Passing Crowdsec blocklists to our Fortigate firewall
Have I ever told you that Crowdsec is a marvel?? 😛 for any type of company… that will protect us from external or internal attacks! It's not a turkey snot.! Crowdsec teams will share a blacklist of IPs, So when a team is attacked, the rest will be protected. But it is also that, This blacklist can be sent to our perimeter firewall, so that he may protect us!
A blast…but to make a very quick remembering to those who have not yet read a Crowdsec post… Let's say it's an agent that is installed on Windows or Linux computers, which among other things will read logs of the services published by these machines and will know if it is being attacked, in view of this, it will take action, for example, adding a rule in the FW of the OS blocking that attacking IP address. The rest of the teams with Crowdsec, when sharing the blacklist they will also protect themselves by blocking that IP, Anticipating any attack, whether it's a local or public IP.
So in this post we will see how we can make our Perimeter Firewall, in this case a Fortigate can read this blacklist and protect the entire organization from above.
First things, on a machine with Crowdsec, where we can reach with the perimeter firewall, we must install the 'Blocklist Mirror', a service that will publish the block list via the web.
sudo apt install golang -y git clone https://github.com/crowdsecurity/cs-blocklist-mirror.git cd cs-blocklist-mirror/ make release cd crowdsec-blocklist-mirror-v*/ sudo ./install.sh
If we have the CrowdSec repository we could install/update it using apt or yum.
The first thing will be to configure Blocklist Mirror, We do this by editing '/etc/crowdsec/bouncers/crowdsec-blocklist-mirror.yaml'. We must indicate the URL of the server 'Local API', Normally these roles go on the same machine. And we indicate a port where we will publish the list, as well as indicating the firewall's IP address on trusted IPs so you can connect and read the list:
...
lapi_url: HTTP://127.0.0.1:8080/
...
listen_uri: 0.0.0.0:41412
...
trusted_ips: # IP ranges, or IPs which don't require auth to access this blocklist
- 127.0.0.1
- ::1
- 192.168.2.1
...
We enable and restart the service to load the new changes:
sudo systemctl enable crowdsec-blocklist-mirror sudo systemctl restart crowdsec-blocklist-mirror
And we can try to open the URL: HTTP://DIRECCION_IP:41412/security/blocklist if we also got into the whitelist! We verify that access is good, that we manually ban an IP address and the list is updated, or if it detects any attacks on other Crowdsec computers.
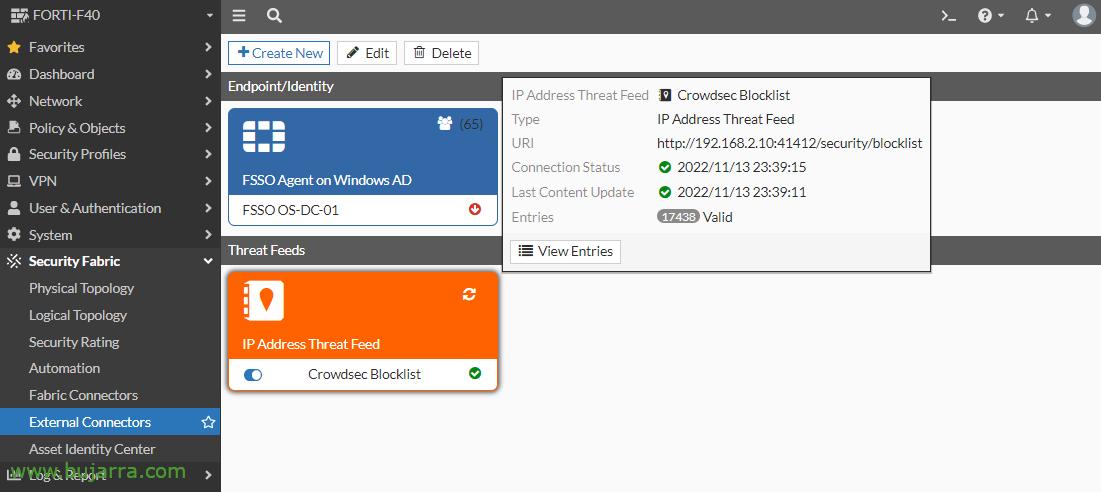
In our firewall we're going to “Security Fabric” > “Extenal Connectos” > “Create New”,
Select 'IP Address',
We give you a name and indicate the URL of the blocklist, and we specify the time to refresh the list, “OK”,
We can confirm that it is valid, Last update date…
Or if we click on 'View Entries'’ Confirm that it is correct,
And nothing, Now we should create rules in our firewall, where as Origin we indicate that it is the list of banned IPs that we have just created.
It is advisable in each interface to make rules for entering and exiting the destinations of the blocklists, denying access. Thus, in the event of a public attack, it will not be able to access internal remedies, or if it is an internal attack, will be isolated.
Eye, by doing this, remember that we have the possibility of being left out of the game, This is, if for whatever reason our team makes an attack, for example, attempts are made to validate incorrectly by SSH or RDP or CIFS or HTTP(s) or whatever to some team in the wrong way, On the 5th attempt (Default) will put us on that blacklist. So maybe it's interesting to put some IPs on Crowdsec whitelists, where the file '/etc/crowdsec/parsers/s02-enrich/whitelists.yaml’ Where we'll do it:
Name: crowdsecurity/whitelists description: "Whitelist events from private ipv4 addresses"
whitelist:
reason: "Private IPv4/IPv6 IP/Ranges"
IP:
- "127.0.0.1"
- "::1"
- "192.168.33.24" # Our cidr management machine:
#- "192.168.0.0/16"
#- "10.0.0.0/8"
#- "172.16.0.0/12"
# expression:
# - "'foo.com' in evt. Meta.source_ip.reverse"
I hope you found it interesting, we continue another day with more Crowdsec magic! You will see what an elegant way to protect our machines! I thank you for the Likes, Like, Retweets and weird stuff on social media,
Hugs!