Corporate Communications with Synapse
In this post we will look at the installation of Synapse, A proprietary server that will allow us to control and secure messaging communications between our users, a simile of Slack. We will be able to give them secure access to meeting rooms through a mobile app or a website, Private Messaging, Active Directory integration, with Jitsi, Nextcloud…
A tool that will make it much faster for us to organize our work life through channels or rooms where users can exchange their needs, A real alternative to email, Teams, Slack and more. They will be able to chat, send files, video conferencing integrated with our Jitsi, or what I said, if you have Nextcloud we can integrate the client natively.
¡Started! Matrix is an open protocol and network for decentralized communication, where users can participate in public and private chat rooms through public and private servers (“Home Servers”); as well as any customer of your choice, just like we do with email. The goal is to provide a free and open global network for end-to-end encrypted communication, without sacrificing ease of use, and thus be able to free users from being trapped in the apps of certain manufacturers, that today has become the most common.
Synapse is the most installed Matrix home server implementation, is written in Python 3 and it's open source. In this post we will see several things:
- Install Synapse
- Enable Reverse Proxy with Nginx
- Install Element client
- Active Directory Authentication Integration.
- Install Element-web
- Jitsi Integration
- Integration with Nextcloud
Installing Synapse
To do the installation we will rely on an Ubuntu Server 21.04 that we will have updated and with a static IP. We start by installing the requirements:
Sudo apt install build-essential python3-dev libffi-dev python3-pip python3-setuptools sqlite3 libssl-dev virtualenv libjpeg-dev libxslt1-dev
We download the repo and the keys to finally install Matrix Synapse:
sudo apt install -y lsb-release wget apt-transport-https sudo wget -O /usr/share/keyrings/matrix-org-archive-keyring.gpg https://packages.matrix.org/debian/matrix-org-archive-keyring.gpg done "deb [signed-by=/usr/share/keyrings/matrix-org-archive-keyring.gpg] https://packages.matrix.org/debian/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/matrix-org.list sudo apt update sudo apt install matrix-synapse-py3
The next question will jump out at us, we need to indicate the FQDN name of the server, something like matrix.mydomain.eso that you must register on your DNS servers and resolve against the IP of this machine.
If we want to send anonymous statistics to improve usage,
We initiate and enable the service:
Sudo SystemCTL Start Matrix-Synapse.service sudo SystemCTL Enable Matrix-Synapse.service
Edit the Synapse configuration file: /etc/matrix-synapse/homeserver.yaml and we'll see the listening port, The Listening Direction (We can leave 127.0.0.1 whether we will access with the reverse proxy), if we want TLS, or important, if we want to allow users to register freely in our environment, Or not:
...
- port: 8008
TLS: False type: http x_forwarded: true bind_addresses: ['0.0.0.0']
Resources:
- names: [client, Federation]
compress: False
...
enable_registration: False
...
