Implementing Windows LAPS
Well, Today we come with a classic, a great tool that we have never talked about in the Blog, so in case anyone doesn't know her, we will implement Windows LAPS (Local Administrator Password Solution) in our organization. Which as its name suggests, help us manage local administrator accounts on the positions, member servers of our organization and even the DSRM password.
Maybe many of you know it or have installed it in its day, The truth is that it is very useful to centrally manage all these local administrator accounts, PCs or member servers. Microsoft has been integrating it into its own operating system for some time now, so you don't have to install anything separately. And that's what this post is about, how to enable the new Windows LAPS.
Before you begin, Let's take a moment to think, All this is very good, but… And what happens if our AD goes down?? and, If there is another CrowdStrike moment? Well, we may be left without access to any machine, Nor with the local accounts since we will not know them, So think about it, perhaps leaving some equipment unmanaged, etc…
If your Windows are up to date, they may already have the 'April patch' installed 2023 Cumulative Update’ (https://support.microsoft.com/help/5025221). Supports Windows Server 2019 and 2022 With the patches of the 11 April 2023 as well as in Windows 10 and 11 versions 21H2 and 22H2 with the 11 April 2023.
As we have mentioned, It would also be used to manage the password for Directory Services Restore Mode (DSRM o Directory Services Restore Mode). To encrypt this password we will need to have a functional level in the domain of 2016 at least. If our DCs are 2019 or 2022 we will be able to use all the features of Windows LAPS, and if our DCs are 2016 we will be able to encrypt passwords, except that of the DSRM.
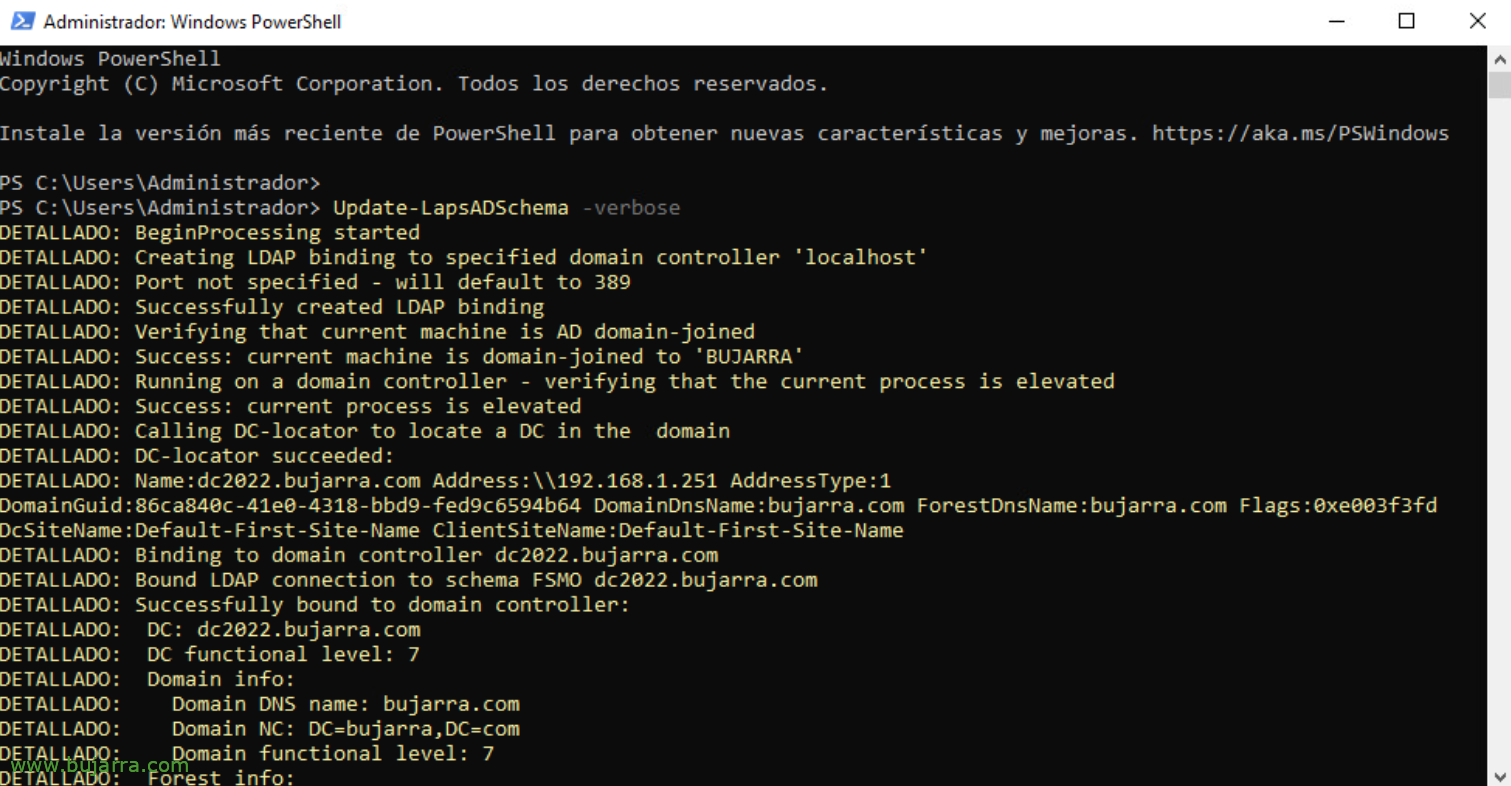
To enable Windows LAPS, the first step will be to extend the scheme of our Active Directory, we run from a PowerShell with Schema Master permissions:
Update-LapsADSchema -verbose
We need to enable Windows LAPS on the OUs that contain the computer accounts we want to govern, Running:
Set-LAPSADComputerSelfPermission –Identity "OU=...,OU=...."
