Nagios – Monitoring with NRPE
Well, Well… Let's put a little more txitxa in our Nagios, Centreon or whatever we got, We will continue with something very interesting for those who want to monitor more advanced items! We will use a small agent that will be installed on remote Windows or Linux computers, For what? Well, among other things, to execute scripts on these computers. We can run any PowerShell script, Batch, VBScript, Perl… and then read the result of the command and discuss it with Nagios!
Nagios Remote Plugin Executor (NRPE) it will run as a service or daemon on the machines to be monitored and will be listening so that from Nagios, with the command 'check_nrpe', We make requests of you. In other future documents we will see other types of agents, Today it's time to talk (For me) of the best!
Installing check_nrpe,
We started by downloading and compiling 'check_nrpe', We previously installed the requirements, Here are the steps followed, At the end we move the binary to the path of the plugins and test it!
[SourceCode]
Yum Install -y GCC GLIBC GLIB-Common OpenSSL-Devel Perl WGET Git
cd /usr/src/
git clone https://github.com/NagiosEnterprises/nrpe
cd nrpe/
./Set
Make all
cp src/check_nrpe /usr/lib/nagios/plugins/
cd /usr/lib/nagios/plugins/
./check_nrpe[/SourceCode]
Installing the Agent,
GOOD, for this we will use NSClient++, the downloaded from their website, and in principle we will use the latest version, in this example we will use the Windows x64 binary.
We begin the installation of NSClient, “Next”,
We select 'Generic', “Next”,
Let's look at the option “Custom”,
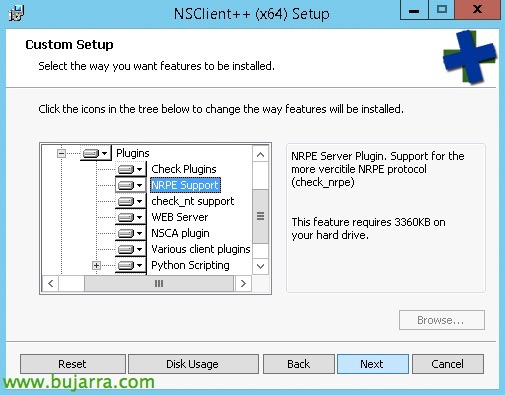
And we select the plugins that interest us, I'll mark them all, Why I'll use them in other examples, in this case, marking NRPE Support would be enough.
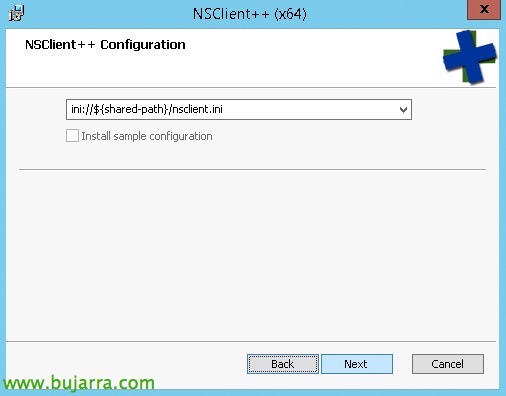
It tells us the INI file that we will use to apply the configuration, “Next”,
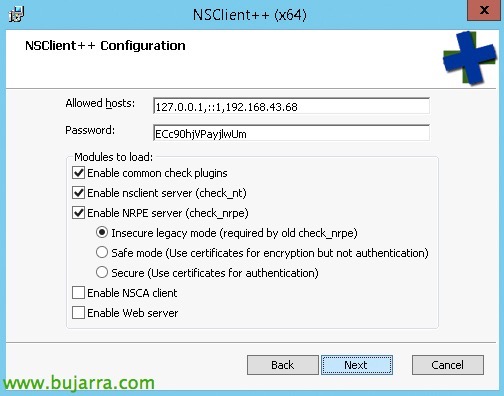
We will need to add the IP address of the Nagios or Centreon machine that will execute the queries, as well as enable check_nt if we are interested, which I am sure to do, you'll see =), we also select the NRPE safety mode, in this case I will not use a password when using Insecure mode, in a corporate environment, at least we will select a safe mode. “Next”,
GOOD, Pressed “Install” to install this little agent…
… Wait a few seconds…
And that's it, “Finish”.
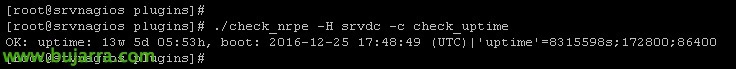
All that remains is to run a command from our Nagios team to test if there is connectivity, A very simple example would be the following:
[SourceCode]
./check_nrpe -H IP_EQUIPO_REMOTO -C check_uptime
[/SourceCode]
If we see that it connects and tells us how long that machine has been on, We can start!! Now all that's left is to feed Windows or Linux machines with scripts and execute whatever we want remotely, In future documents I will give interesting examples, But we'll need to follow this document first.