If we make any changes we restart the service:
sudo systemctl restart matrix-synapse.service
And if in bind_address we listen from 0.0.0.0 We will be able to open a browser and verify that the service is running, We open against HTTP://DIRECCION_IP_SYNAPSE:8008
Reverse Proxy
As we can see, our Synapse runs under HTTP, what we will do next is install Nginx and enable access to Synapse using reverse proxy and SSL encryption. So come on, we installed Nginx, We start it and mark it as automatic start with the system:
Sudo apt install nginx sudo systemctl start nginx.service sudo systemctl enable nginx.service
We created the configuration file for the Synapse website, We call it for example '/etc/nginx/sites-available/synapse’ and at least we will replace the example FQDN that I leave you with that of each one of you:
Server {
Listen 80;
server_name matrix.mydomain.eso;
Return 301 https://$server_name$request_uri;
}
Server {
Listen 443 SSL;
Listen [::]:443 SSL;
server_name matrix.mydomain.eso;
ssl_certificate /etc/ssl/certs/wildcard_midominio_eso.cer;
ssl_certificate_key /etc/ssl/certs/wildcard_midominio_eso.key;
# If you don't want to serve a site, comment this out root /var/www/html;
index index.html index.htm;
location /_matrix {
proxy_pass http://127.0.0.1:8008;
proxy_set_header X-Forwarded-For $remote_addr;
}
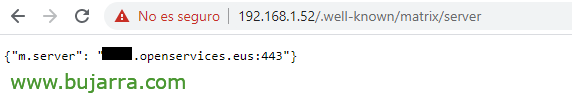
location /.well-known/matrix/server {
Return 200 '{"m.server": "matrix.midominio.eso:443"}';
add_header Content-Type application/json;
}
location /.well-known/matrix/client {
Return 200 '{"m.homeserver": {"base_url": "https://matrix.midominio.eso"},"m.identity_server": {"base_url": "https://vector.im"}}';
add_header Content-Type application/json;
add_header "Access-Control-Allow-Origin" *;
}
}
Creamos un enlace para habilitar el sitio de Synapse y reiniciamos Nginx:
sudo ln -s /etc/nginx/sites-available/synapse /etc/nginx/sites-enabled/ sudo systemctl restart nginx.service
Si todo ha ido bien podremos validarlo abriendo un navegador contra https://DIRECCION_IP_SYNAPSE/.well-known/matrix/server
Element
GOOD, to connect to our Synapse server, We can use any customer as we said above, the most common is perhaps Element, formerly known as Riot. Well, Element can be opened directly from https://app.element.io or we can Download a client Locally, for our Windows, Linux, Mac, Android or iOS.
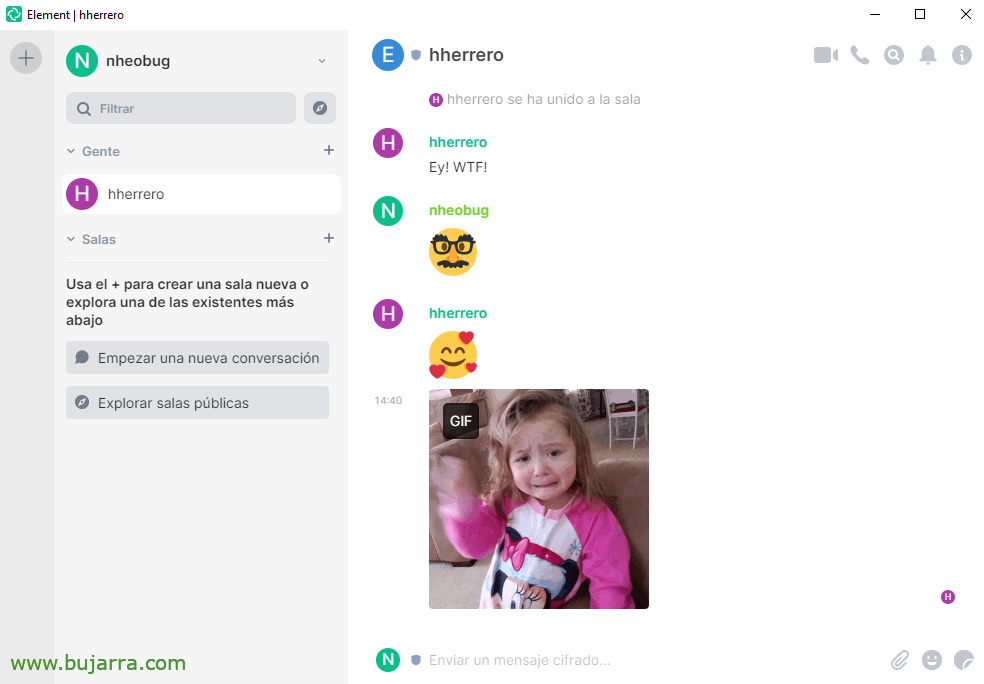
Once Element is opened, We must indicate that we have the account hosted on our own server, we indicate our FQDN and we can log in. But before we log in… Will we have to have an account? ¿No? GOOD. if we have Synapse already configured against our LDAP we can try to log in with our Active Directory user, If not,, We will need to use local users. In order to create local users we must allow users to register and for this we remember, In the configuration file we set 'enable_registration: True’ and we restart the service. Now we could create a user account. But of course, Beware of open records, It is true that in the configuration you will see that we may require a previous shared secret and thus they are not validated, put a CAPCHA… Normally we will leave the records disabled.
