Antivirus protection for our Nextcloud data
A fundamental thing in our IT lives is protection, try to secure our data as much as possible, No? In this post we will add one more layer of security to our Nextcloud environment, In a simple way, we will add antivirus protection to the files that are stored in our private cloud, We will prevent infected files from being uploaded!
How we'll do it? Very simple, Installing an antivirus, in this case ClamAV. We will do it on our Nextcloud machine and then by enabling an app that will show us reports or messages in a fully integrated way as soon as it detects a virus or any type of malware in users' documents. So they won't be able to upload infected files, since it will be analyzed at that time!
We proceed to install the ClamAV antivirus, we update the signature database and to finish, We start the services!
[SourceCode]sudo apt-get install clamav clamav-daemon
sudo freshclam
sudo /etc/init.d/clamav-daemon start
sudo /etc/init.d/clamav-freshclam start[/SourceCode]
To integrate the ClamAV antivirus with Nextcloud we will do it by downloading a small App that we will enable later:
[SourceCode]git clone https://github.com/nextcloud/files_antivirus.git
mv files_antivirus/ /var/www/nextcloud/apps/[/SourceCode]
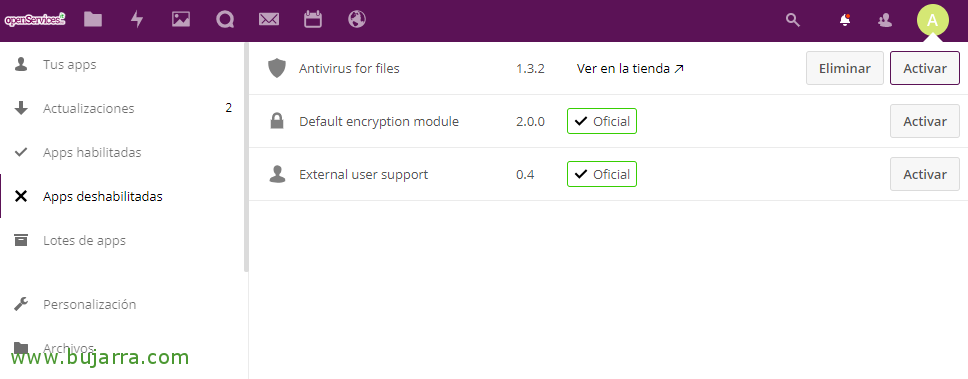
