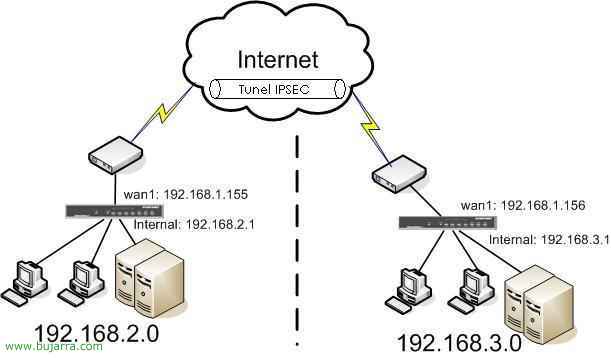
Connect iPhone or iPad to IPsec VPN with FortiGate
In this document, we'll look at the configurations needed to connect an iPad or iPhone device to a FortiGate IPsec VPN, with this we will be able to make the corporate applications of our iPad/iPhone work directly, ideal for putting on a softphone-type application and calling (or receive calls) directly from such devices, saving the costs of calls or being 100% Available,