Gophish – Ethical phishing in our company
Today we are going to see a very complete and simple tool at the same time, An open source tool that will help us carry out security awareness exercises in our organization. We will do internal phishing, A simulation that will help us to know the level of our beloved users.
We can conduct a security awareness exercise within our company by conducting ethical phishing drills, in order to assess the readiness of our users and improve weaknesses. Of course, always with permission and legally.
You will see how in less than 15 minutes we can have everything ready, we will use Gophish that will give us everything to perform the test. Not only from the sending of the emails, but we will have a very complete console: We will see statistics, Who received the email, Who opened it, who clicked on the fraudulent link and even if they entered the credentials (if we want), We could see them.
So before we go any further, If you're a person who's going to use this to do evil, Please, Don't do it, We don't need people like you on this planet. Really, Make it look at you, You may have a psychological problem and it is best to contact a professional.
This guide is aimed solely and exclusively for us to internally carry out the tests that help us improve the security of our companies. The end.
There are several ways to deploy Gophish, in this post we will see how to deploy it with Docker, so in 2 minutes will be ready. We download the container image with:
Sudo Docker Pull Gophish/Gophish
And we directly started the Gophish container:
sudo docker run --name gophish -p 3333:3333 -p 82:80 -d gophish/gophish
In the previous command we see 2 harbours, the 3333 will be used by Gophish as an admin console, From there we admins can define the phishing campaigns. And additionally, In the 80tcp (that I map it to myself in the 82tcp) Gophish will serve fraudulent websites that we want to simulate through this port, go, where the user will arrive by clicking on the link.
Important, In the container logs we will see the password of the user 'admin’ what will be the one with which we enter to manage Gophish, so we consulted her:
sudo docker logs gophish -f ... time="2023-09-28S20:53:10Z" level=info msg="Please login with the username admin and the password af5cj3ccd1e705e8" time="2023-09-28S20:53:10Z" level=info msg="Creating new self-signed certificates for administration interface" time="2023-09-28S20:53:10Z" level=info msg="Background Worker Started Successfully - Waiting for Campaigns" time="2023-09-28S20:53:10Z" level=info msg="Starting IMAP monitor manager" time="2023-09-28S20:53:10Z" level=info msg="Starting phishing server at http://0.0.0.0:80" time="2023-09-28S20:53:10Z" level=info msg="Starting new IMAP monitor for user admin" time="2023-09-28S20:53:10Z" level=info msg="TLS Certificate Generation complete" time="2023-09-28S20:53:10Z" level=info msg="Starting admin server at https://0.0.0.0:3333"
So you're done, We just have to enter HTTPS://DIRECCION_IP_DOCKER:3333 to access Gophish management,
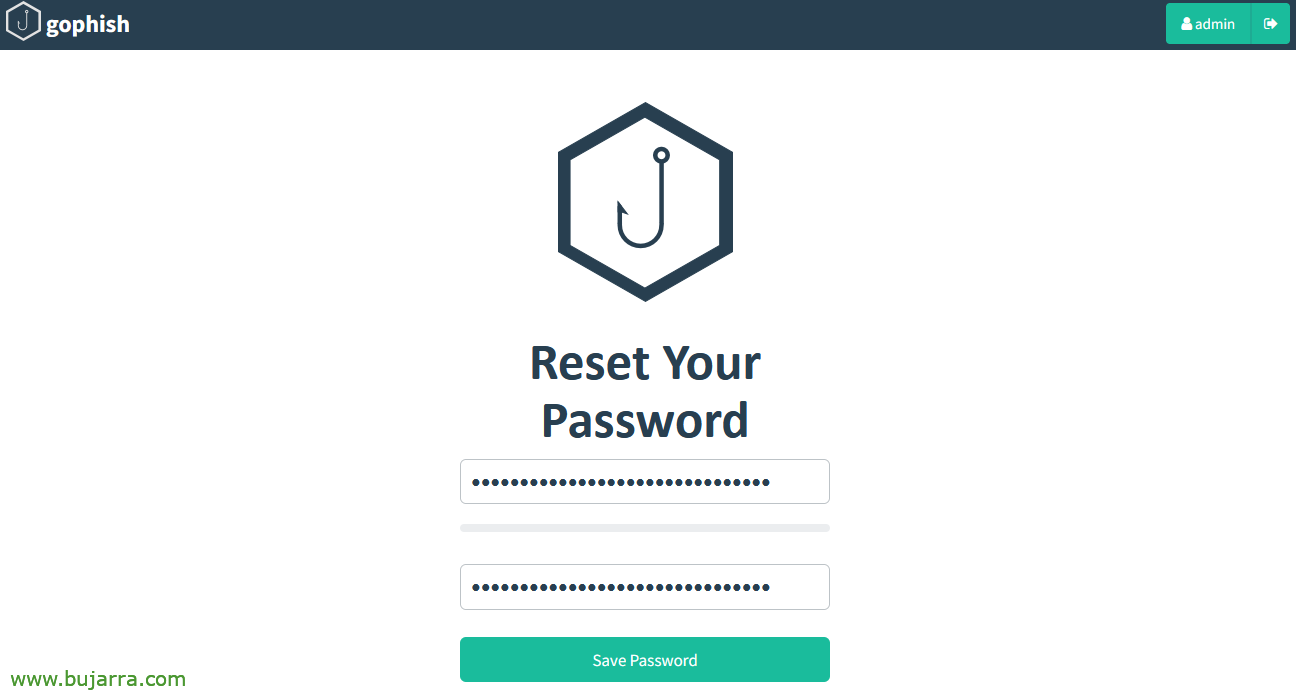
Let's log in once, It will force us to change the password of 'admin', We put whatever we want.
