Logon auditing of Active Directory users with Elasticsearch and Grafana
Something very common that we are usually asked for is the possibility of knowing the logons and other interesting information that a user can generate. In this post we will see how to visualize data as interesting as: When have they logged in, When they closed the session, Incorrect login attempts, When a computer has been locked, or unlocked, or when the screensaver has tripped, or it has been deactivated…
Actually, this type of information, as we know, is recorded in the Event Viewer of the computers, Some records may be provided to us by domain controllers, and other records the computers where users work.
The example we will make in this post will be as I said, Collect team events, we will centrally store them in Elasticsearch and then with Grafana we will make the queries that interest us the most based on an event ID. We will be able to see the data in real time, or directly search over a period of time, or directly ask for a particular user. Then we visualize them in graphics, board, Or however we want, And if we want to, we generate PDF reports and we send them via email to whoever is interested.
So obviously we will first need a machine with Elasticsearch working, And then We'll install Winlogbeat on domain controllers. The DCs' event viewer would record when a user logs in and incorrectly logins. And if we want data on when they have logged out, or what we were talking about at the beginning of when a team crashes for a timeout, or when it is unlocked, Same with the screensaver, what if when the screensaver jumps or when it is deactivated. There we would need to install Winlogbeat on the client computer.
In the end, as we understand, event viewer events are collected in Elasticsearch and then we'll query for any identifiers, In this post we will only look at these examples, But there are many other possibilities!
