Getting passwords with PWDUMP and L0phtcrack
This tutorial explains how to guess user passwords on a remote computer, in this case I'm going to get the user passwords out of a Windows domain controller 2003, it would be the same for a Windows 2000, and it doesn't have to be a domain controller, it can be a Windows XP and it would not have to be a remote PC or server, If not local.

The first thing is to validate ourselves against the remote server as an administrator, Yes, We need to know the password of a user with administrator privileges on the remote host, That is why this document explains how to get the other passwords of the users knowing that of an administrator. From MSDOS, We authenticate with administrator privileges on the remote host, in my case it is a domain controller:
“net use SERVIDOR_DESTINIOadmin$ /u:DOMAINUSER PASSWORD”

Now, we downloaded the PWDUMP to our PC, Any version would work from PWBoOn3, Up to the pwdump6 (HERE PWBoS6-1.5.0); we uncompress it for example in C:pwdump, we enter through MSDOS to that directory, We run the program to export the users and the hashes of their passwords to a file, Run:
“pwdump SERVIDOR_DESTINO > FICHERO_DE_CLAVES”

Now we open the L0phcrack or LC, in my case, I will use LC5 or L0phtcrack version 5. The first thing is to create a new session so that we can then import the key file and burst it.

Once we have a session, We have to import the file that we have generated with the PWDUMP, To do this, click on “Import”

And in “Import from file” Indicate “From PWDUMP file” and in “Filename” we look for the previously generated file, Click on “OK”

We will see the list of users, Now we have to customize this session a little with the options that interest us. We will see which users have a password less than 8 characters and you want don't have a password. Well, we customize the session from “Session” > “Session Options…”

We have several options to customize the way we will try to break these passwords. We can enable “Dictionary Crack” to crack passwords with dictionaries in languages, or make hybrid attacks to mix the words X characters; and the type of characters you'll use in brute force… we configure as we wish and “OK”.

And now simply, We click to start with the play button “Begin Audit” and start pulling out the passwords.
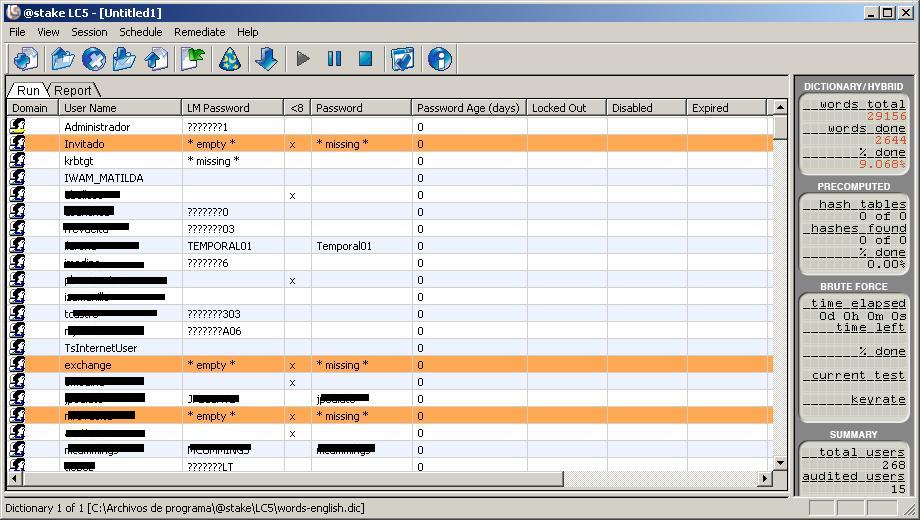
It will take a long time, depending on the CPU we have, if possible, we do this from a powerful PC, Ideally, a server with a couple of nice CPU's, and it will show us the passwords of the users as they get them. The process can take from a few minutes, up to more than a couple of days, It will all depend on the complexity of the passwords, the features from where we are running the LC, and the session options we've set up.