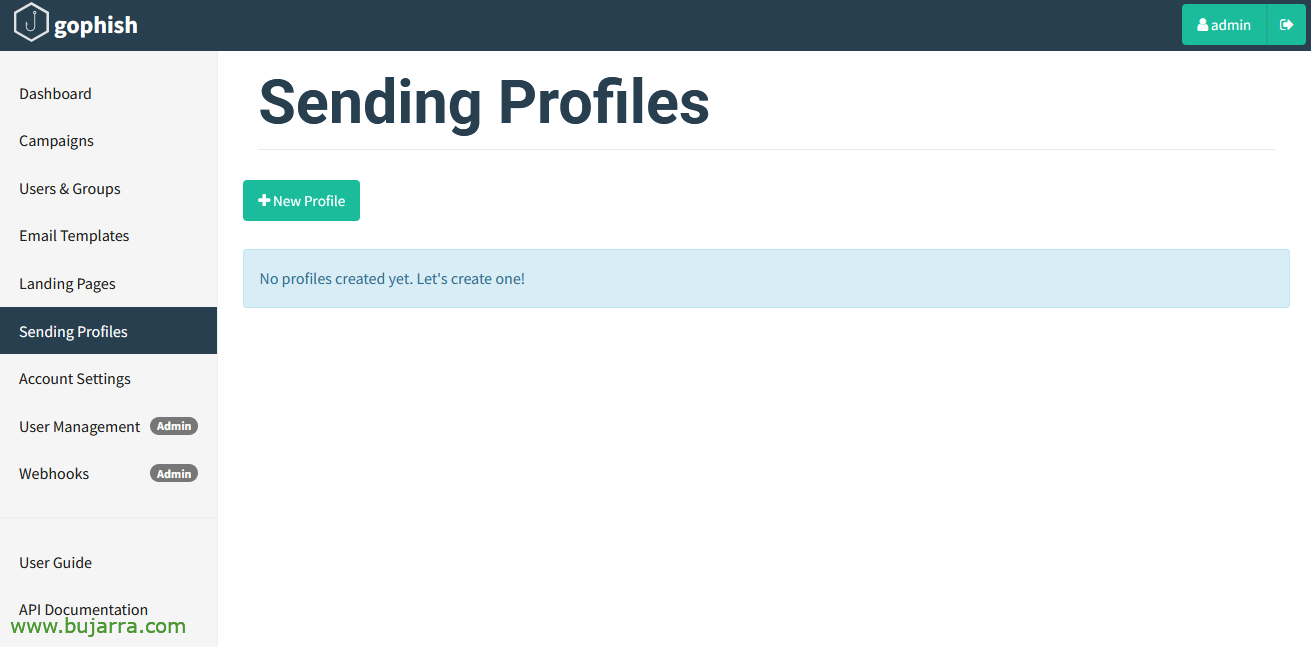
And let's start!!! We start first by setting up a shipping profile, This is, From which mail server will we send the emails?. So we click on “Sending Profiles” > “New Profile”,
So that we understand the exercise that we are going to do in the post, we are going to do ethical phishing against a company called Open Services IT (It's where I work), and I'm going to play dumb and assume that we DON'T have credentials from that company to send emails from @openservices.eus (that would be its public domain). So I set up another email, for example, a personal one that has nothing to do with it, We will use @bujarra.com, from here we will send the emails, But don't worry, users won't find out.
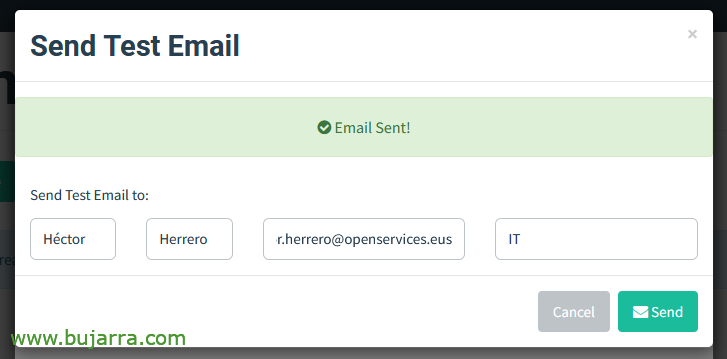
Fill in the email details and click on “Send Test Email” to validate it,
We send a test email, and we will see that we settle the part of the mail.