And finally we will create a GPO where we will apply the settings that we are interested in for Windows LAPS, since “Equipment Setup” > “Policies” > “Administrative templates” > “System” > “LAPS” We will have several options. This GPO must be applied to the team accounts that we want to manage.
The “Password settings” we must enable it and indicate the complexity we want, as well as the length or age of the password we want.
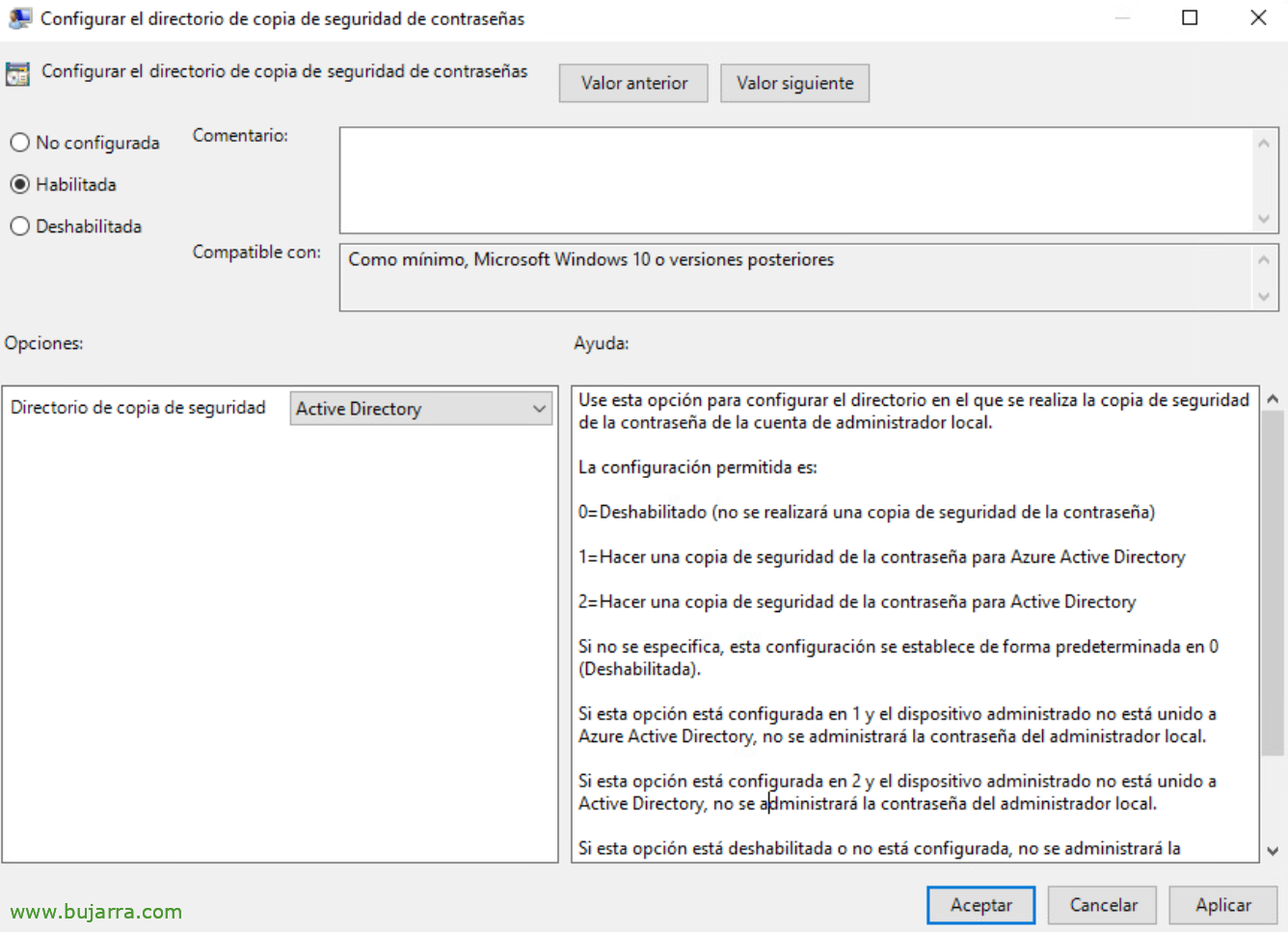
In the directive “Configure the backup directory” we will indicate as Backup Directory to “Active Directory” to manage and store computer passwords there.