Create the Command in Centreon,
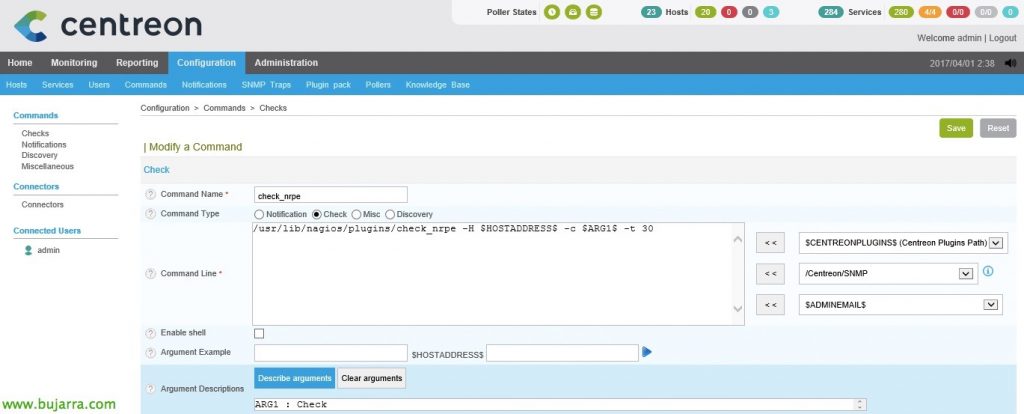
It would therefore remain to register the Command that we will use when we create the Services that we are interested in that monitor remote computers. We're going to “Configuration” > “Commands” > “Add” and create the following command:
- Command Name: We give the command a name, To associate it, it is best to put it the same as the name of the script it executes., in this case 'check_nrpe'.
- Command Type: Select 'Check'.
- Command Line: As usual, we indicate what Centreon or Nagios will actually execute when you call this command, it would look something like: '/usr/lib/nagios/plugins/check_nrpe -H IP_EQUIPO_REMOTO -c $ARG 1$ -t 30'.
In this case, If we look at, I add a timeout to the command at the end of 30 Seconds, since perhaps some commands that we execute remotely will take a while, won't? Well, each one as they want, Click on “Describe Arguments” and we defined the argument that we put in place so that when we create the Service we remember what needs to be filled in; which will be the check/command that we define in the nsclient.ini. We will see examples in future documents.
Example of a script in nsclient.ini
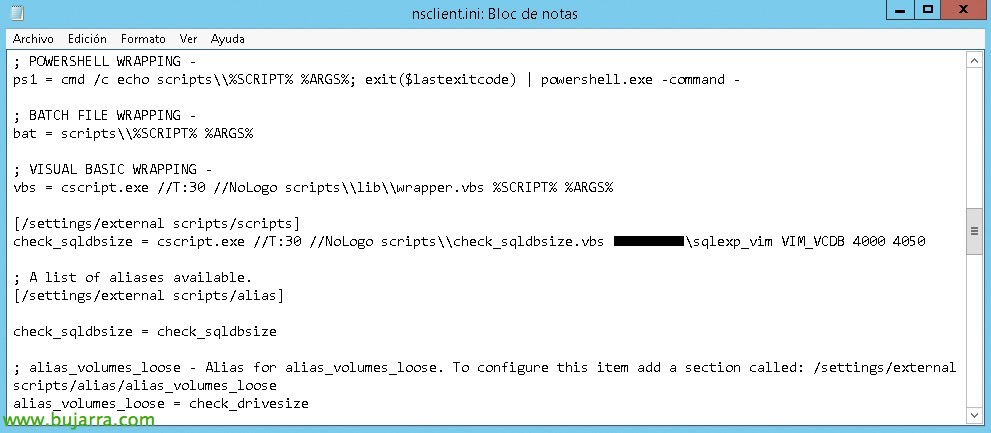
The operation would be as follows, on the remote machine where we installed the NSClient, We will have the configuration file 'nsclient.ini', That we will have to go (i) adding the scripts that it will execute, and (Ii) adding the aliases that reference the script. Example:
[SourceCode]
[/settings/external scripts/scripts]
comando_bat = scripts\archivo.bat
[/settings/external scripts/alias]
alias_bat = comando_bat
[/SourceCode]
Last, we must copy the PowerShell script, vbScript, Java, batch… that we have to the 'scripts' folder’ by NSClient. Every time we modify the configuration file 'nsclient.ini’ we will have to restart the Windows service “NSClient++” to reload the config and we can call this script from the remote Nagios, in the example above with:
[SourceCode]
./check_nrpe -H IP_EQUIPO_REMOTO -C alias_bat
[/SourceCode]
Use of arguments,
Let us imagine then, that what we are going to execute, the script on the Windows/Linux side, requires arguments, and we want to pass them on to you from the Nagios machine. As an easy-to-understand example, We think of a script that monitors backups, Ok? Either by PowerShell or whatever. And to this script I will pass as an argument the name of the backup task, Yes? If I want to, avoid defining it 5 times in the INI (Since I have 5 Backup Tasks), I will pass on to you from Nagios/Centreon the argument directly from Job. Here is an example of the necessary configuration in the 'nsclient.ini', First we will enable local and external arguments to be passed to it and then we define the command that it will execute followed by the arguments it expects (in the example a PowerShell script):
[SourceCode]
[/settings/NRPE/server]
allow arguments=true
[/settings/external scripts]
allow arguments=true
[/settings/external scripts/scripts]
check_copias = cmd /c echo scripts\check_copias_seguridad.ps1 $ARG$1 $ARG$2; exit($lastexitcode) | powershell.exe -command –
[/settings/external scripts/alias]
alias_copias = check_copias
[/SourceCode]
And then we can from the Nagios machine execute a command by passing arguments to it, which we will later define from Centreon with GUI in a more comfortable way:
[SourceCode]
./check_nrpe -H IP_EQUIPO_REMOTO -c alias_copias -a "primer argumento" "segundo argumento"
[/SourceCode]
What I said, we will see in future documents practical examples of the use of NRPE, How with some scripts we can get the most out of all the information that interests us. Many times we will have to make our own scripts, And why not? If we transfer all our needs to Nagios, we will control them and we will be able to rest much more peacefully with our organization fully monitored!