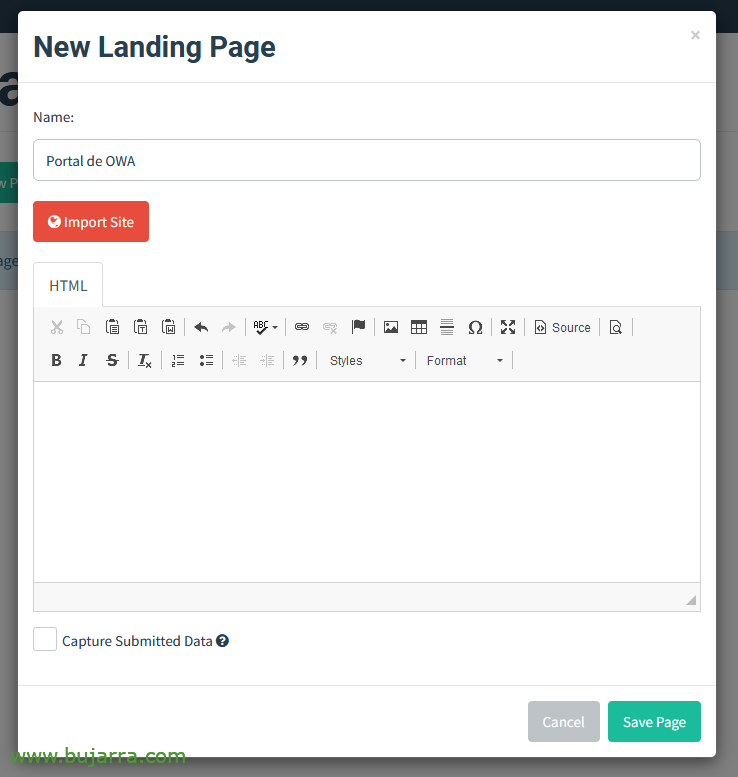
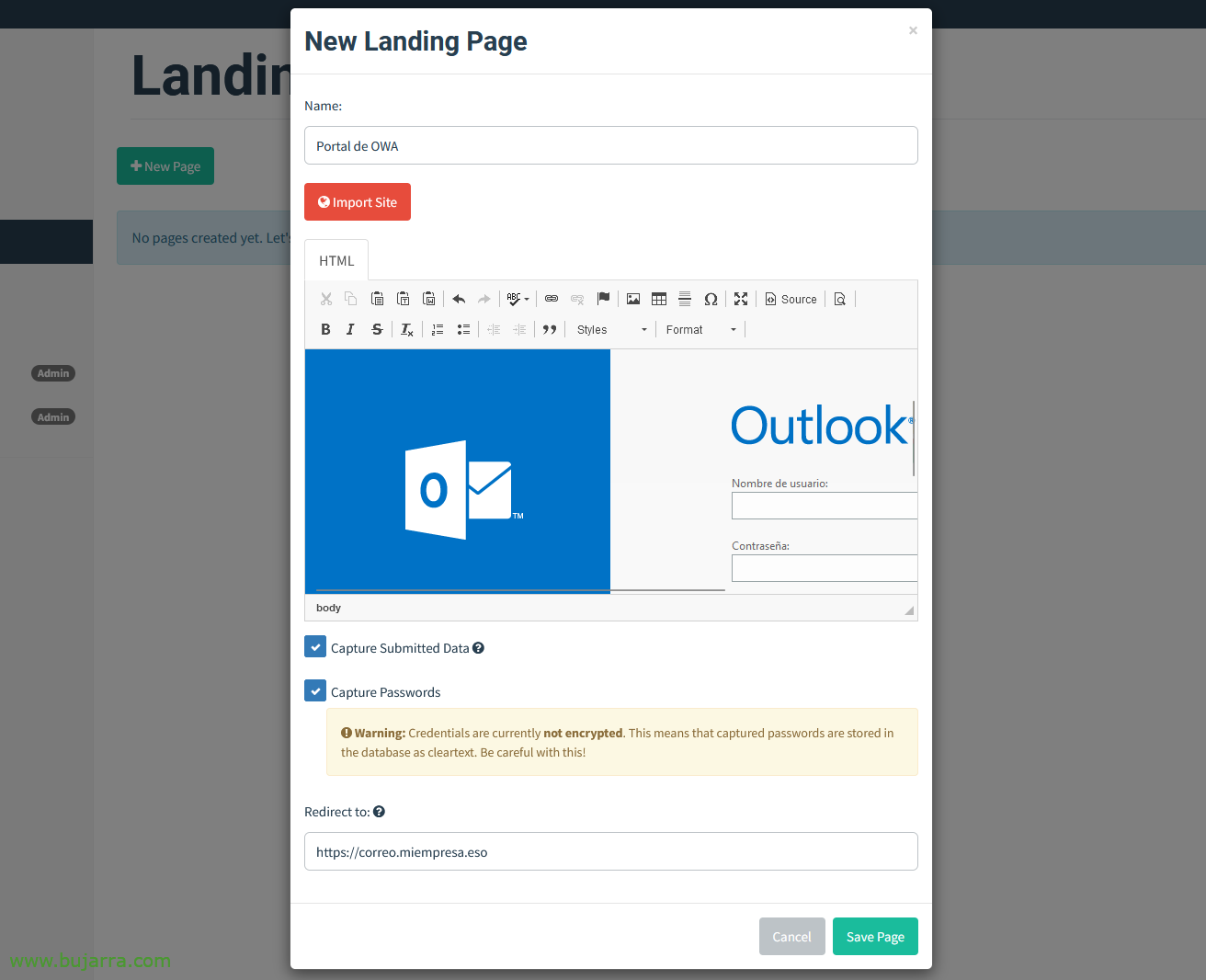
Next, we'll create the page where we'll take users; In the exercise we are doing I am going to simulate the company's email website, that we know uses Microsoft Exchange and has OWA, So this we'll create, We're going to “Landing pages” > “New Page”,
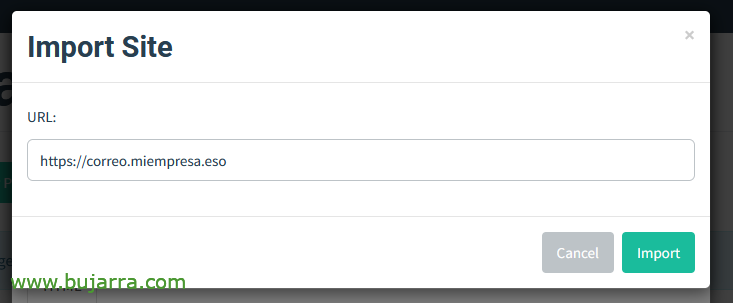
You're going to freak out, you will see how simple… We give it a name, e.g. 'OWA Portal'. But how do we duplicate the OWA website?? Very easy, give it to “Import Site”…
We put the URL of the site we want to copy/clone, this is the company's OWA and we click on “Import”,
Tachan!!! has copied the HTML code and left it exactly, The lemon pear… we can check both checks to capture any data they write, as well as the password if we were interested.
So this website will be the one that users are presented with and when they type in their credentials… Gophish will then redirect them to the right place. Users won't