Using Brutus – Password cracker
Discharge – HERE
It's pretty fast and very easy to handle, The passes that can crack are: HTTP (Basic Authentication), HTTP (HTML Form/CGI), POP3, FTP, SMB, Telnet, other types such as IMAP, NNTP, NetBus etc . And this version contains these features: Gradual authentication engine, 60 Simultaneous connections by target, No username, Single username and multiple username modes, List of passwords, Combo list (user/password) and configurable brute force modes, Highly configurable authentication sequences, Import and export custom authentication types as BAD files seamlessly, Being able to use SOCKS proxy for each session, Username and password list generation and manipulation functionality, HTML Forms Interpretation for HTML Form/CGI Authentication Types, Be able to save the cracking session and be able to return to it whenever desired. System Requirements: Windows 95, Windows 98, Windows NT 4 o Windows 2000. 24 Mb RAM, 5Free Mb in your HD (hard disk) and clear internet connection. HOW TO START CRACKING The first thing we have to do is open Brutus AET2, and a window like this will appear:

Below I will explain what each section of the program is for: In “File” If we click on it, we get a detachable window with several options, Import Service, that serves to import a Service that is not included in the program such as…HTTP (Basic Authentication), HTTP (HTML Form/CGI), POP3, FTP, SMB, Telnet, IMAP, NNTP, NetBus etc. Export Service, It is used to export if you have a new service for the program. Load Session, It is used to load a session that we leave halfway. Save Session is used to save the session we are running and to be able to return to it whenever we want, Restore Last is used to restore everything we have previously chosen. In “Tools”, We found Word List Generator that serves as the name suggests to generate, manage and optimize your Word List (Password List). And I think there's little to explain. In “Target” it is used to put the Target class that we want to crack, that is, the IP, if it is HTML we will put the URL address and the program will convert it into IP, the same will happen if we put an FTP that we are going to crack. In “Type” You select the type of self-identification you are going to crack and we have already seen above all the types that there are so it is superfluous to explain them again. In “Port”, You won't have to pay much attention to it, since by selecting the “Type” What do you want to change alone, if you select Telnet the port will be automatically put 23 and so on with all. The “Use proxy” is to use SOCKS proxys when cracking see this image:
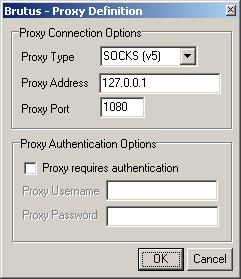
I think there is little to explain, in “Proxy Type” You have to select the type of proxy, In “Proxy Address” the IP or, failing that, the Proxy host and in “Proxy Port” the number of the port you are going to connect remembering that, if you scan HTTP (Basic Authentication) or HTTP you have to use the 80 or 8080 and if you scan, FTP, Telnet, etc. use a proxy SOCKET or by the 1080. In “Authenticacions Options” There are several options, Start: If we do not know the Usermane of the victim either when trying to hack HTML, Telnet, FTP, etc. We can use a file in which we have possible usernames so we leave the option “User Username” activated and on the “Browse” you search your hard drive for the file containing possible usernames. But if you know the name of the user, then you activate the option “Single User”and the box “User file” will be transformed into “User ID” And that's where you have to put the username that you know. In “Pass Mode” Select the type of file we are going to use: “Word List” is the option in which we will choose a file that we have with possible passwords and we will search for it on the hard drive with the button “Browse” and appear in the “Pass File” the full address where you have the Passwords file. You can also select the “Combo List”, This option allows us to use the same list of passwords to obtain the username and password. The other option is “Brute Force” that it doesn't need any files with passwords or anything, that is, he does it by brute force , It is somewhat slower than the other options as it will take a little longer to find the passes, but it is more effective, If you want to configure the ranges of passwords that you are going to use by brute force then press the button “Range” and a window like this will appear:
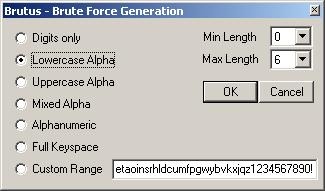
In this window you can choose which type of password you are going to use by brute force, The first thing you have to do is choose if you are going to start from 0 to the digits occupied by the passwords, That's why we're going to “Min Length” and to “Max Length” And there's a choice where it's going to start from, Example: if you select Min Length 0 and Max Length 6 Well, it will start with a single digit or letter (since “a” until “zzzzzz”) and it will go through all the letters and symbols, if you choose Min Length 6 and Max Length 6 Well, it will start with 6 Digits or letters (“Aaaaaa” until “zzzzzzz”) and so on with the number you choose. Then on the left side is where we're going to choose the type of password you want to crack, whether they are letters, number, Numbers and letters….. I explain this below, “Digits Only” Only numbers dare, that will search for passes by brute force that contain only numbers, whether it's a date, etc. “Lowercase Alpha” This option is lowercase-only letters, “Wake up Alpha” the same as the previous one but in capital letters, “Mixed Alpha” I would look for letters but not in alphabetical order, “Alphanumeric” Between mixing numbers and letters, “Full Keyspace” As the name suggests, use all keys on the keyboard, lyrics, Symbols, Numbers etc. “Custom Range” Use everything, lyrics, numbers, symbols etc. “Positive Authentication Results” is where it will mark how the progress of searching for Passwords is going and the ones it finds, see this example
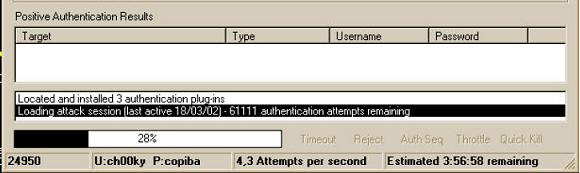
And little more to explain about this program I hope this manual will help and if I don't explain it very well then I will improve it in future editions 🙂