To summarize, the configuration part of each Winlogbeat, Remember that we can filter from there directly to bring all types of records or only those that interest us, In this case, what we are talking about would be recorded in the 'Security' events, So we'd be left with our winlogbeat.yaml more or less like this:
winlogbeat.event_logs: - Name: Security ignore_older: 72h setup.kibana: host: "https://DIRECCION_IP_KIBANA:5601" output.elasticsearch: # Array of hosts to connect to. Hosts: ["https://DIRECCION_IP_ELASTICSEARCH:9200"] username: "USER" password: "PASSWORD"
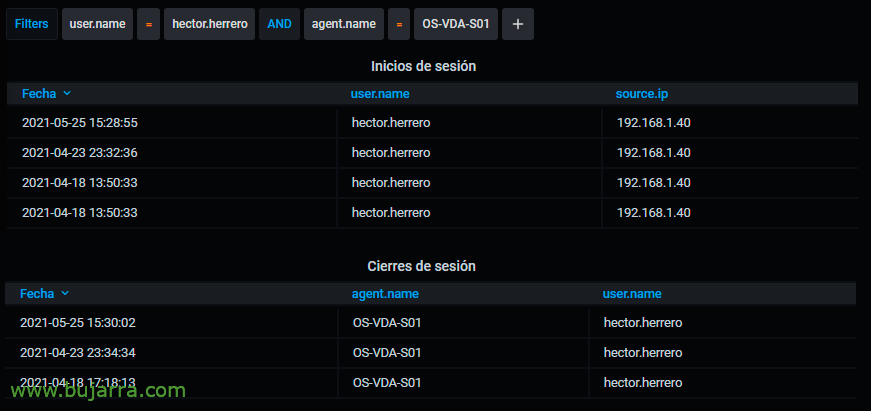
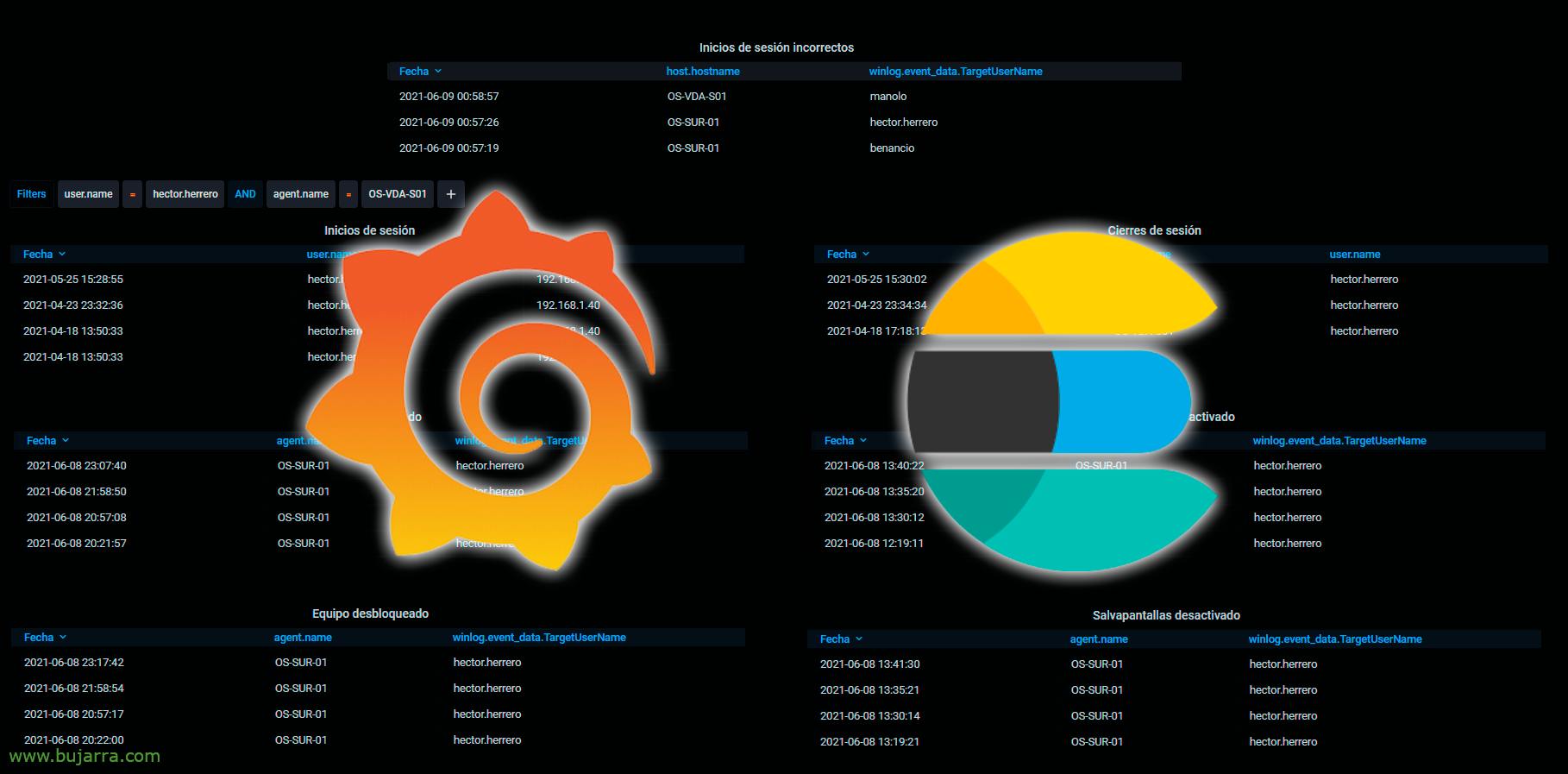
Once we have Elasticsearch powered and we have created the DataSource from Grafana against this index we can start to be able to make the visualizations that interest us. I'll do the most basic of all, a Table, a table where we will see in a listed format the fields that interest us and filtering by the ID of an Event ID or Event ID.
For example, to view logouts (When someone logs out of their user), we will make a very simple Lucene query, By putting “event.code: 4647” It is enough for us. To find out which ID does what, I will leave below the post a list of the most interesting ID's regarding this topic. And the best as always, will be playing from Kibana to discover other types of queries.
Total, that with a Table type panel, With the query, indicating that we want the result in Raw format, we transform it into JSON format and select the fields we want to display, we can also rename them or change their format. Look at the image to answer any questions.
Then we can create as many panels as different information we want to visualize, to view sign-ins with the ID 4624 we will have it or maybe with it 4768, It depends on what type of logon we are interested in. For logouts we can search by the ID 4647.
If we want to see the incorrect logins, we will only have to look for the ID 4625.