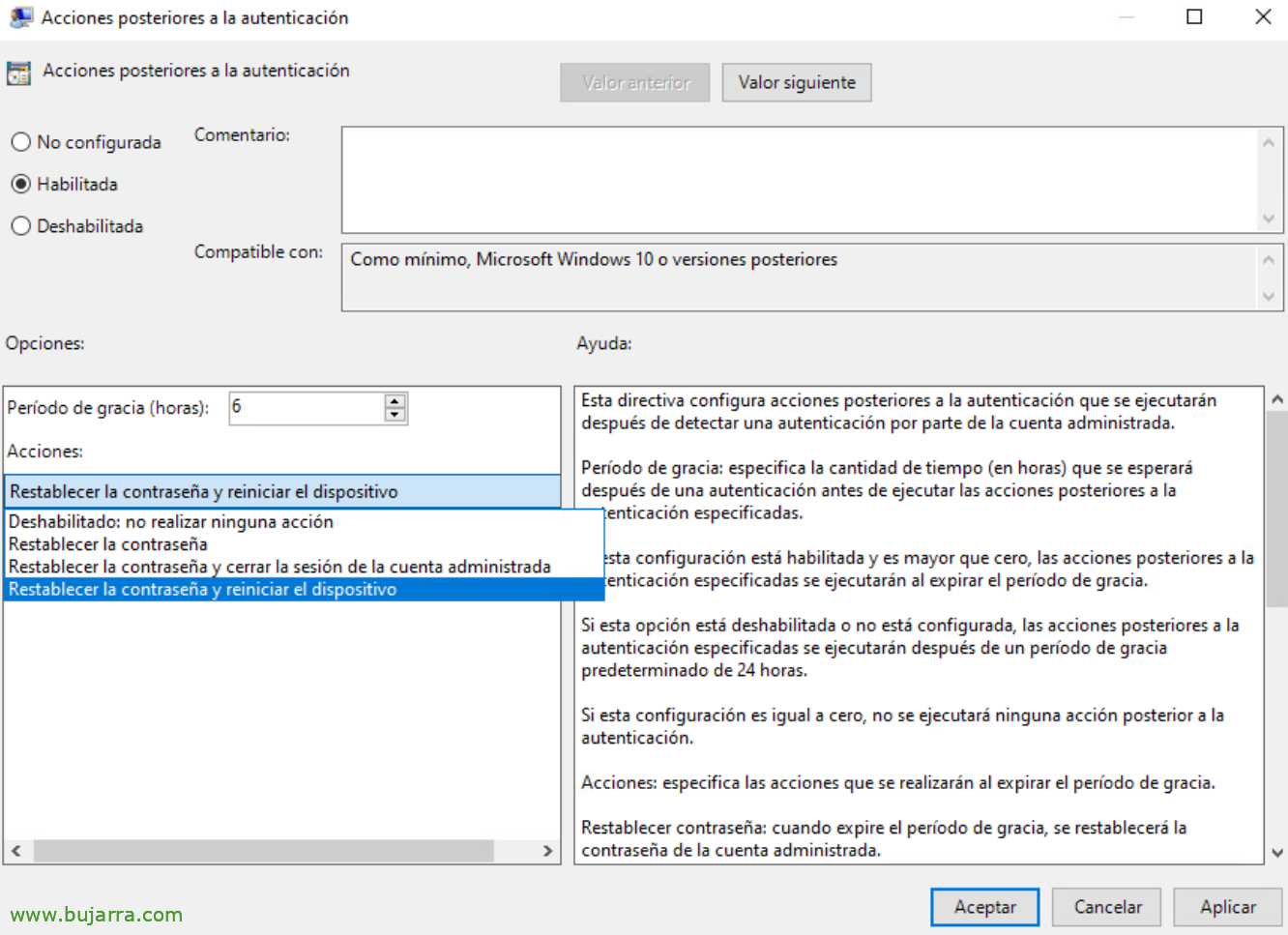
Once the password is used, we have a GPO that will allow us to perform some action if we are interested, It's called “Post-authentication actions”,
If we enable “Enable password encryption” our password will travel in encrypted form to the Active Directory to be stored, We need functional level of mastery 2016.
