Setting up one cluster, two or more Fortigate
This procedure explains how to configure two Fortigate firewalls in clustered mode, for high availability. Both firewalls need to have the same firmware version. In my case they both have a version 3, With a built 400. I've set up the following features for each of them:
Hostname: Mortadelo
IP de la DMZ: 192.168.4.1
IP de la Internal: 192.168.2.1
IP de la WAN1: 192.168.1.155
Hostname: Filemon
IP de la DMZ: 192.168.4.2
IP de la Internal: 192.168.2.2
IP de la WAN1: 192.168.1.156
IP addresses don't matter which one to assign (Logically) I simply indicate it to say that the other interfaces are disabled.
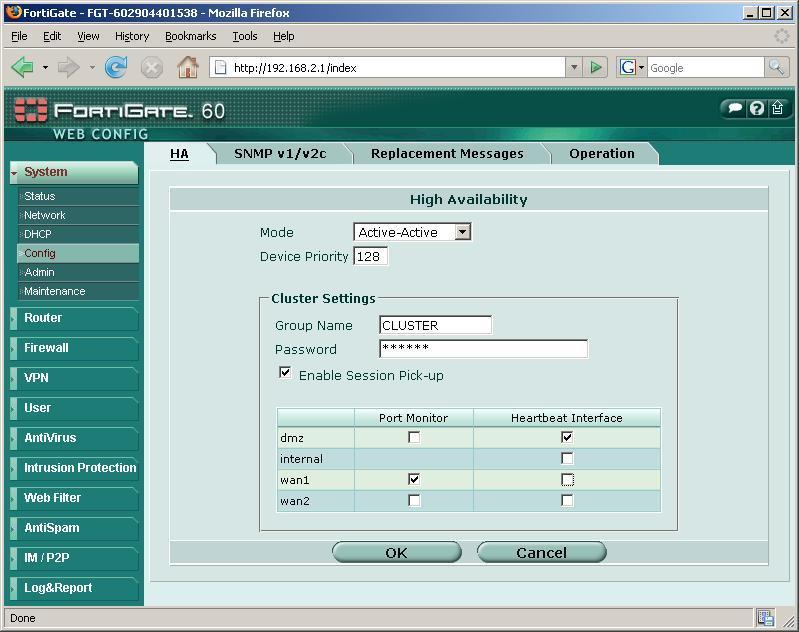
Well, What would have to be configured to make this cluster, We're going to “System” > “Config”. In “Mode” We will indicate the status of this firewall, If it's in “Standalone” means that it will not belong to any cluster. If it's in “Active-Passive”, the one that is in passive mode would be as turned off or waiting for the one that is as active to fail. The most logical thing to do is to set it as “Active-Active” so that they are done as a load balancing and share the load. Priority indicates, what will be the priority of this firewall in the cluster, we can have several with more or less priority for them to carry the load, they are usually all put with the same priority. In “Group Name” is simply the name of the cluster, in my case “CLUSTER” and we assign it a password/password for when we want to join more firewalls to this cluster. We enable “Enable Session Pick-up” to indicate that sessions are not missed if there is a fall, This is logical, That's what a cluster is for (High Ability). Below we indicate the interfaces that we want to monitor with the Logs (“Port Monitor”) which are usually external interfaces. And in “Heratbeat Interface” We will mark the ones that will be connected between the firewalls, In these Fortigates, the normal thing is to connect them through a port that we have free, as in my case by the DMZ, so I check this check and connect the firewalls with a cross-clable between the DMZ interfaces. “OK”. We have to be patient and wait a long time for the cluster to be created, as Fortigate will have to be restarted. We give about five minutes to continue with the next step.
