Monitoring Windows Events from Centreon
A fairly quick post that I think may interest many of us, and it's no more common than being able to monitor any event in the Windows Event Viewer. Can you imagine keeping an eye on the events of the domain controllers??
Being able to be aware when a User has been created, modified, deleted… or a Group, or an Organizational Unit, or a GPO (Group Policy), or whatever interests us!
Begin with, we will need the NSClient agent installed on the Windows machine to browse, If you have doubts, This post old man He can help you. And the second thing will be to know the event ID that we want to locate.
It is possible that if we want to use some special character (we'll use it in a variable), we have to have in the nsclient.ini allowed the use of strange characters; as well as the use of arguments, taking into account that we would look something like this:
[/settings/NRPE/server] allow nasty characters=true
allow arguments=true ... [/settings/external scripts]
allow arguments=true allow nasty characters=true ...
Remember to restart the NSClient service if you change the .ini
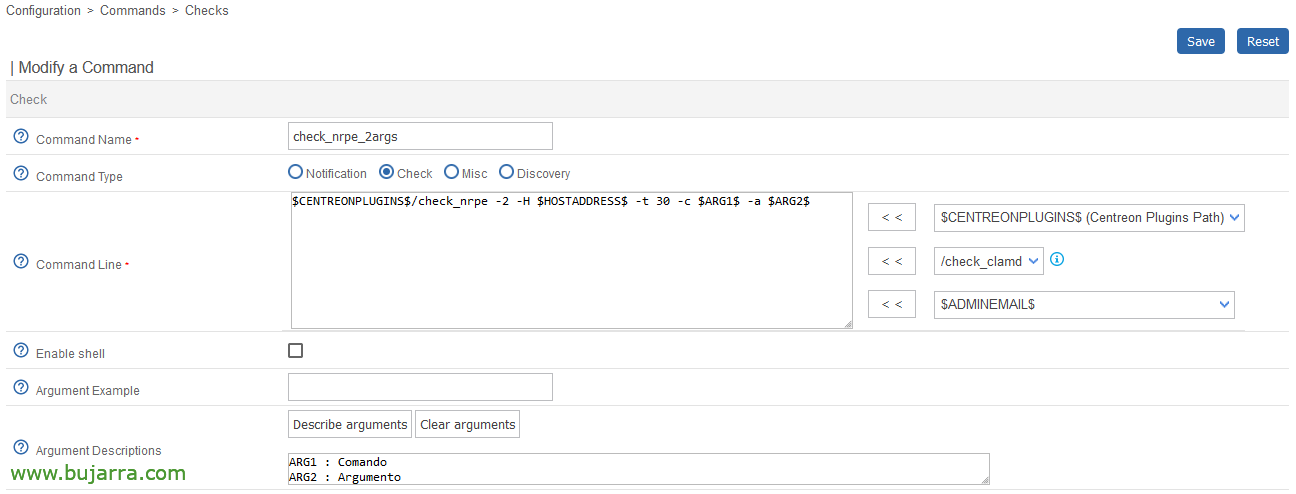
After that, I suppose that the check_nrpe Command has already been registered in Centreon, or we can register another with 2 Arguments, since the command we're going to throw at it is like this example:
/usr/lib/centreon/plugins/check_nrpe -2 -H DIRECCION_IP -t 30 -c checkEventLog -a file=security scan-range=-24h MaxCrit=1 "filter=id = 5136" truncate=300 'top-syntax=${status}. The following have been modified: ${count} OUs in the AD in the last 24h'
If you look closely, we have specified the event ID 5136 which corresponds to the fact that an OU has been modified, We can indicate the time or number of events you will read, as well as personalize the message in case the hare jumps. We can play with MaxWarn or MaxCrit to alert us to the number of events.