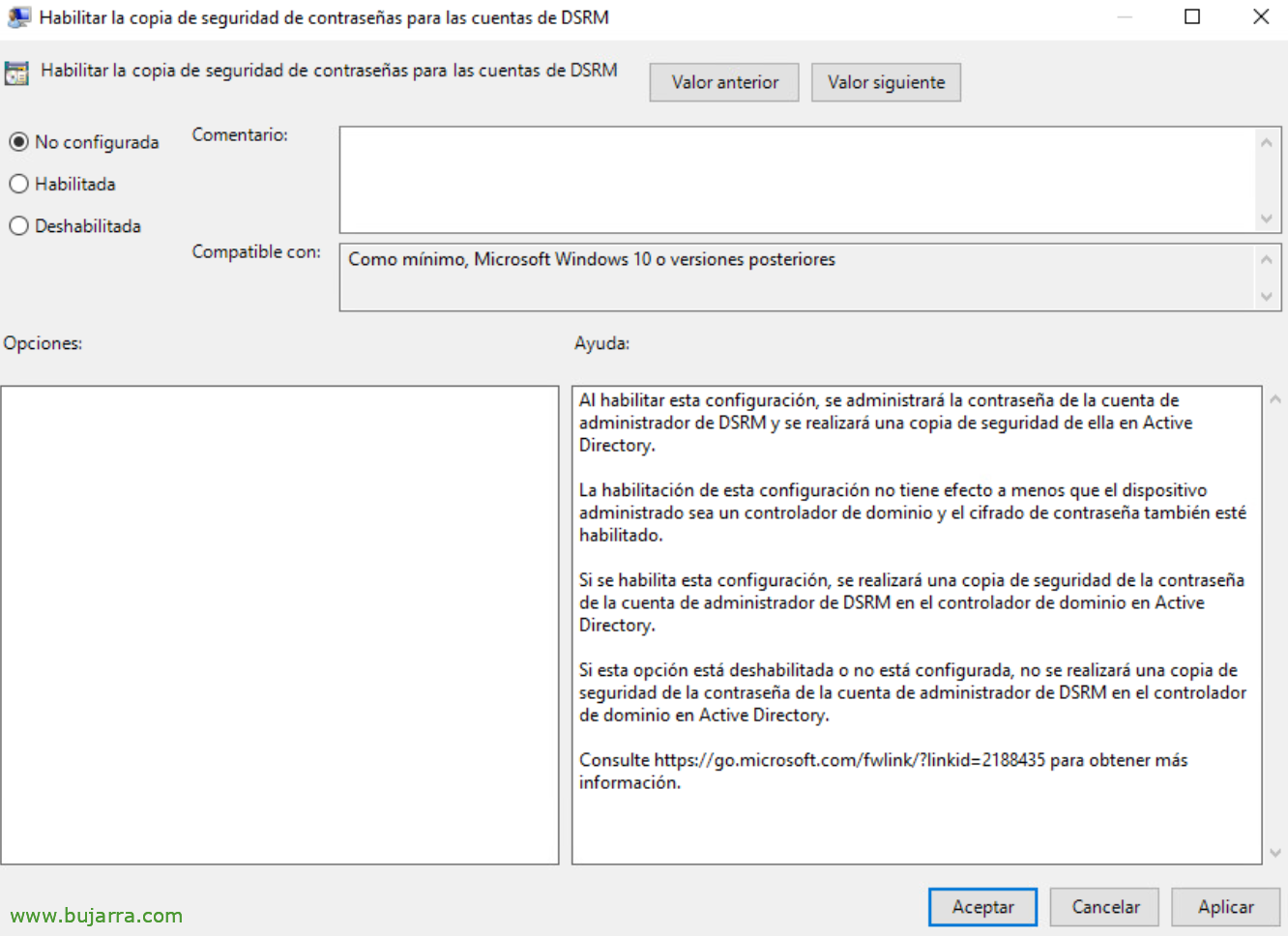
If you are interested in managing the password for Directory Services Restore Mode (DSRM o Directory Services Restore Mode) we will be able to enable it, and the GPO must be applied to the Domain Controllers.
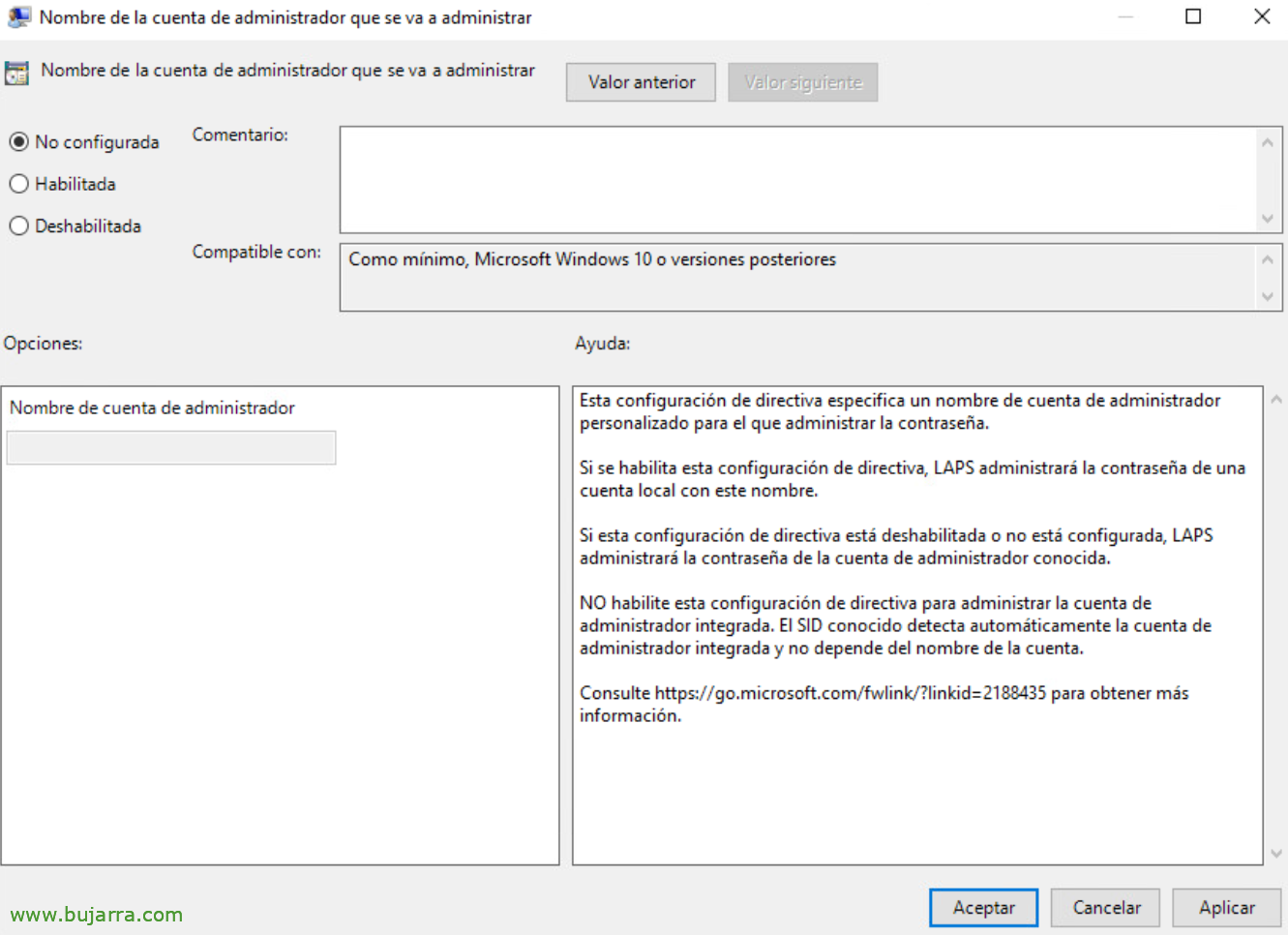
