Mounting DirectAccess on Windows 2012
Road to the VMware Partner Exchange event & Forum, In my dear Termibus, I wanted to share with you my first tests with DirectAccess, which is already a technology that came out in 2008 R2, but in 2012 have simplified their assembly as well as their requirements. DirectAccess will allow the secure connection of our client computers to our organization without the need to use tedious VPN's, We will configure a server that will be the one that will connect us securely to any resource on the internal network.
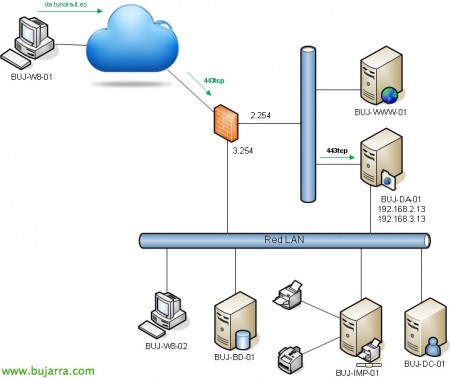
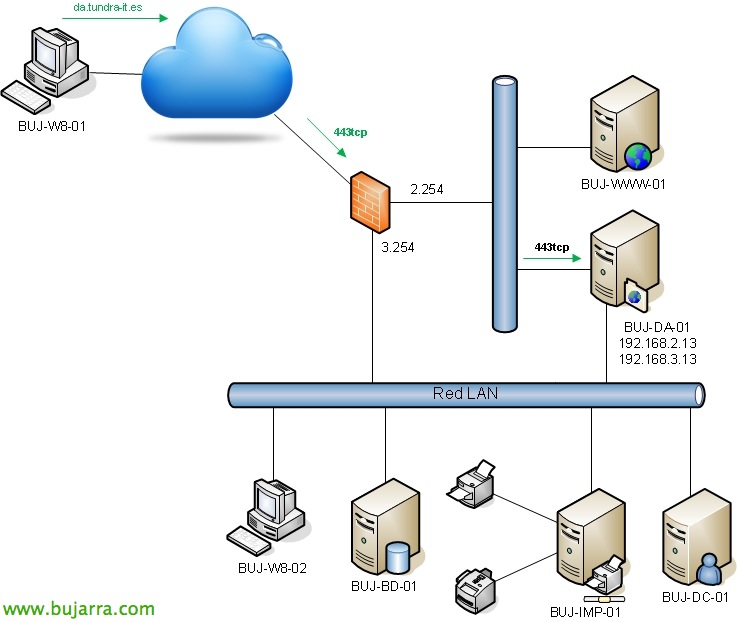
Well, This would be the network schema on which this document is based, we will deploy a DirectAccess server in the DMZ with a leg also on the LAN, Additional data:
DMZ Network: 192.168.2.x/24
Lan: 192.168.3.x/24
Internal Dominance: tundra-it.com
FQDN DirectAccess: da.tundra-it.es
BUJ-DC-01 (192.168.3.1): DC, Internal DNS, AC, Files, Printers…
BUJ-DA-01 (192.168.3.13, 192.168.2.13): DirectAccess, 2 NIC's (one in DMZ, one in LAN)
AD Computer Group with DirectAccess Access Permission: DirectAccess Computers (Windows members 8 of the organization we are interested in).
BUJ-DNS-01: It will be an external DNS server that I will use to create the Type A record for the DA site's public name.
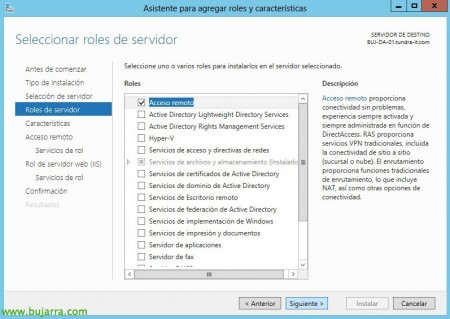
We open the wizard to add roles and features, We'll start by adding the server role “Remote Access”,
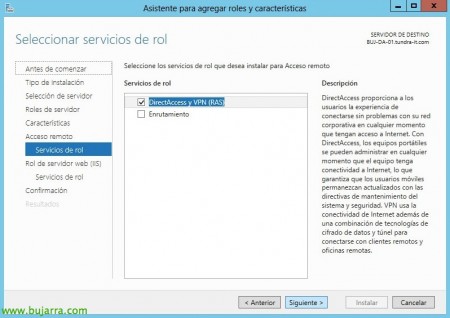
In role services we will only dial “DirectAccess and VPN (EVENNESS)”, Click on “Following” to be installed
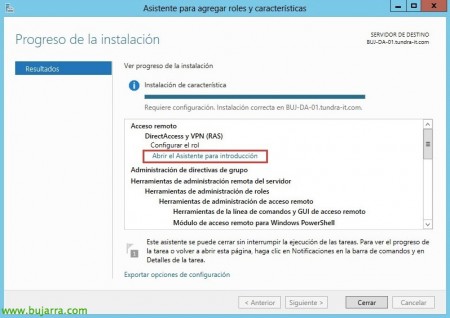
Once installed, We open the “Getting Started Wizard” and we'll set up DirectAccess,
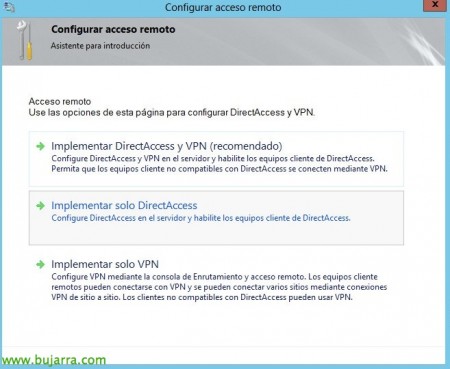
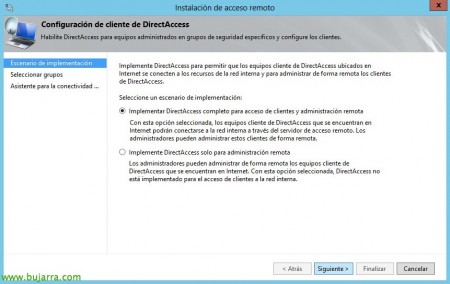
The introduction wizard will appear, Click on “Deploy DirectAccess only”,
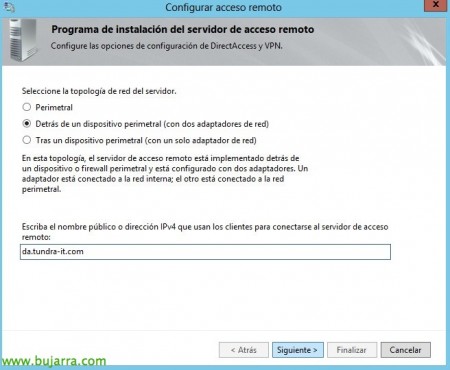
In this scenario we have the DirectAccess server with two NICs, one on the DMZ and the other on the LAN, So we press “Behind an Edge Device (with two network adapters). “Following”,
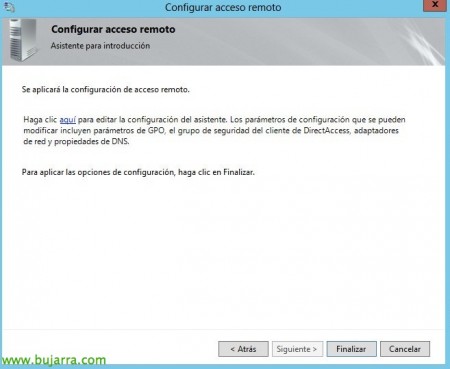