know what happened, if they have mistyped the password, if the browser refreshes… So in the “Redirect to” we will put the good URL, Where will they go next.
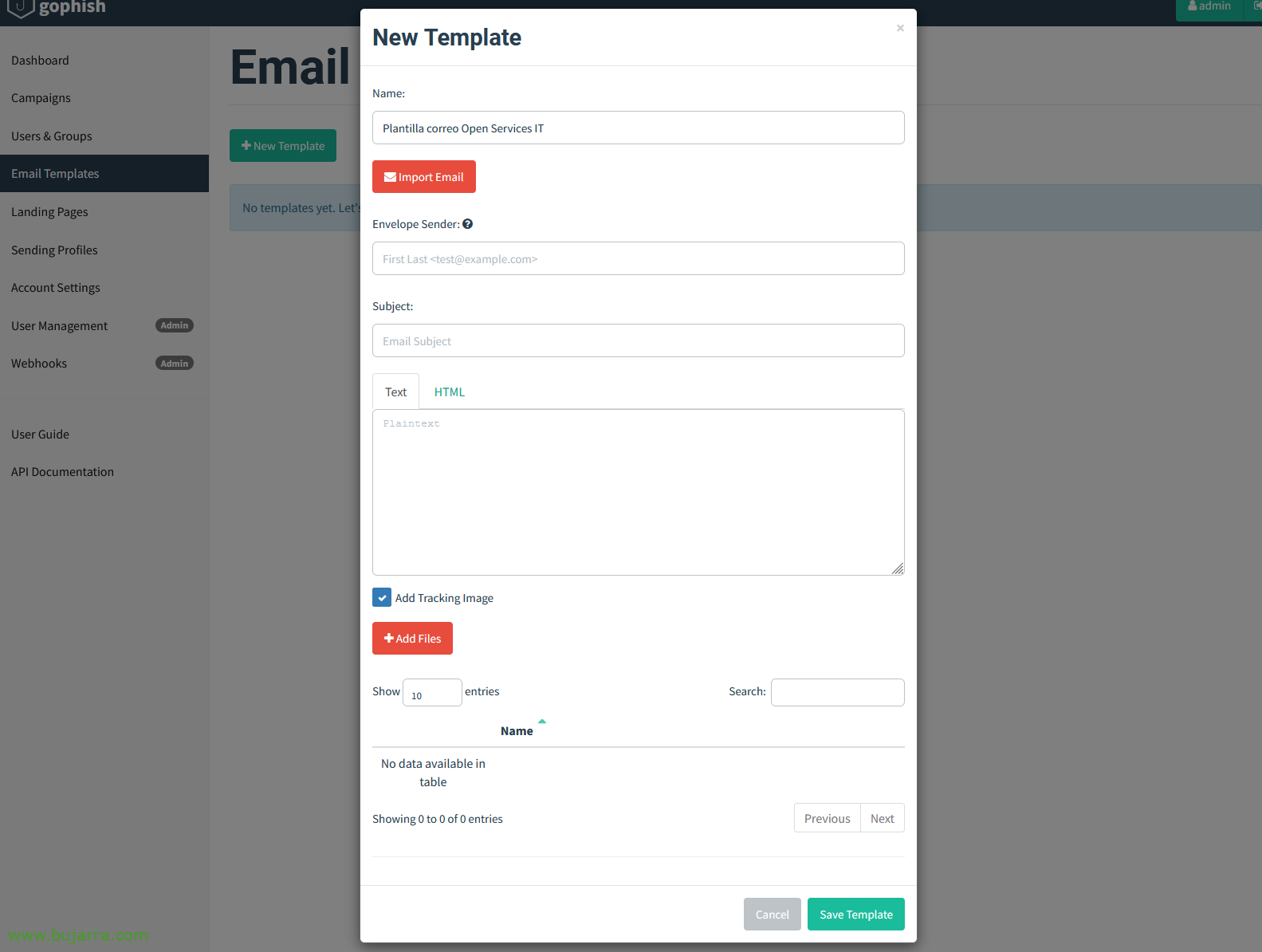
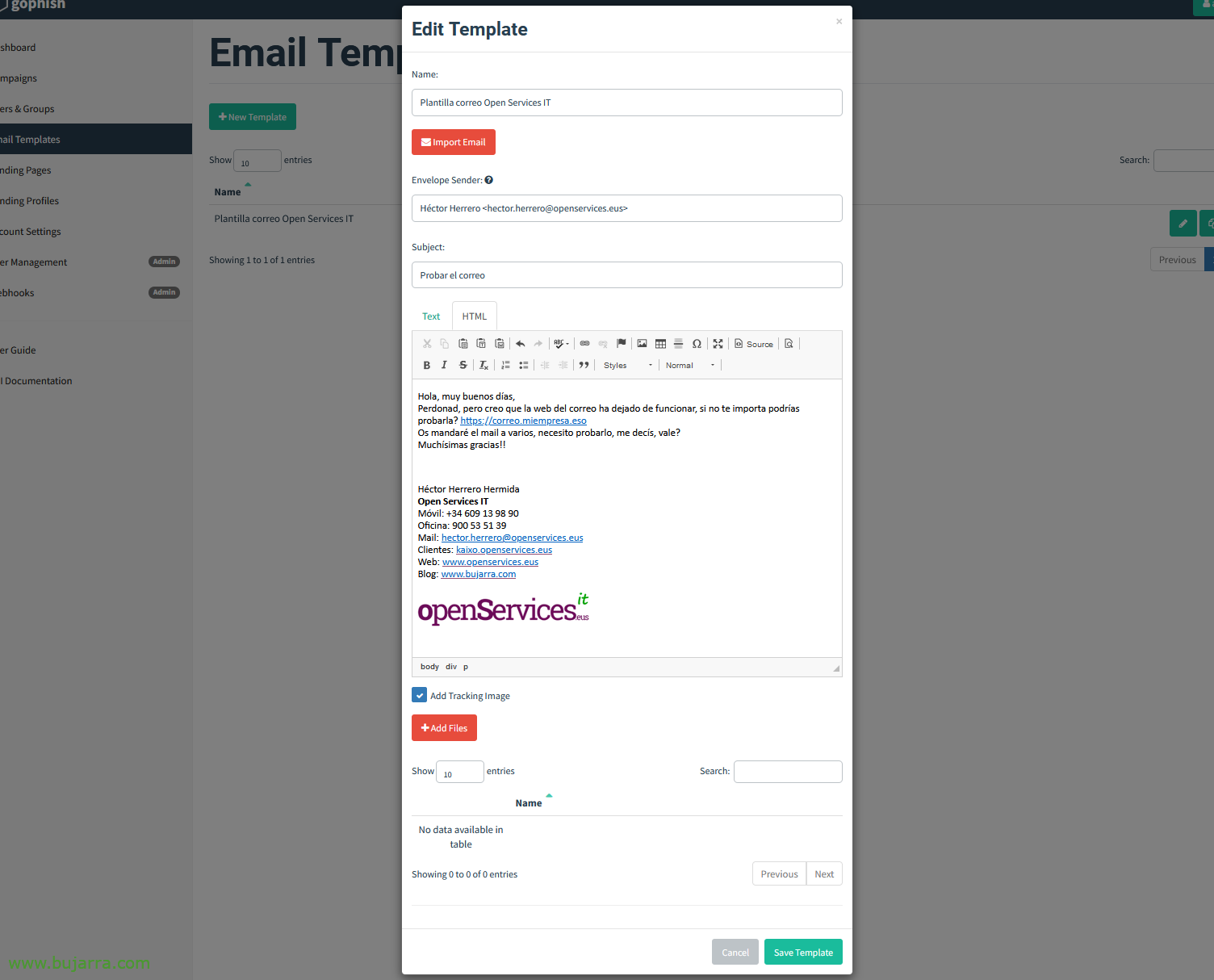
The next thing will be to create the email template, that is, what will be sent by email to users. With the company's format, fountain, signature… We're going to “Email Templates” > “New Template”,
We give you a name, e.g. 'Open Services IT Email Template', and to copy the same format as an email we have, click on “Import Email”,
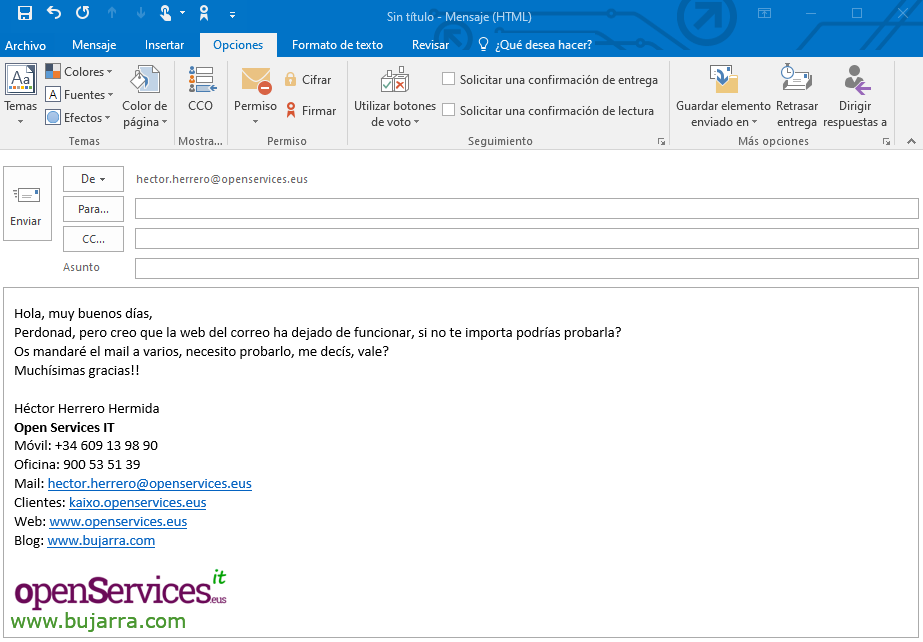
We take an email with the format that the company usually sends emails, we copy his signature, The logo… We can write a text now… save the email and copy the code in HTML format.
Total, that in the 'Import Email’ paste the HTML code that will have generated that template email, Click on “Import”,