By default it will not be necessary to indicate the name of the account to be managed, since Windows LAPS will determine it by the account SID, if in our case we have a particular user that we want to manage, then we will indicate it.
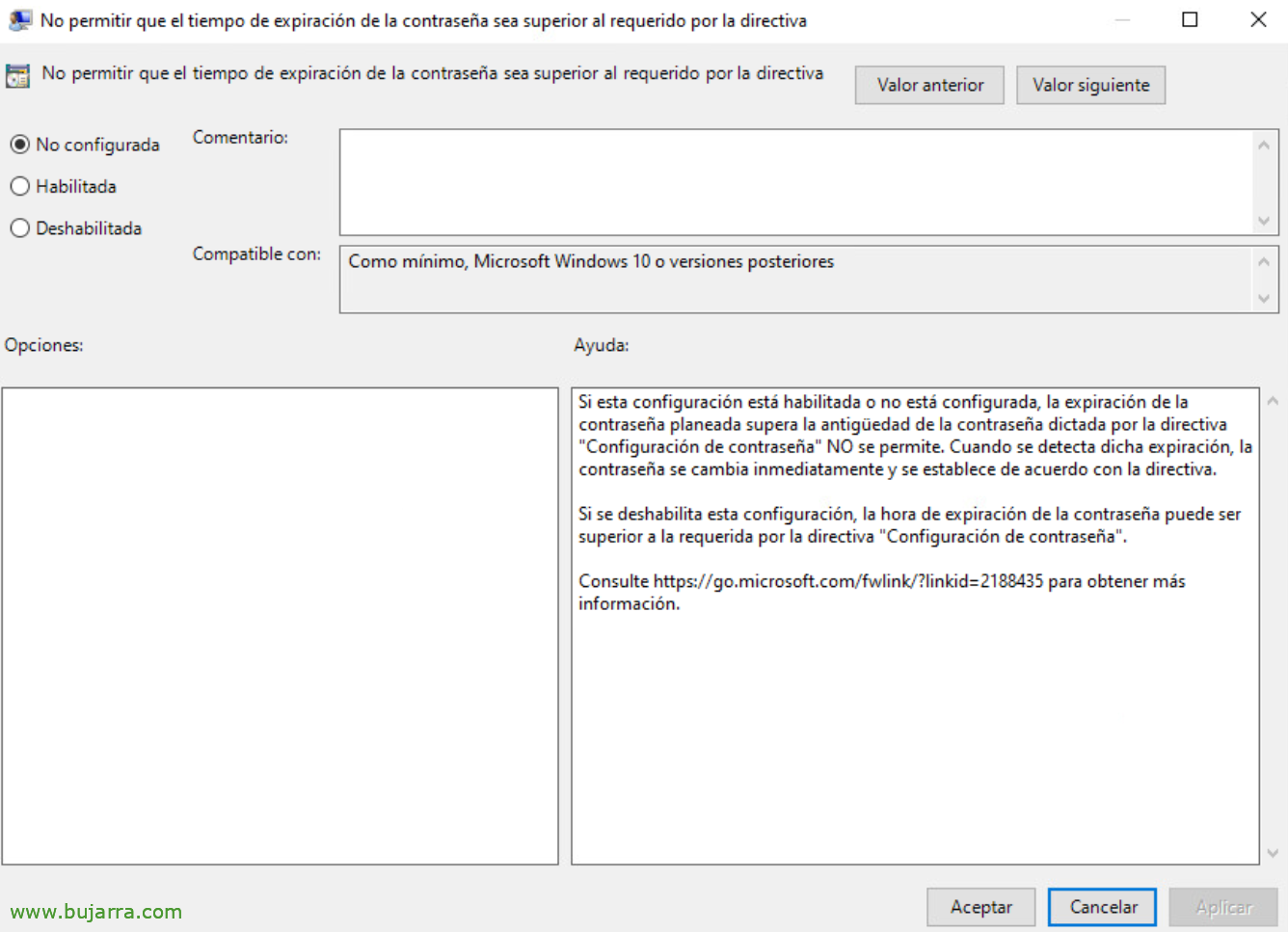
And we can also “Do not allow the password expiration time to be longer than required by the policy”.