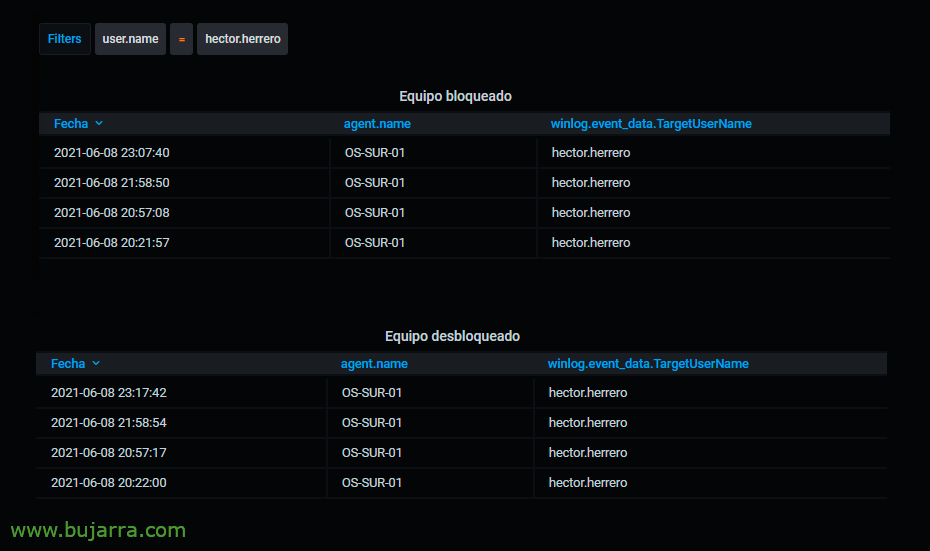
If we want to search for computers when they crash, when a user session is locked we will have the event ID 4800 and for unlocks we will filter by the ID 4801.
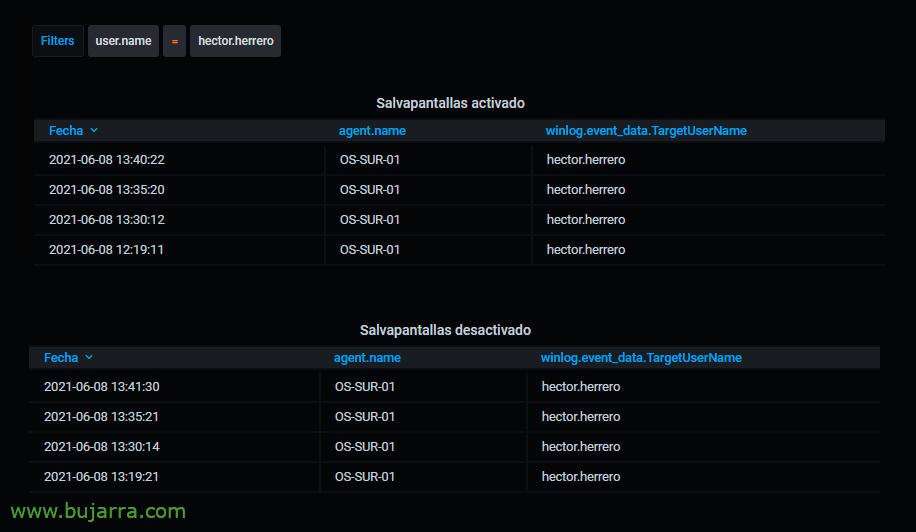
And the same for the screensaver, if we want to know when it has jumped on a computer, we will look for the ID 4802 and in the case of knowing when they have deactivated the screensaver we will have the ID 4803.
