Wifi Network Configuration with NPS Server Authentication
In this document we are going to try to explain how to establish a level of security in our wifi network, for controlled and secure equipment access, based on authentication through the users of our Active Directory,
The first thing we will need is to install an Enterprise Certificate Authority in our Domain in order to secure the Wi-Fi access of our customers.
Once the Certificate Authority is installed, we will generate a Computer Certificate that we will use for our Radius validation. To do this, we open an MMC console and add the certificate console.
We will now make a request for a new certificate, in this case of type Domain Controller since it is a Domain Controller where we will install our NPS Server. In the event that it is different, we will request a certificate of Equipment.
We press Enroll.
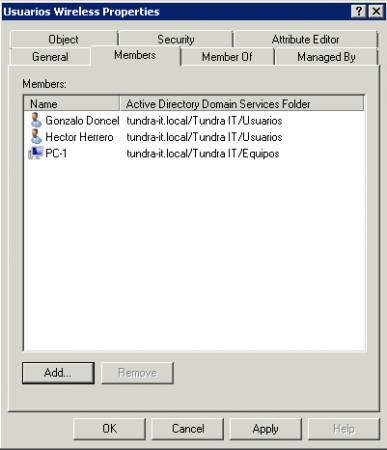
Once the certificate has been made, we will go on to configure an Active Directory group that will contain the users and computers to which we want to give access permissions.
For them we open Active Directory users and computers and create a Universal Group in the Active Directory that will contain the users and computers that we want to give permissions in the Authentication of our WIFI network.
To this group we will add the users and computers to which we allow access.
We now have the basis to start working our NPS server. Now we will install the Role “Network Policy and Access Services”,
We leave a mark “Network Policy Server”, “Routing and Remote Access Services”, “Remote Access Service” & “Routing”
Now let's go to NPS and create a Standard configuration: “RADIUS for 802.1X Wireless” and press the “Configure 802.1X”,
Mark “Secure Wireless Connections” And we give it a name,
We add our Radius clients who will be our Access Points
We give the AP a name, your IP address and we create a password that you will share with the AP
We will add as many APs as we have to authenticate by Radius.
Explanation of the different existing Authentication Methods:
– EAP (Extensible Authentication Protocol) uses an arbitrary authentication method, such as certificates, Smart Cards, or credentials.
– EAP-TLS (EAP-Transport Layer Security) is an EAP type that is used in certificate-based security environments, and it provides the strongest authentication and key determination method.
– EAP-MS-CHAP v2 (EAP-Microsoft Challenge Handshake Authentication Protocol version 2) is a mutual authentication method that supports password-based user or computer authentication.
– PEAP (Protected EAP) is an authentication method that uses TLS to enhance the security of other EAP authentication protocols.
When selecting the authentication mechanism, you need to balance between the levels of security required with the effort required for deployment. For the highest level of security, choose PEAP with certificates (EAP-TLS). For the greatest ease of deployment, choose PEAP with passwords (EAP-MS-CHAP v2).
Elegimos el tipo de autenticación “Microsoft Protected EAP (PEAP)” and click on “Set” para elegir el certificado que hemos generado anteriormente de nuestra CA.
Elegimos el Certificado generado anteriormente por nuestra CA y en este caso vamos utilizar el metodo de autenticación EAP-MSCHAPv2
Ok and Next
Now we specify the Active Directory Groups to which we give access, I mean, the group we created earlier “Wireless Users”. “Next”,
Following,
End.
We register the NPS Server in the Active Directory. Right-click on NPS and Register Server in Active Directory.
“OK”,
Accept.
With this we have finished the wizard and we have already configured our NPS server in a quick way to accept connections from APs and Customers..
To tweak the configuration we can tweak within Network Policies the policy created in the Wizard
Or include new APs for example in RADIUS Customers
AP Configuration,
In this part of the document we will look at the configuration of our access point,
We configure the AP to shoot against the NPS server with the following parameters:
– WPA2 Enterprise
– Encryption: AES
– IP of our RADIUS server
– Password shared with NPS server
Domain Equipment Policy,
We created a new policy for the computers in the domain so that they have the Wi-Fi Network configured through a GPO if we are interested.
To do this, we go to Group Policy Management and create a new policy that we will apply to the equipment that we have put in the group created at the beginning of the document 'Wireless Users'’ in which we will configure the following.
Let's go “Equipment Configuration” > “Wireless Network” > “Create a New Wireless Network Policy for Windows Vista and Later Releases”,
We give a name to politics, a description and “Add…” > “Infrastructure”,
We give a name and add the Wi-Fi network.
We configure all the parameters as we have made our network and we go to “Microsoft Protected EAP (PEAP)” > “Properties”
Activate “Validate Server Certificate” and we check the CA of the domain and we accept
Let's go back to the tab “Security” and we put in “Advanced” to activate the “Single Sign-on”.
We accept Everything and we already have configured an automatic configuration policy for connection to our Wifi network.