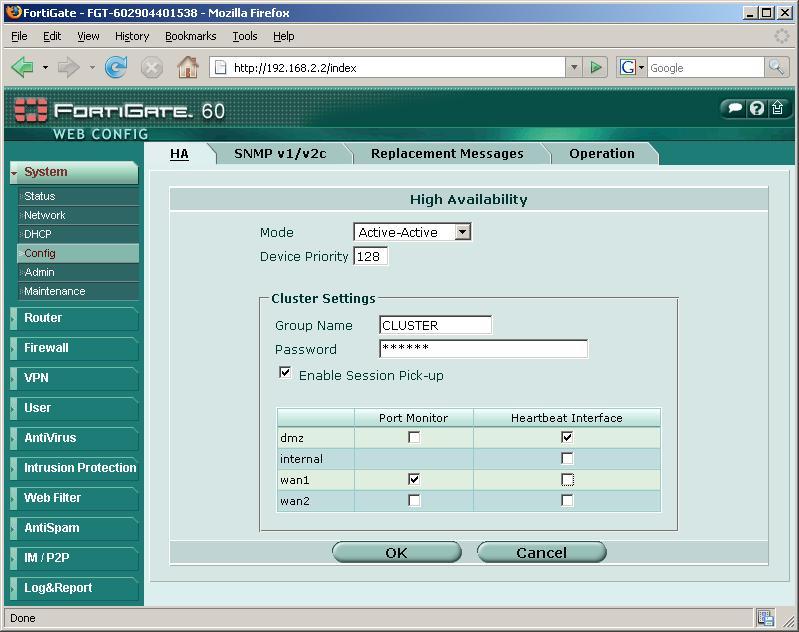
Now we do the same thing on the other firewall, if we have previously configured it in the 192.168.2.1, Now we'll do it in the next one 192.168.2.2, entering the same cluster name to join it with the same password. “OK”. Now the FW will restart, We are patient again and we wait for you to join the cluster.
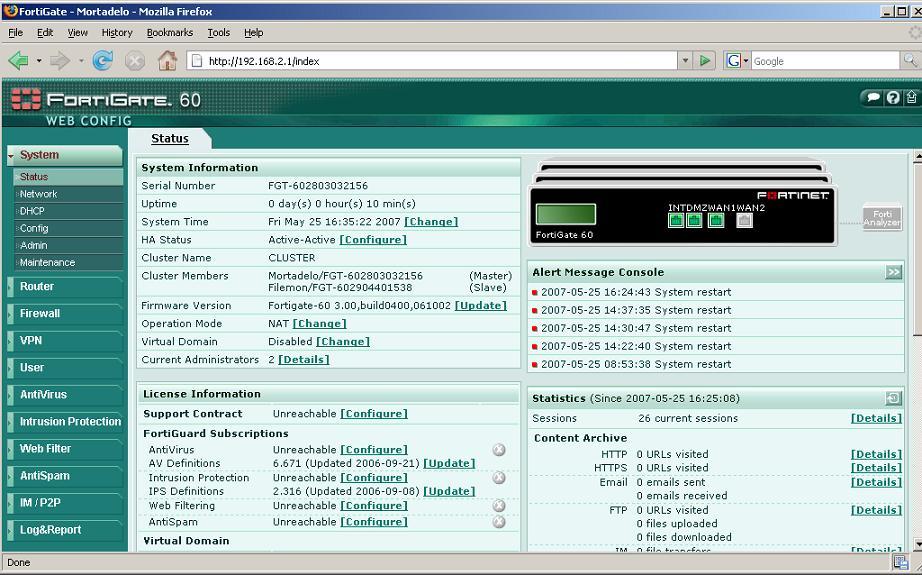
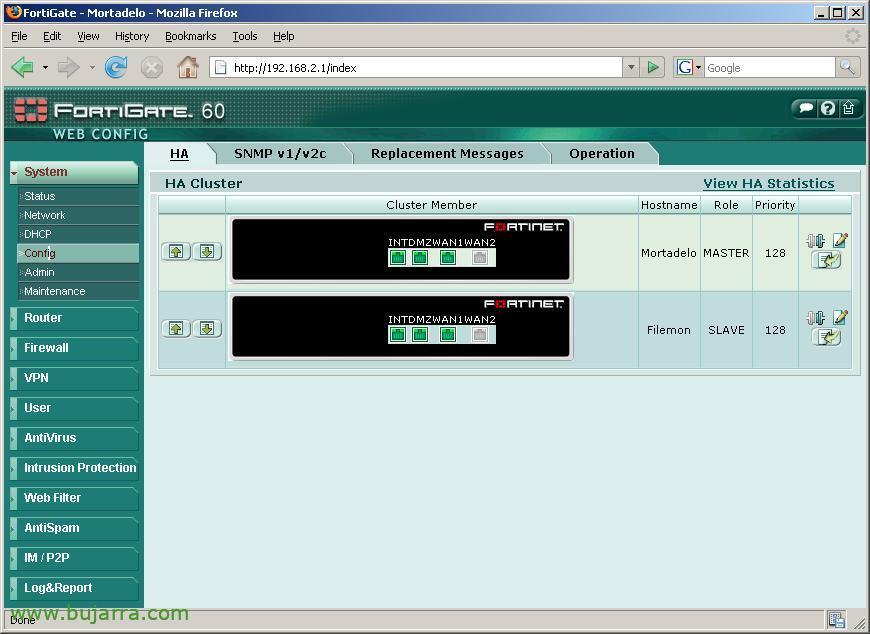
Once restarted, we will see that on the main console the image has already changed and we see several together, This means that there is a cluster, on the screen it already indicates who the cluster members are. When creating the cluster we have to take into account that the first one we do, from which we create the cluster, will be the one that maintains the configuration, since the others will inherit it from him.