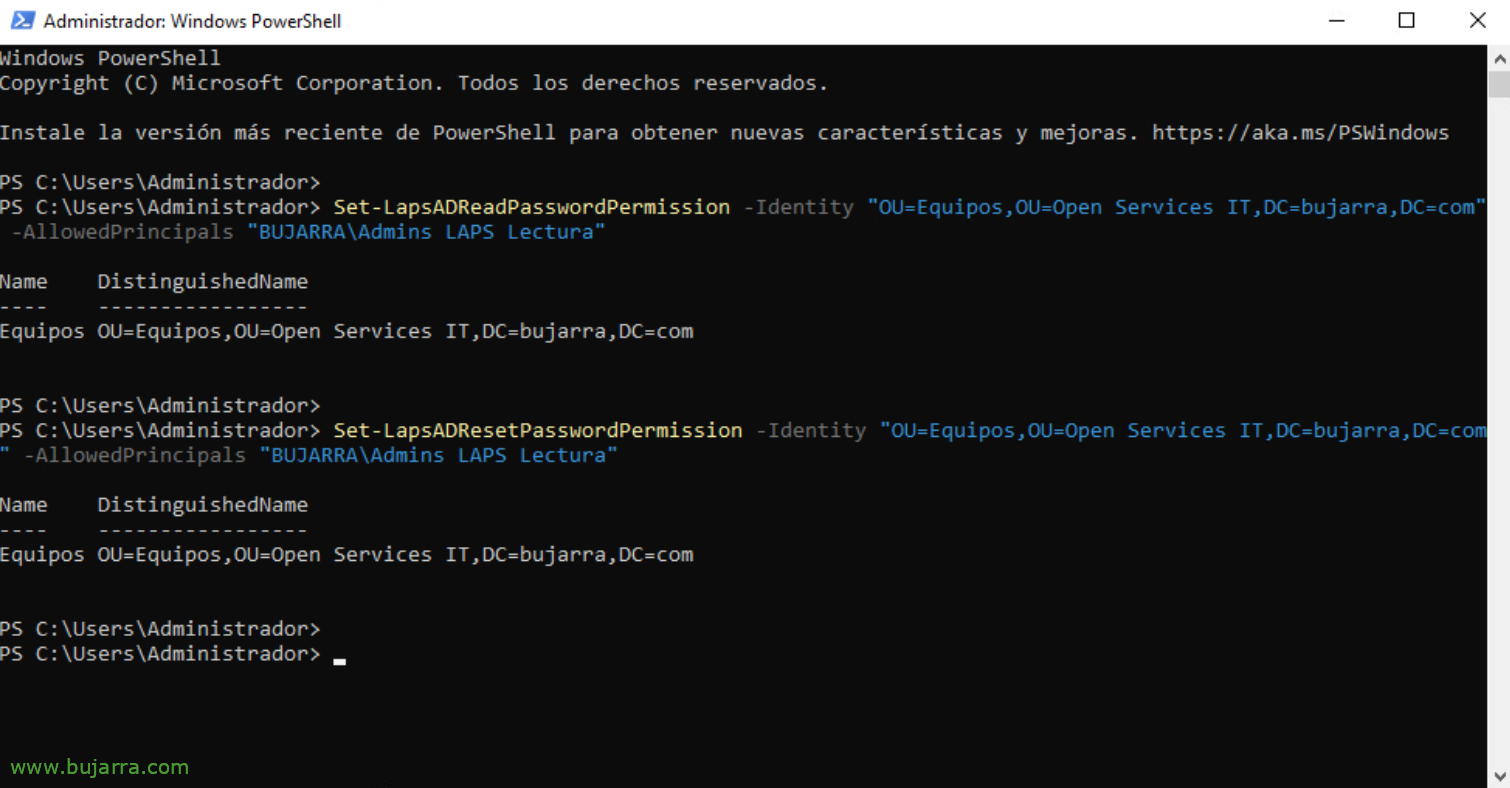
If we want to give permissions to read passwords to a specific group in the Active Directory, we will do so with:
Set-LapsADReadPasswordPermission -identity "OU=...,OU=...." -AllowedPrincipals "MYDOMAINGroup Name"
If we want to give permission to reset the passwords of a specific group in the Active Directory, We will do it with:
Set-LapsADResetPasswordPermission -identity "OU=...,OU=...." -AllowedPrincipals "MYDOMAINGroup Name"
Set-LapsADResetPasswordPermission -identity "OU=...,OU=...." -AllowedPrincipals @("MYDOMAINGroup Name 1", "MYDOMAINGroup Name 2")