Tachán again! We already have the email template that we are going to send, with a text a little like that so that users bite, I will give them confidence and ask them to try to enter the mail, I think it doesn't work. But of course it works!!!
We indicate a subject to the email and VERY important, in 'Envelope Sender’ We can falsify the sender's name and email, There, even if we send the email from @bujarra.com we can tell them that the sender is from @openservices.eus, and the user won't find out, Sailor fabric…
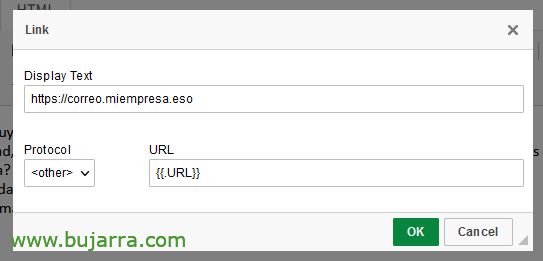
Total, in the email we put the corporate URL where they would have to click…
… and we created a link but to our Gophish site!!! For example, eh, in Protocol we put '<other>’ and in the URL we put the {{URL}}, so Gophish will put the malicious 😉 URL You have more variables in your Official Website in case you want to customize the email, and we name the user by name, etc…
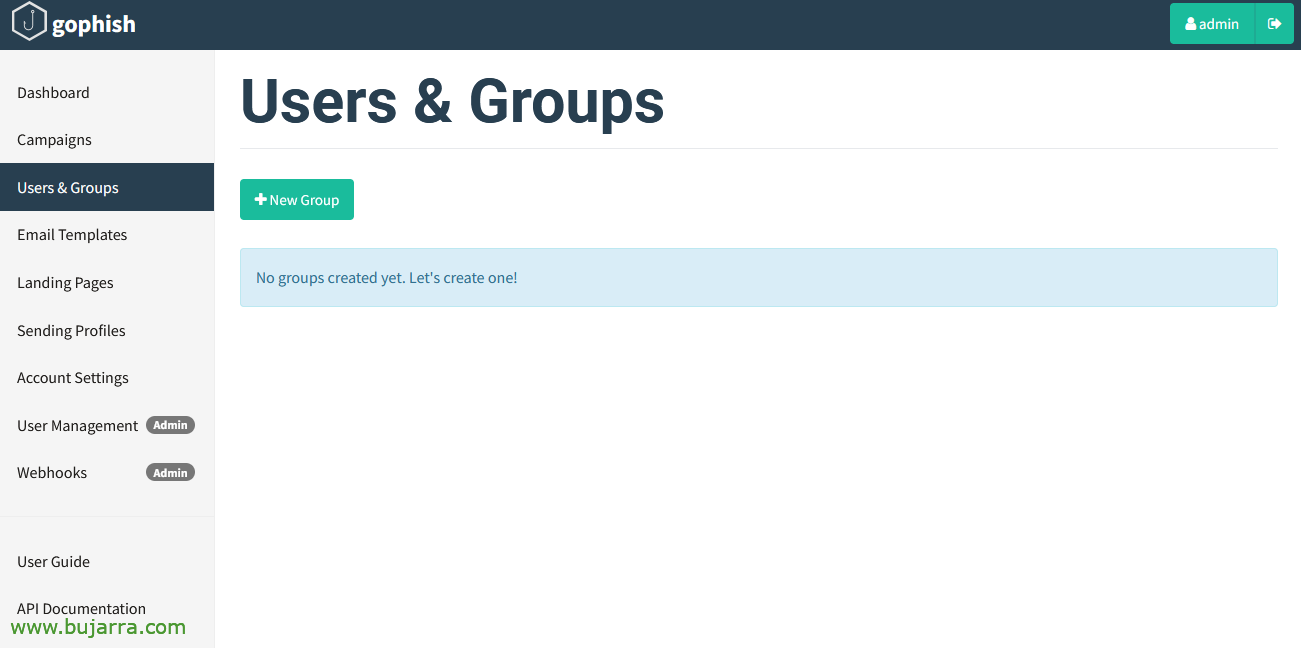