And click on the link “here” To edit the default settings.
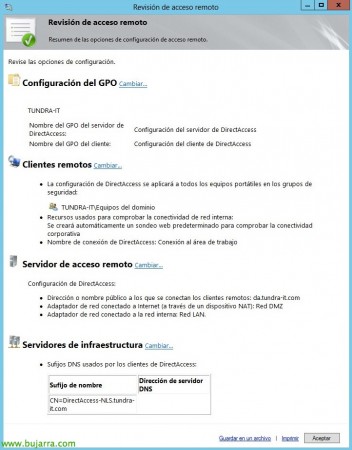
We can accept the default configuration or then configure each element of the infrastructure. Can: Rename the GPO's that will be created, Configure options for remote clients, those of the remote access server, those of infrastructure servers or application servers.
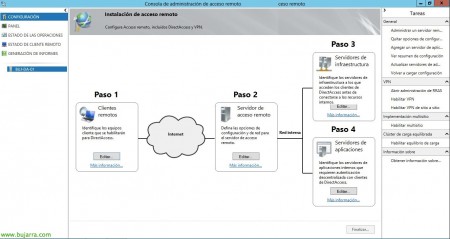
This would be the overview of the configuration to be carried out,
We edit the Step 1, DirectAccess client settings, Mark “Deploy full DirectAccess for client access and remote management”, “Following”,
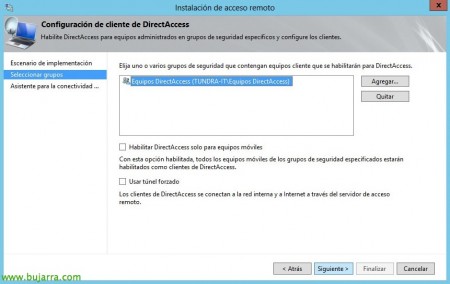
Select the group of teams that we have previously created and uncheck “Enable DirectAccess for mobile computers only” and “Use forced tunneling”, “Following”,
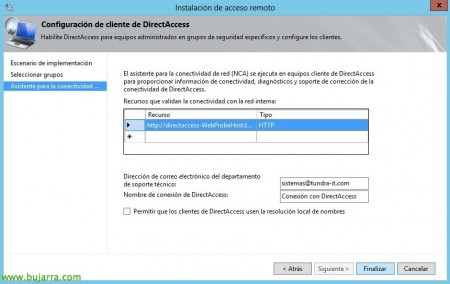
We leave the host that creates us by default to distinguish later on the clients if we are connected to the LAN 0 to an external network. By default, it will create a record in the DNS with the entry: directaccess-webprobehost.domain.local and will test your connection with HTTP; we can add another network equipment with PING additionally. We will provide users with an email from technical support, as well as the name of the network that will be created on the client PCs; Optionally we can “Allow DirectAccess clients to use local name resolution”, “End”,
In El Paso 2, in “Remote Access Server”, we will indicate the public name or IPv4 of our site where the equipment will be connected, “Following”,
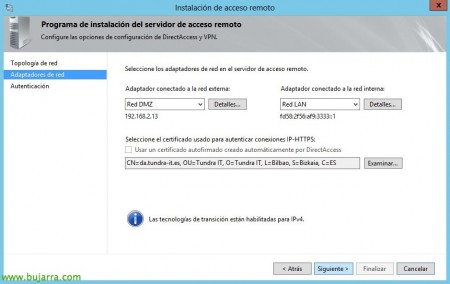
We indicate that the adapter connected to the external network is the one from the DMZ network and the adapter from the internal network is the adapter from the LAN network, in addition, we must have previously generated a certificate in our internal CA (or public) for the 'da.tundra-it.es' site, we select it & “Following”,
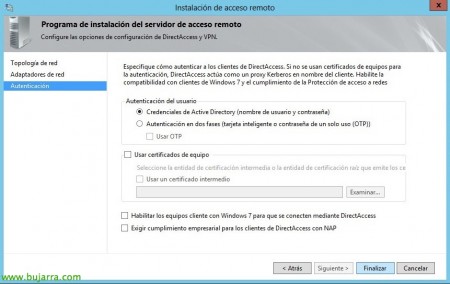
For now, to validate my Windows computers 8 It's enough for me to mark “Active Directory credentials (Username and password)”, in future documents we will see additional authentication methods with certificates and we will also give access to Windows computers 7. If we have NAP configured, We may require your compliance in order to allow the connection to the clients. “End”,
