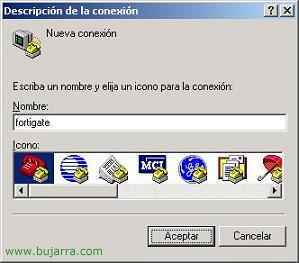
Active Directory Connector for Fortigate: FSAE – Fortinet Server Authentication Extension
If we want to integrate the firewall with our Active Directory (Active Directory – AD), so we don't always have to use local users, if not take advantage of those that the domain controllers database has, we'll use a tool called FSAE. This procedure explains, How to install the FSAE, How to configure domain controllers and firewall, Then we'll create a policy and they'll just browse the internet (or the rule that interests us) Active Directory Users.