If we want to see the permissions that apply to an OU, We could see it with this command:
Find-LapsADExetendedRights -Identity "OU=...,OU=...." |Fl
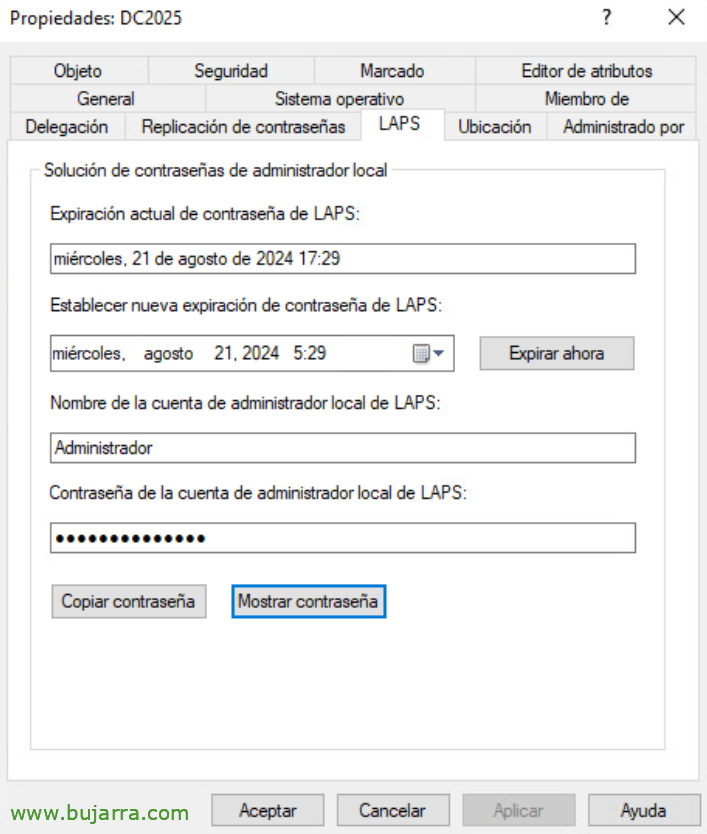
And well, to view passwords for LAPS-managed accounts, it will be as simple as opening the Active Directory Users and Teams console, Find the account of the team we want, We'll see that it has a tab “LAPS” where it will tell us when the password expires, If we want to force it to change now, as well as who the managed administrator user is, or if we want to see or copy the password.
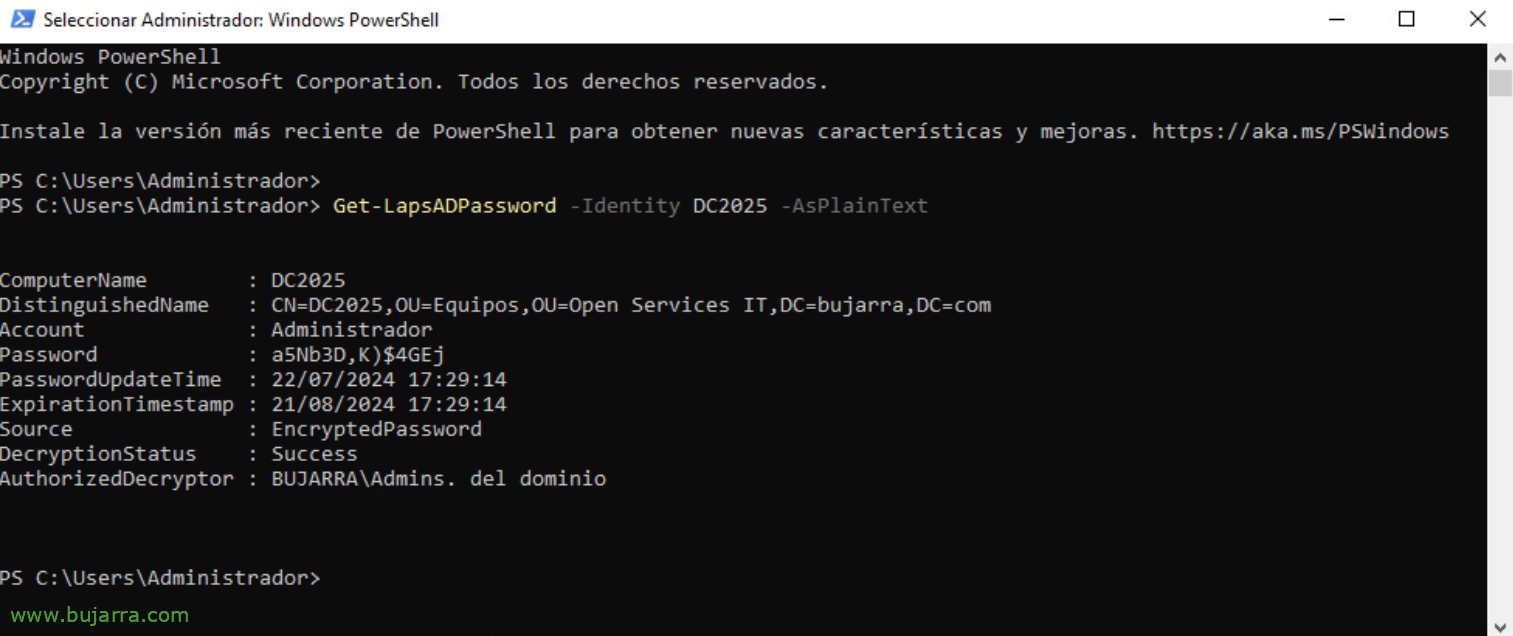
We can also see the PowerShell password of a remote machine:
