib/centreon/plugins/check_crowdsec.sh, remember after recording it make it executable with (CHMOD +X), In the script we will have to have a couple of considerations, enter the API key and IP address of the Crowdsec Central API
#!/bin/bash
# Make the request with curl and filter with jq result=$(curl -s -H "X-API-Key: xxxxxxxxx" HTTP://DIRECCION_IP_CROWDSEC_LAPI:8080/v1/decisions/stream?startup=true | jq '.new[] | Select(.uuid != null) | {value, scenario}')
# Count unique IP addresses ip_count=$(ECHO "$result" | jq -r '.value' | sort -u | WC-L)
ip_list=$(ECHO "$result" | jq -r '.value' | sort -u | Paste -sd,)
# Check for banned IP addresses and generate the if message [ "$ip_count" -Gt 1 ]; Then echo "CRITICAL: There are $ip_count banned IP addresses: $ip_list"
exit 2
Elif [ "$ip_count" -Gt 0 ]; Then echo "CRITICAL: There is $ip_count banned IP address: $ip_list"
exit 2
Else done "OK: There are no banned IP addresses."
exit 0
fi
Later as follows the custom, we will create the Command in Centreon, It will be enough to give the command a name with the following command line '/usr/lib/centreon/plugins/check_crowdsec.sh'.
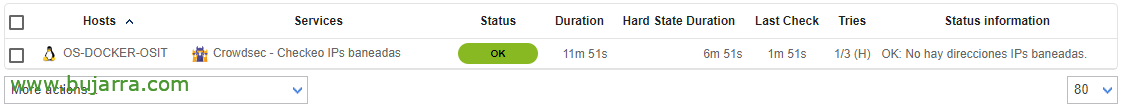
We created a service in Centreon called for example 'Crowdsec – Checking banned IPs’ and we associate it on the Crowdsec server and in the 'Check Command'’ it will be enough to choose the newly created Command.
Once the configuration has been saved and exported in Centreon, we will be able to see our check-up and verify that it works correctly.
In the event of detecting an IP in the blocklist or blacklist, it will alert us, you can try adding a decision manually from the Crowdsec CLI and you will see how the service in Centreon goes to CRITICAL and alerts us to which or which, are the IP addresses that have been banned by the system.
Well, I hope that this document can inspire you in what types of things we can set up to have more control in our organizations in order to achieve greater security, or for those who may not yet know what Crowdsec is and can encourage them to discover it… Well, What that, That you behave very well, enjoy the fruit!