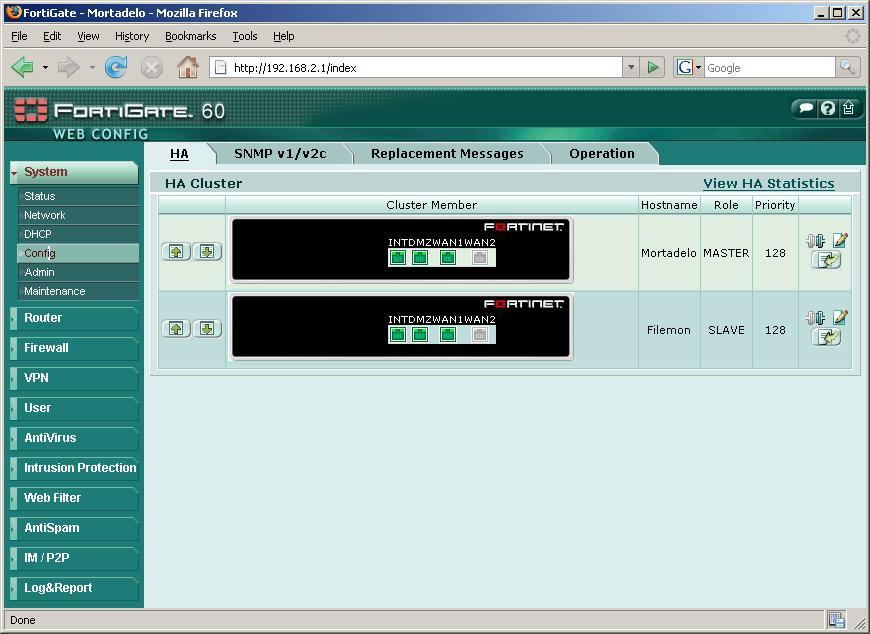
And from “System” > “Config” We'll look at more options and who are members…
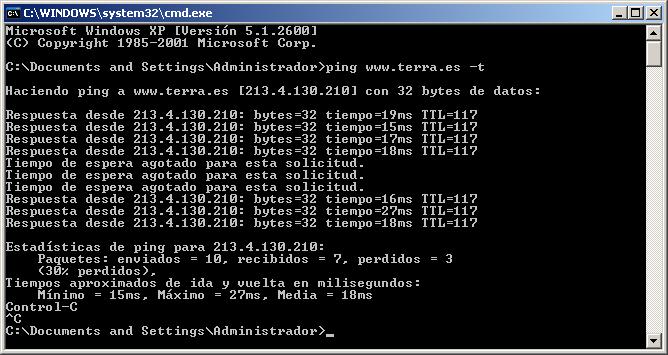
We can do a test, for example a ping to the outside and turn one off abruptly, taking away food or whatever. We see that the ping cuts off, Because the Fortigate cluster still has a lot to improve but that in a couple of seconds everything returns to its course with the other Fortigate. So the cluster works perfectly.