GOOD, it's time to log in as an administrator to Nextcloud and go to the “Apps”, From there we will see in “Disabled apps” that we have a new, we must Activate the 'Antivirus for files'.
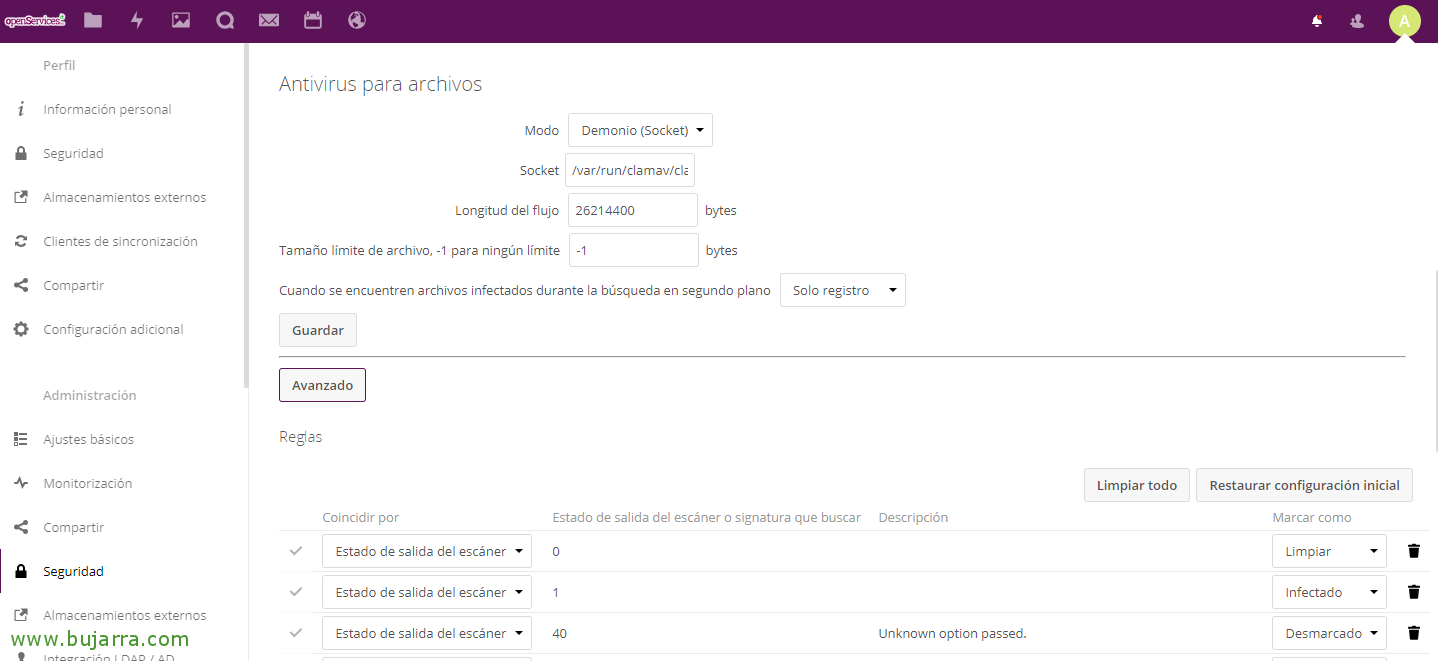
After enabling the antivirus app, from the “Configuration” > eyelash “Safety”, we will be able to configure the AV in the best way depending on our environment. We must specify the way in which it will work, Default “Demon (Socket)”, will run on the same Nextcloud server and ClamAV. If we have a high load of files/users, we can select the second option “Daemon” indicating the server where ClamAV runs. The last Mode would be “Executable”, something less recommended where the clamscan starts and stops with each file they upload.
We will also indicate the path of the Socket, If we don't know, We may run the following to locate it:
[SourceCode]netstat -a|Grep clam
unix 2 [ ACC ] LISTENING FLOW 2117964 /var/run/clamav/clamd.ctl[/SourceCode]
If you want more info visit the Web Configuration.
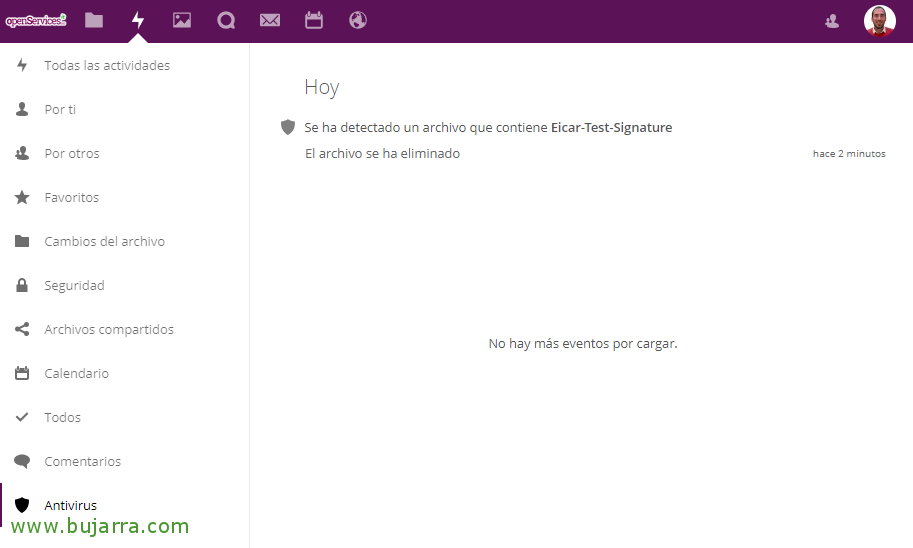
And with that everything would be ready! If you want to try uploading the typical Eicar example to see if it detects it! If you have followed all the steps correctly, you will be able to see how the antivirus detects them, it will not let you upload files and also in the Activity Panel, You will be able to see the incident log!