So we adapt the command and we'll have something like:
$CENTREONPLUGINS$/check_nrpe -2 -H $HOSTADDRESS$ -t 30 -c $ARG$1 -to $ARG$2
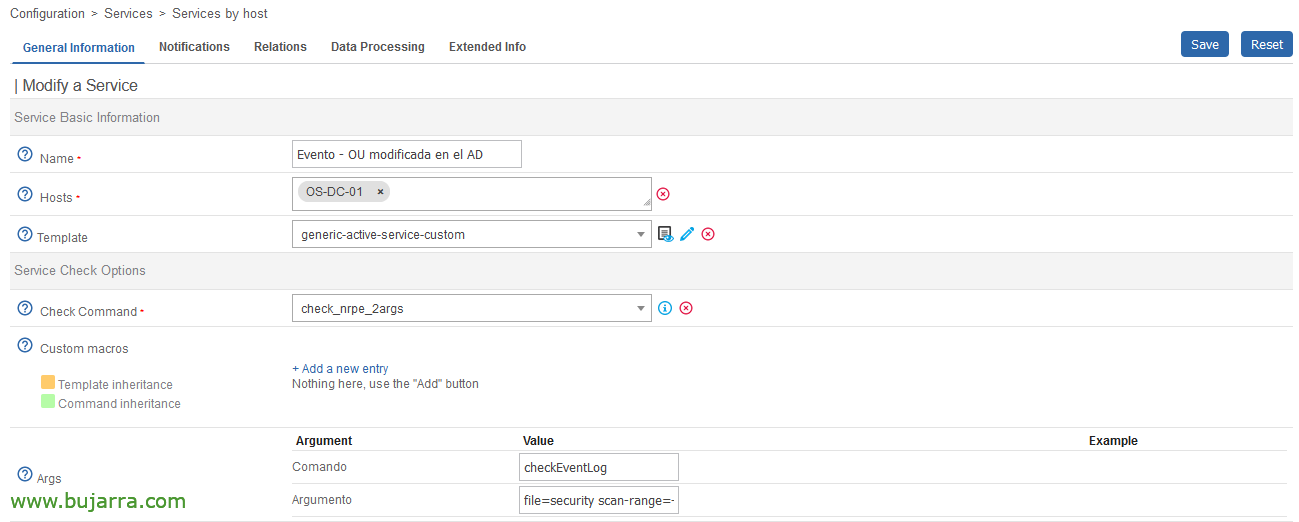
Total, that we can already create as many services as events we want to supervise, in this example the service would have the following two arguments::
Command:
checkEventLog
Argument:
file=security scan-range=-24h MaxCrit=1 "filter=id = 5136" truncate=300 'top-syntax=$${status}. The following have been modified: $${count} OUs in the AD in the last 24h'
We record and export the settings as we usually do…
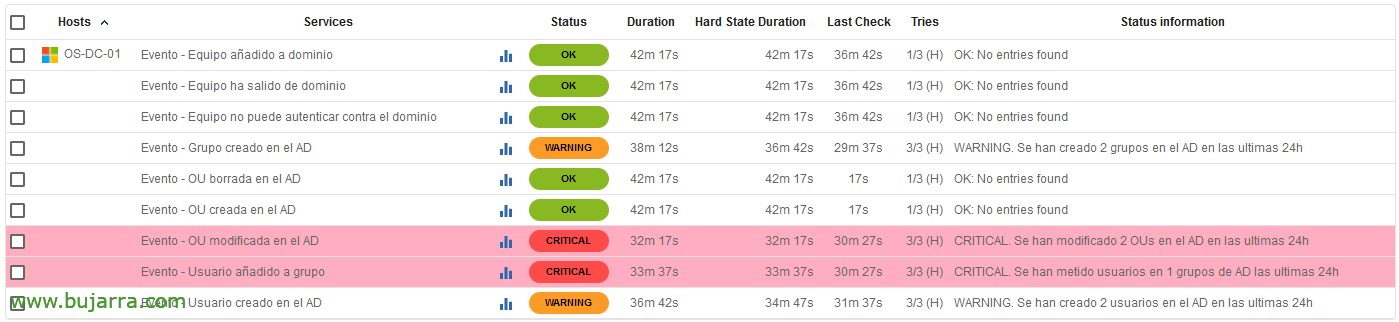
And as Juan Tamariz would say… chan-ta-ta-chan!!! ole!!! We already have some events controlled from here, if a domain team comes out we will find out, or if it joins the domain, or if a user is modified, group or whatever, or if they are created, or if they are deleted…
I leave you to think about and look for the event IDs that you are most interested in monitoring, I send you a hug, Have a very good week and above all… Be happy!