And nothing, if we enter now Element welcomes us, allows us to send messages to contacts, explore public rooms or create group chats among others.
Element itself has no complications, Users handle these types of tools on a daily basis, But this one is open source, Sure, encrypted and runs in our datacenter, No data leaks or with maximum privacy.
Configuration against Active Directory
The most convenient thing to do is to integrate Synapse authentication with your Active Directory domain, for this, first we will install the LDAP connector and finally in the Synapse configuration we indicate the data of our LDAP. We install the requirements first:
sudo apt-get install matrix-synapse-ldap3 -y
Edit the Synapse configuration file (/etc/matrix-synapse/homeserver.yaml) and added the following settings in the corresponding section:
password_providers:
- module: "ldap_auth_provider. LdapAuthProvider"
config:
enabled: True uri: "LDAP://DIRECCION_IP_DC:389"
start_tls: False base: "ou=OU_2,ou=OU_1,dc=DOMAIN,dc=LOCAL"
attributes:
uid: "sAMAccountName"
mail: "mail"
Name: "givenName"
bind_dn: "cn=USUARIO_LDAP_SYNAPSE,ou=OU_2,ou=OU_1,dc=DOMAIN,dc=LOCAL"
bind_password: "PASSWORD"
#filter: "(objectClass=posixAccount)"
Where Good, we could add some extra lines against another DC, as well as that preferably configure LDAPS better by the 636 and with TLS and in the BaseDN we will have the base from where users will look for us, as well as if we want to put any additional filter…
And as soon as after restarting the Synapse service we will be able to try to log in with our domain users.
sudo systemctl restart matrix-synapse.service
Element-web
On the Synapse server itself we can install Element-web, so that we can avoid making users have to go to the Element website to talk or have a client installed offline. Element-web will provide us with the same GUI but running on our server (in Nginx), a web client, go.
So, We create the directory where we will save element-web, we downloaded it, We install GNUPG, The keys & we install them, We unzip element, We create a symbolic link and correct the permissions; finalmente crearemos nuestro fichero de configuración:
sudo mkdir -p /var/www/html/element cd /var/www/html/element sudo wget https://github.com/vector-im/element-web/releases/download/v1.7.34/element-v1.7.34.tar.gz sudo apt install -y gnupg sudo wget https://github.com/vector-im/element-web/releases/download/v1.7.34/element-v1.7.34.tar.gz.asc sudo gpg --keyserver keyserver.ubuntu.com --search-keys D******@**ot.im
sudo gpg --verify element-v1.7.34.tar.gz.asc sudo tar -xzvf element-v1.7.34.tar.gz sudo ln -s element-v1.7.34 element sudo chown www-data:www-data -R element cd element sudo cp config.sample.json config.json
Editamos el fichero de configuración (/var/www/html/element/element/config.json), modificamos la ‘base_url’ con el FQDN completo de Synapse (matrix.midominio.eso); y ‘server_name’ con el nombre del dominio (midominio.eso). Staying:
{
"default_server_config": {
"m.homeserver": {
"base_url": "https://matrix.midominio.eso",
"server_name": "midominio.eso"
},
"m.identity_server": {
"base_url": "https://matrix.midominio.eso"
}
},
...