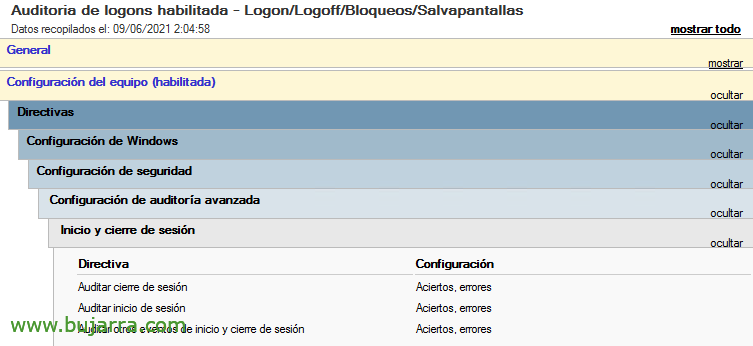
Last but not least, we must create a GPO to be able to enable 3 Policies, that allow this type of information to be collected in the teams' event viewers, from Computer Settings > Policies > Windows Settings > Security Settings > Advanced Audit Settings > Login and logout:
- Audit logout: Successes and mistakes
- Audit login: Successes and mistakes
- Audit other logon and logoff events: Successes and mistakes
I leave you a list of events that may be useful to you:
Change in audit policies:
4719: System Audit policy changed.
4908: Changed the Login Table for Special Groups.
Changes to audit authentication policies
4706: A new trust has been created in a domain.
4707: A trust to a domain has been removed.
4713: Kerberos policy has been changed.
4716: Trusted domain information has been modified.
4717: System Security access has been granted to an account.
4718: System security access to an account has been removed.
4739: A domain policy has been modified.
4865: Added a trusted forest information entry.
4866: A trusted forest information entry has been deleted.
4867: A trusted forest information entry has been modified.
4706: A new trust has been created for a domain.
4707: A trust to a domain has been removed.
Computer Account Management Audit
4741: A computer account has been created.
4742: A computer account has been changed.
4743: A computer account has been deleted.
Audit of DPAPI activity
4692: An attempt was made to back up the Data Protection Master Key.
4693: An attempt has been made to recover the data protection master key.
4695: An attempt has been made to unprotect auditable protected data.
Kerberos Authentication Service Audit
4768: A Kerberos authentication ticket has been requested (TGT)
4771: Kerberos pre-authentication failed
4772: Kerberos authentication ticket request failed
Auditing the operation of the Kerberos service ticket
4769: A Kerberos service ticket has been requested (TGS)
4770: A Kerberos service ticket has been renewed
Logout auditing
4634: A user account has been logged out.
Login auditing
4624: A user account has been successfully logged in.
4625: A user account was unable to log in, Invalid credentials.
4648: An attempt was made to log in with explicit credentials.
Auditing Other Account Sign-In Events
4648: An attempt was made to log in with explicit credentials.
4649: A replay attack detected.
4800: Workstation is locked.
4801: Workstation has been unlocked.
5378: The requested credential delegation was not permitted by policy
Auditing Other Object Access Events
4698: A scheduled task has been created.
4699: A scheduled task has been deleted.
4702: A scheduled task has been updated.
Creation of Audit processes
4688: A new process has been created.
Audit Security Group Management
4728: Added a member to a global security group.
4729: A member of a global security group has been removed.
4732: Added a member to a security-enabled local group.
4733: A member of a security-enabled local group has been removed.
4735: A security-enabled local group has been modified.
4737: A security-enabled global group has been modified.
4755: A security-enabled universal group has been modified.
4756: Added a member to a security-enabled universal group.
4757: A member of a security-enabled universal group has been removed.
4764: Changed the type of a group.
Audit Security System Extension
4610: The Local Security Authority has uploaded an authentication packet.
4611: A trusted login process has been registered with the Local Security Authority.
4697: A service has been installed on the system
Sensitive privilege use auditing
4672: Special privileges assigned to a new login.
4673: A privileged service has been called.
4674: An operation was attempted on a privileged object.
Special Login Audit
4964: Special groups have been assigned to a new login.
User Account Management Audit
4720: A user account has been created.
4722: A user account has been activated.
4723: An attempt was made to change the password for an account.
4724: An attempt was made to reset an account password.
4725: A user account has been deactivated.
4726: A user account has been deleted.
4738: A user account has been modified.
4740: A user account has been locked.
4765: A SID history has been added to an account.
4766: Attempt to add a SID history to an account failed.
4767: A user account has been unlocked.
4780: ACL has been configured for accounts that are members of Admin groups.
4794: An attempt has been made to set the restore mode of directory services.