Get-LapsADPassword -Identity NOMBRE_MAQUINA -AsPlainText
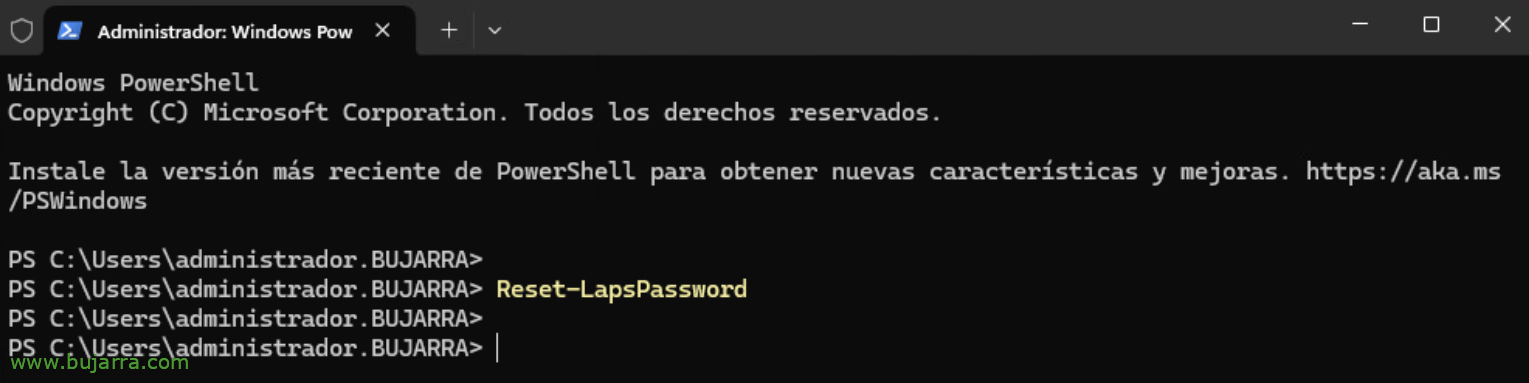
As well as forcing the password of the local machine where we are to be reset:
Reset-LapsPassword
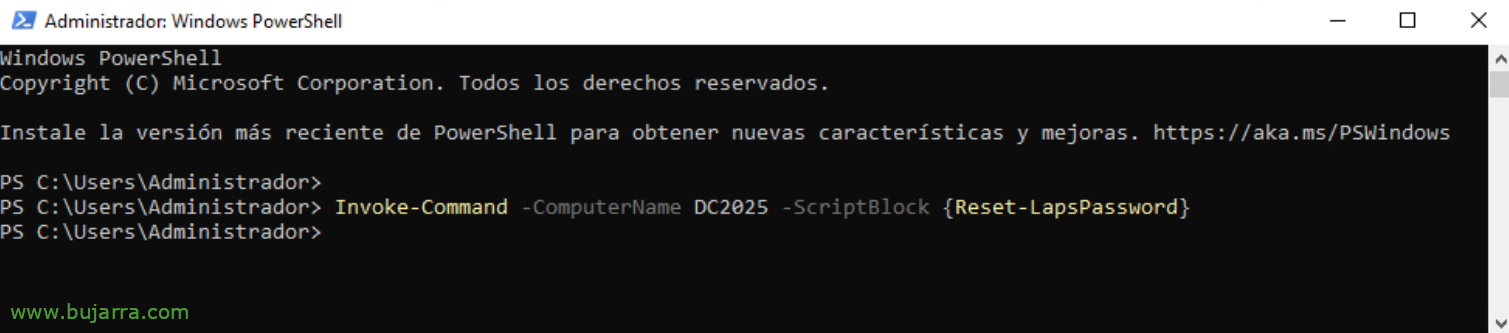
Or reset the password of a remote machine:
Invoke-Command -ComputerName NOMBRE_MAQUINA -ScriptBlock {Reset-LapsPassword}
Well, I hope that this type of document can help you to manage your time and your organization in a more efficient way, to take ideas to secure the environments and make our lives 🙂 easier So with this I say goodbye, And as always I send you a hug!