Implementing Windows LAPS
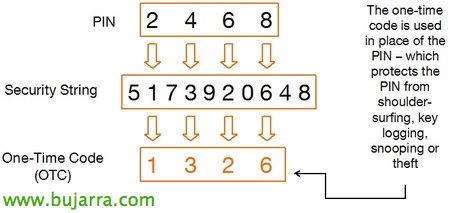
Well, Today we come with a classic, a great tool that we have never talked about in the Blog, so in case anyone doesn't know her, we will implement Windows LAPS (Local Administrator Password Solution) in our organization. Which as its name suggests, help us manage local administrator accounts on the positions, member servers of our organization and even the DSRM password.