We create the configuration file for Nginx:
Server {
Listen 80;
server_name element.mydomain.eso;
Return 301 https://$server_name$request_uri;
}
Server {
Listen 443 SSL;
Listen [::]:443 SSL;
server_name element.mydomain.eso;
ssl_certificate /etc/ssl/certs/wildcard_mi_dominio.cer;
ssl_certificate_key /etc/ssl/certs/wildcard_mi_dominio.key;
root /var/www/html/element/element;
index index.html;
Location / {
try_files $uri $uri/ =404;
}
}
We enable the site and restart Nginx:
sudo ln -s /etc/nginx/sites-available/element /etc/nginx/sites-enabled/ sudo systemctl restart nginx.service
And we tried with a browser to access https://element.mydomain.eso et voilà! We will now be able to log in with our users directly on the web, and I won't tell you if we customize the Start…
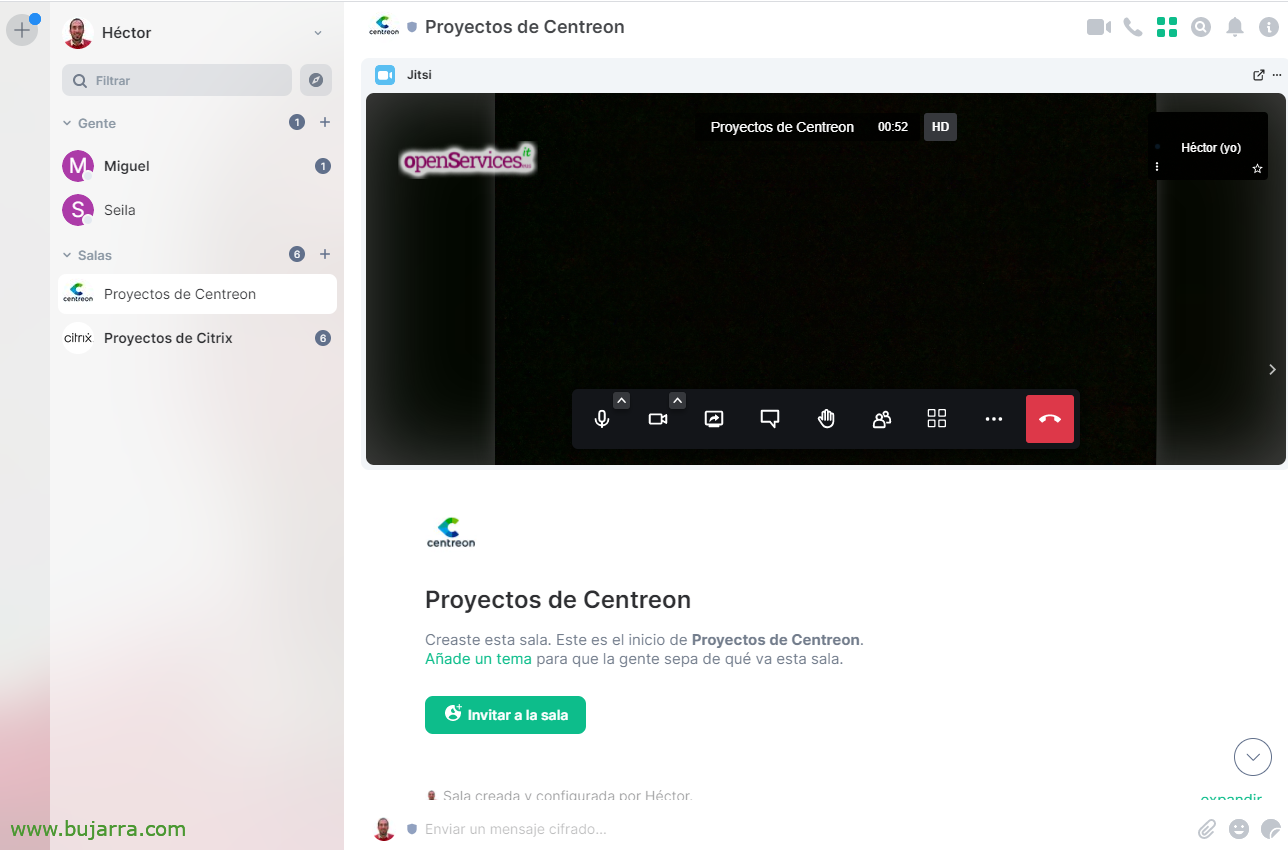
Jitsi Integration
If we have our own server Jitsi-based video conferencing, we can integrate it with Element-web and so when they want to make a call or video call, or group, use our resources, Everything stays at home, sure, encryption… Simply edit the element-web configuration file (/var/www/html/element/element/config.json) in the Jitsi section and put our FQDN:
},
"Jitsi": {
"preferredDomain": "jitsi.mydomain.eso"
}
And it would look super cool!