And nothing, Now we only have to say who we are going to send the emails to, in “Users & Groups” We will be able to register our first group and add several users to test it… Click on “New Group”,
We manually add users or import them from a CSV, We will send these users our first test. The name, surname, Mail or position are variables that you could play with if you are interested.
And we're ready to create our first campaign!!! “Campaigns” > “New Campaign”,
The campaign is nothing more than where we will put all the pieces of the puzzle together, where we will indicate the email template we are going to use, The website template we'll use, the URL is the URL of the Gophish web portal, In my case it is with port 82tcp, Default would be at 80TCP, and the most normal thing would be not to use internal IP addresses, if not an FQDN that resolves externally and internally. We indicate the release date and the email profile we will use. As well as which group we will send the Phishing to.. We give “Launch Campaign”…
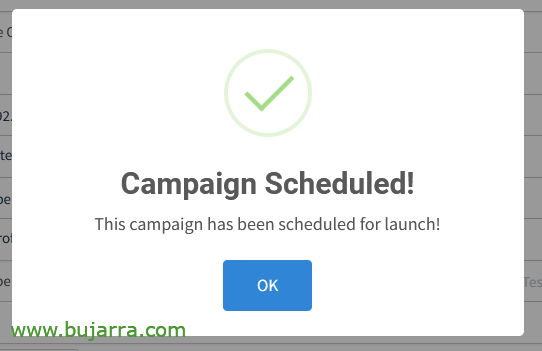
