Earning an A+ in SSLABS on published sites with NetScaler
This post will be very useful if we have any service published with NetScaler, from the Gateway itself, to a Content Switch that we have, for example, The issue will be to raise the level of encryption required while avoiding possible vulnerable old ciphers.
For a long time we have known and I give you the fun with the wonderful website of SSL Labs, a website that will verify any service we have published with a certificate and therefore we think it is safe. SSL Labs will show us the colors and indicate possible security flaws. The question will be to listen to it and not use ciphers that are not secure today.
We start, If we're going to “Traffic Management” > “SSL” > “Cipher Groups” and we create from “Add” A new cipher group, where we will add the latest encryptions and of course we will remove access to old machines that do not support them, such as Windows 7. We give it a name and add the following ciphers:
- TLS1.2-ECDHE-RSA-AES128-GCM-SHA256
- TLS1.2-ECDHE-RSA-AES256-GCM-SHA384
- TLS1.2-ECDHE-ECDSA-AES128-GCM-SHA256
- TLS1.2-ECDHE-ECDSA-AES256-GCM-SHA384
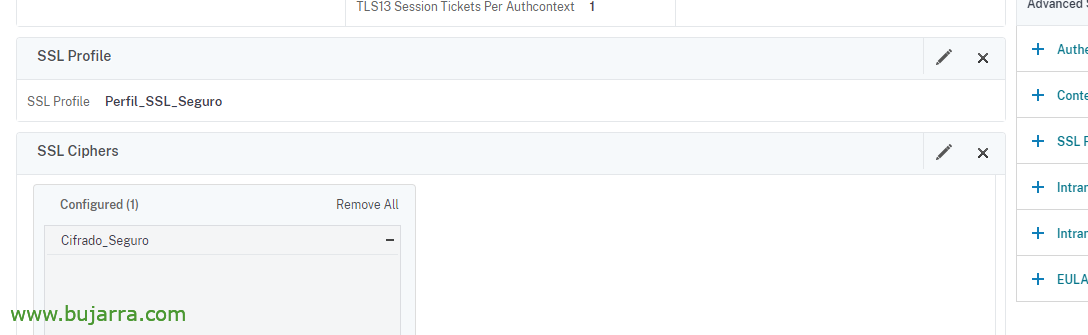
Now, we will create an SSL Profile, since “System” > “Profiles” > “SSL Profile”. And we set up:
- We give you a name.
- In 'Deny SSL Renegotiation’ we tick 'NONSECURE'.
- We check 'HSTS' and indicate 'Max Age'’ to '15552000’
- In 'Protocol’ uncheck 'SSLv3', 'TLSv1', and 'TLSv11'. At least we'll leave 'TLSv12'.
And then it would be a matter of associating the Encryption Group and the SSL Profile in the virtual servers that we have, Be a GSLB, Content Switching, a Gateway…
Ideally, you should do a test before and after modifying in the NetScaler, remember later if everything went well, Save the settings. So, we can clear the cache in SSL Labs and try again, If everything has gone well, we will have the highest safety note, Now our secure channel will be using higher levels of encryption.