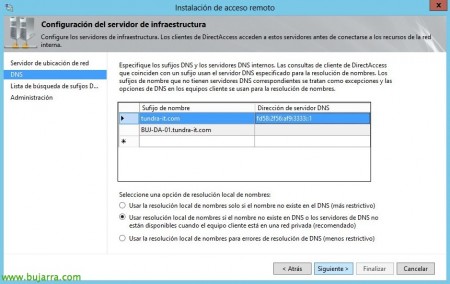
In El Paso 3, “Infrastructure Servers” We will indicate where we have the network location server (NLS), In this case “The Network Location Server is deployed to the Remote Access Server”, we must have previously generated a Computer certificate for the DirectAccess server, “Following”,
We indicate the DNS names and servers for the DNS suffixes of the internal network and leave them by default “Use local name resolution if the name doesn't exist in DNS or DNS servers aren't available”. “Following”,
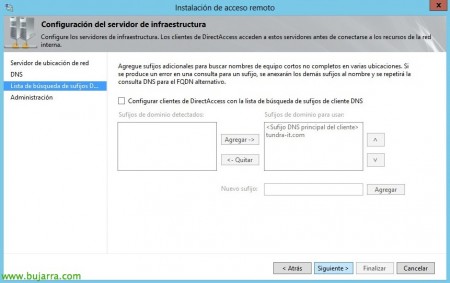
We will be able to add additional DNS suffixes for other internal ones, “Following”,
If we have patch or update servers, we can add them for client management, “End”,
And finally, in El Paso 4, we will be able to extend authentication between DA clients and internal app servers.
We must save and Apply the configuration so that the GPO's are created and the DirectAccess clients are automatically configured.
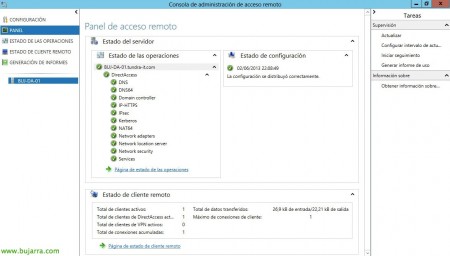
In the Dashboard we will see the status summary, where we will see if we have any problems both with configuration and some type of connectivity, we will also see the connected clients or those that fail to connect, We will also be able to get some fairly complete reports as well as obtain a lot of registration information in case of need.
It will be enough to prove it, First verify that the policies have been applied to us in a client ('gpupdate /force’ & 'gpresult /R'), Remove the equipment from the corporate network, take it to an external network and see that it can't connect to WebProbe's HTTP machine to lift the DirectAccess connection by connecting to the public name over HTTPS, We confirm that the connection is correct, from a PowerShell we run 'Get-DAConnectionStatus’ and we'll see if everything is OK, in addition to seeing it in the Networks panel. We open a browser for example and confirm that we can access the organization's resources!!!