¡Yes! We are super safe, “Launch”,
And “OK”, Campaign launched!!! The engines were put into operation!! Now to wait for the results…
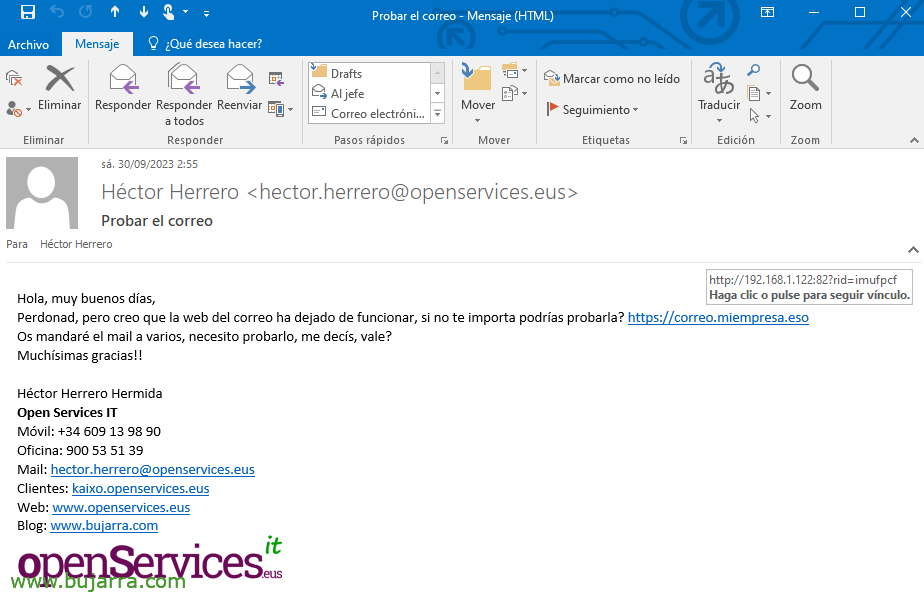
The user would receive this email, where it says that it comes from a person in the company (even if the mail server has nothing to do with it), with that text that if you look at the link no matter how much they read a text, the URL will be different…. And if they puncture…
If they click I'd take them here… look at the URL… Do you think users will notice? I don't know Rick… total, On top of that, they decide to put their credentials in…
Well… If they put in the credentials… it will redirect them to the corporate email website, And they won't have realized what happened… Tell… But I have already entered the credentials?? hey? and from here on we don't care… Look at the URL now they would be on the corporate site…
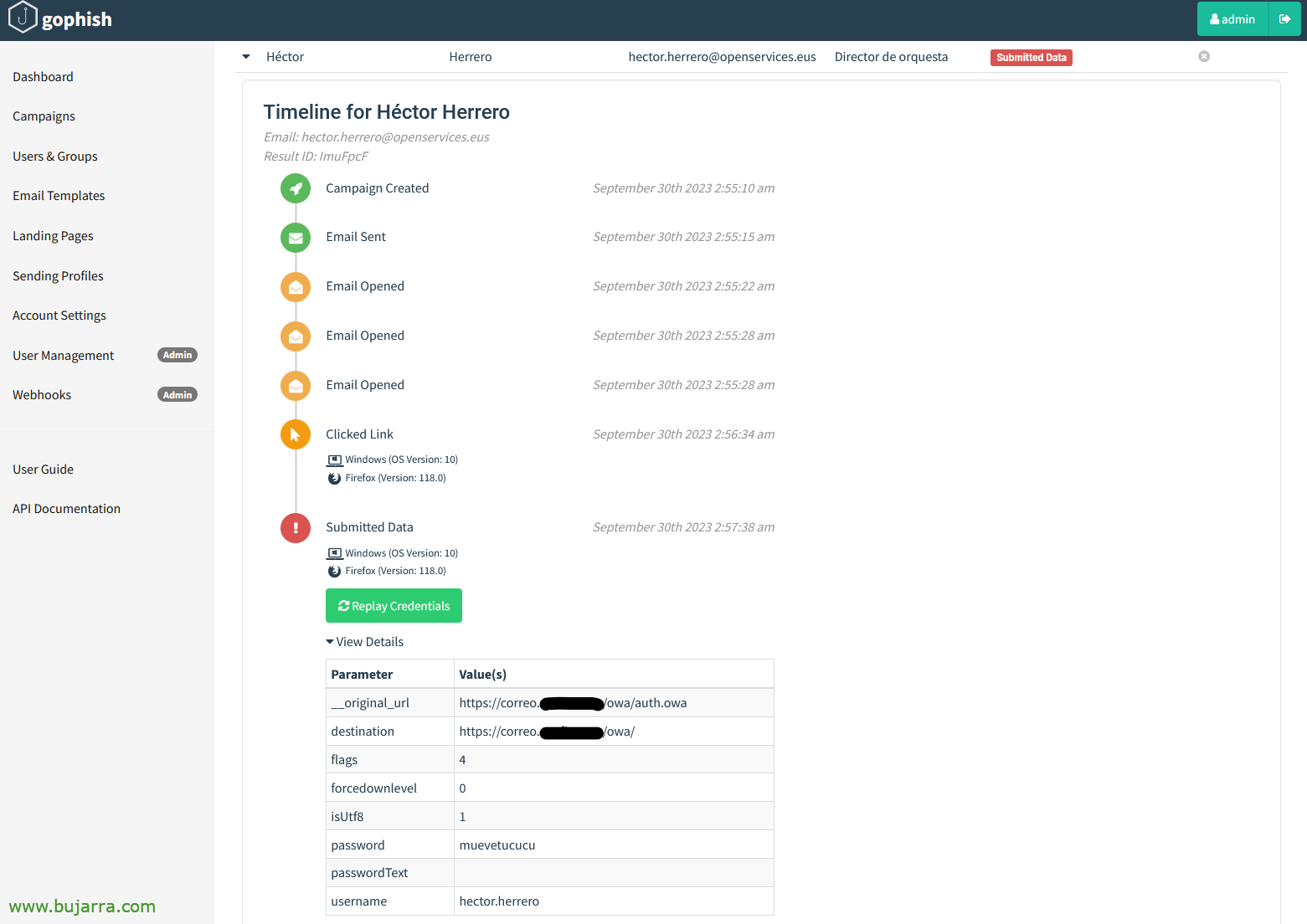
GOOD, And what would we see? Well, apart from a global summary in case we have launched several campaigns, We will also have a specific one for this drill. We can see how many emails have been sent, have been opened, Users have clicked on the link, Users who have submitted data… or even if someone noticed it and reported it as evil…
In the details we will be able to navigate through each user… and know what he did…. in this case the user received the email and after 3 times of seeing it it seems that he has made up his mind and has clicked on the link… and even worse… He has entered his credentials… Oh oh… User to re-education!!!
Well, You have seen how easy it is, simple and for the whole family we can implement a free and open source ethical phishing solution, with which we can also generate a report that we teach in management to promote training, The use of secure methodologies, etc…
As usual, I send you a hug, Have a VERY good week and as I said, Please, those who are going to use these tools fraudulently.. Let them educate you too!