Rules and alerts with ElastAlert 2
The party begins as the other one said… I'm going to show you some things that I think you'll like to be able to exploit your logs and evolve our SIEM into a SOC, Very interesting topics. First we have ElastAlert2, which is an open-source tool that will allow us to generate rule-based alerts with data stored in Elasticsearch.
If you save, e.g. logs in Elasticsearch, either logs from your Active Directory, From Entra, from your firewall, of your servers, stalls or other gadgets… We will be able to make queries in an automated way through a series of rules, and then alert us if we were interested in any situation (or execute actions). Well ElastAlert 2 He has come for this, to help us, we will be able to create (or import) as many rules as we need them to make the queries we need.
In this document we will look at a concrete example, I do not know, There are so many possibilities… We are going to try to detect when our system is compromised, Detecting suspicious activity (or malicious), in the end it is a matter of preventing greater evils, either by alerting us or by generating actions that mitigate the scenario. Well, that, in the example that we have, We'll try to detect when someone (For example) you have successfully logged into a FortiGate firewall. As it is a first document we will do this, Detect, and generate an alert by Telegram. In other documents we will see many more things that can be done.
Txapas on the side, ¡Started! What do we need? Well, the usual! Patience and Docker!🤣 So on a machine with a Linux that we have for these purposes, and after installing Docker and Docker Compose, Well, we're going to deploy a container with it, It's that easy, this container, ElastAlert2, will be in charge of reading the rules files that we leave in a folder and making, what you have to do 😅.
git clone https://github.com/jertel/elastalert2.git CD elastalert2 mkdir config mkdir rules
And we create our docker-compose.yml with something like this:
version: '3.9' Services:
elastalert2:
image: 'jertel/elastalert2:latest' volumes:
- './rules:/opt/elastalert/rules'
- './config/elastalert.yaml:/opt/elastalert/config.yaml' container_name: elastalert restart: unless-stopped networks:
red_elastalert2:
Networks:
red_elastalert2:
driver: Bridge
And first of all, we will also have to edit the ElastAlert2 configuration file './config/elastalert.yaml', where we'll indicate the Elasticsearch server, Your port, Access credentials… And while we're at it,, let's enter the data of our Telegram, since we have said that we want to receive alerts of this type.
es_host: "SERVIDOR_ELASTICSEARCH" es_port: PUERTO es_username: USER es_password: PASSWORD rules_folder: rules run_every: minutes: 1 buffer_time: minutes: 1 writeback_index: elastalert_status alert_time_limit.days: 2 telegram_bot_token: "TOKEN_BOT_TELEGRAM" telegram_room_id: "ID_GRUPO_TELEGRAM" telegram_parse_mode: "HTML" alert_text_type: alert_text_only
We've got it ready, All that's left is to unfold it, and I leave you below the command to see the logs in case you have any incident:
Sudo Docker compose up -d sudo Docker logs elastalert -f
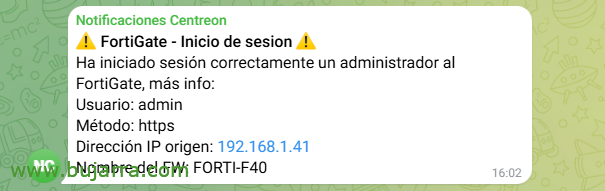
And now there's the hard 🤠work, the beautiful 😍 part, which is nothing more than creating the rules we need, as many as, in this case alerts we want to receive, that or import existing 😉 rules. I leave you with the example of a rule (./rules/OpenServicesIT-Fortinet-FortiGate-Login-Correct.yaml) Where we'll see what we expect, a rule that will search for logs in a FortiGate with successful logins, This is, every time someone logs into a FortiGate, by GUI or CLI, in a satisfactory way. That alert is the one we will receive, in this case by Telegram and nothing else we will do (For now)….
Name: Fortinet-FortiGate-Login-Correct Type: frequency num_events: 1
index: filebeat-* threshold: 10
use_count_query: false timeframe:
minutes: 3
filter:
- query:
query_string:
query: 'tags: fortigate AND fortinet.firewall.action: login AND rule.description: "Login Successful"' alert:
- Telegram alert_subject: <b>FortiGate - Login</b>
alert_text: |
An administrator is successfully logged in to FortiGate, More info:
User: {0}
Method: {1}
Source IP address: {2}
FW Name: {3}
alert_text_args: ["source.user.name", "fortinet.firewall.method", "source.ip", "observer.name"]
How do you see, It has a rule format that we must comply with in a meticulous way, There are many possibilities, in this particular case each 1 minutes we will make an Elasticsearch query and as soon as we have 1 event, because it will generate such a beautiful alert on Telegram. Don't drive Telegram crazy with 'silly' alerts either’ that for that we will have other incident management tools, but it is a very practical example to show.
Once our rule is created, or when we modify them, ElastAlert2 will reload them automatically, We don't need to reset anything. And it's that easy, this will start looking for what we need in our Elasticsearch! I'll probably give you some other examples of curious rules that can be made with ElastAlert2, Whatever check against blacklists, Impossible travel detection or the time traveler (or whatever you say), integrations with Crowdsec decisions… There is fabric to cut…
Wishing you great, You take care of yourselves, And as always, Umbrella for the rain and umbrella for the sun 😅, what old phrases… A hug! 🫂