Integration with Nextcloud
Come on, we're done… This is the same, if you have your own file exchange system or even more a Hub to connect your users with Nextcloud you will be able to integrate an APA into the Nextcloud interface itself with an app
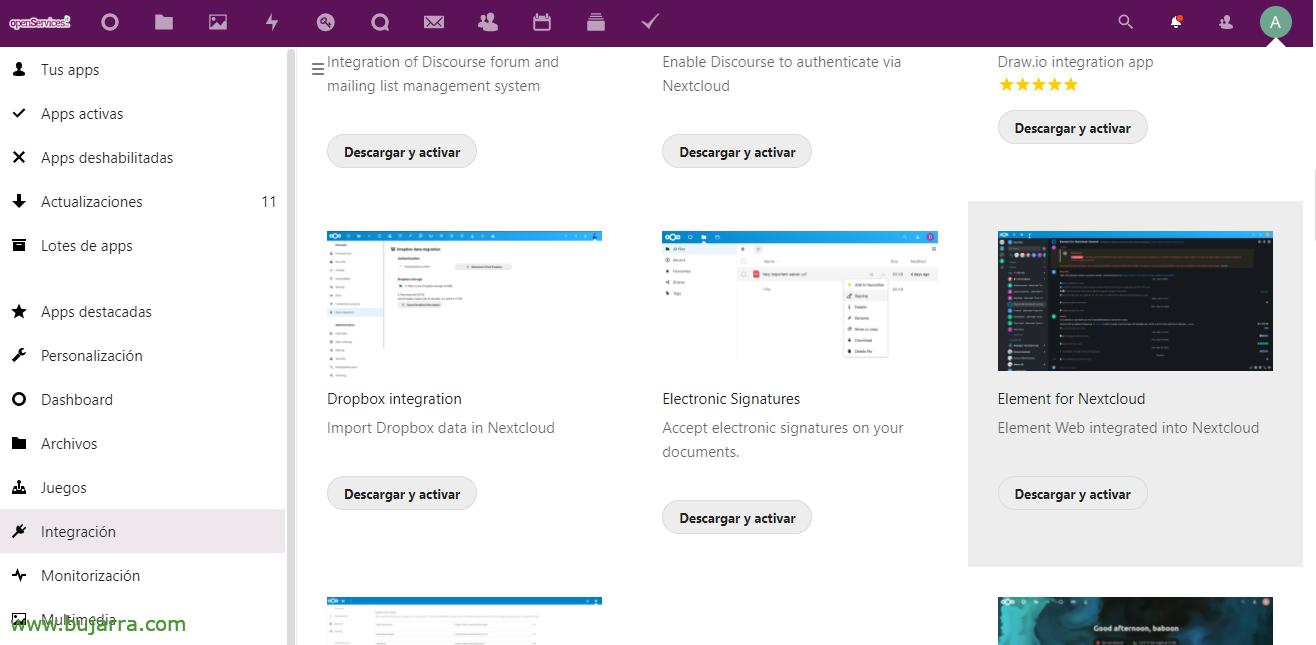
On Nextcloud, logged in with an account with administrator privileges, Let's go to the Apps > Integration > and we search for 'Element for Nextcloud', Click on “Download and activate”.
If we go to the Settings part, in the side menu we can see a new section called 'Element', we will need to configure the URL of the Element Web server.
And now users will have an additional icon in the top bar, where they can directly talk, interact with the rest of the classmates… ¡precious!
Well, which I hope you have found interesting, thank you to all of you who give Likes and Recommendations on social networks, hugs to tod@s!