Associating the DNIe with Active Directory users and authenticating with SmartCard
In this document we will see how we can associate the digital certificates of the DNIe with SmartID (Electronic ID card) with the user accounts in our Active Directory, It is ideal for authenticating our employees without a username and password, of course, we can later associate it with the rest of the services we need, if we have access via the web, Citrix… we'd just need a card reader on each piece of equipment and you're good to go, It could even be used to put a device at the front door in the office to validate physical entry, Time Management… all through smart card-based authentication.
First, to make this document, We will need the following company software SMARTACCESS, Say it's paid software (but very low cost):
– SmartID Corporate Logon: Allows logins with any smartcard with any X509v3 certificate (DNIe for example). These are two components:
+ SmartID Corporate Core Components: These are the basic components, must be installed on the computers to be authenticated (PC's customers) and on domain controllers.
+ SmartID Corporate Administrative Tools: Tool to manage DNIe authentication settings using the SmartID Policy MMC.
– SmartID OCSP Client for DNIe: Software that uses the OCSP protocol to check online the status of the revocation of the DNIe certificates.
Installing SmartID Corporate Core Components,
Installing SmartID Corporate 2008 Core Components has nothing, but we will take into account that the equipment will have to be restarted later, We can also install it by command line (It's an MSI). We will have to install it on all the domain controllers and client computers with which we want to authenticate.
Installation of CSPs for the DNIe,
Download from the official website of the electronic DNI and install the cryptographic modules on the computers or CSP on Windows (Cryptographic Service Provider). We can install it by command line or with a double click, we will have to take into account that later we will have to restart the computer! so if we install by command line: 'DNIe_v6_0_2.exe /zuX’ (where X is the seconds to restart the computer).
Once rebooted, When starting, will request that we install the CA certificate 'AC root dnie', Click on “Install certificate…” and we follow the wizard.
Installing SmartID OCSP Client for DNIe,
We will install this in the equipment that will verify the status of revocation of the electronic DNI certificates, then we'll enable it at the active directory level with a.
Installing SmartID OCSP Client for DNIe is Wizard Mode, but we can also install it silently, It requires a reboot at the end but we can install it at the same time as SmartID Corporate 2008 Core Component. Well, “Following”,
… Wait a few seconds…
If we have a license, we enter it, If we can't test it for 30 Days, “Go ahead”,
And “Close”.
What I said, This equipment would have to be restarted.
To enable it, from a domain controller, we create a team GPO that is applied in an OU with the computers that have the software installed. We add the template that generated the installation to the GPO called “SmartIDDNIeRP.adm”.
And we enable the policy in “Team Setup” > “Administrative templates” > “SmartAccess” > “SmartID DNIe Revocation Provider Configuration” > “Configuration Parameters”, We enable it, We configure the proxy if we have and the audit to generate a log.
Installing SmartID Corporate 2008 Administrative Tools,
It will be the tool we use to manage the association of the DNIe certification authority, an MMC add-on.
We begin the installation of SmartID Corportate 2008 Administrative Tools, “Following”,
…
“Close”
Configuring SmartID Corporate Logon to authenticate with Active Directory users' ID cards,
GOOD, to have new issuers appear in the SmartID Policy Console, We have to meet the requirements:
– The Active Directory must have each third-party issuing CA in the NTAuth store in order to authenticate users in the Active Directory.
– Each third-party root CA available in the trusted root CA store of all domain members. The intermediate CAs of the certification chain, if any, must also be in said warehouse.
So the first thing, we need the root certificates of the DNIe CAs, we can easily achieve this by exporting them from a DNIe certificate or downloading it from the official website.
To do this,, from a DOS console on the domain controller we run: 'certutil.exe -dspublish -f CERTIFICADO_CA NTAuthCA’
And we'll edit the directive “Default Domain Policy” from the tool “Group Policy Management” Active Directory, We import this certificate from “Equipment Setup” > “Windows Settings” > “Security Settings” > “Public Key Policies” > “Trusted Root Issuers” > “Import…”
We start the wizard of a certificate from a trusted root authorities, so we continued the wizard with the DNIE CA CERTIFICATE.
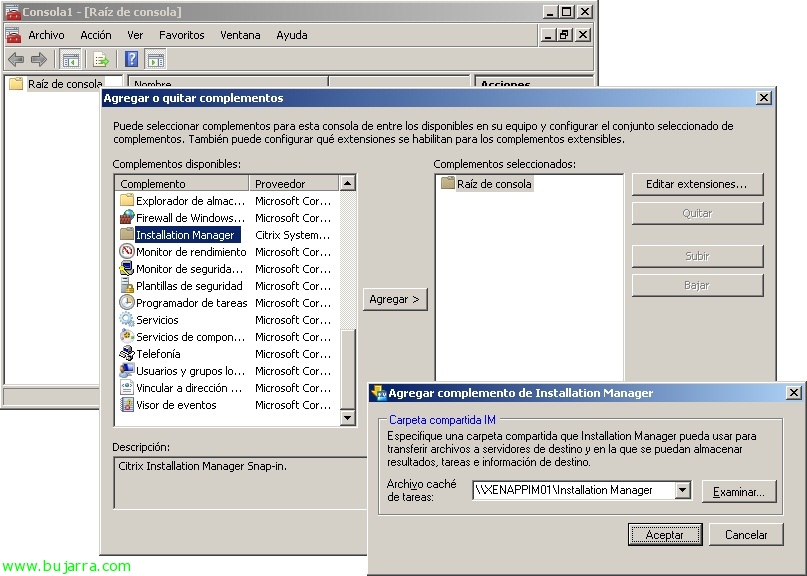
Vale, Let's set up SmartID, for this, we open a new MMC console and add the plugin “SmartID Policy”,
We have to associate against the CA of the DNIe (of the General Directorate of the Police) the ownership of the matter with its OID to then correctly identify the certificates of the users' DNIe. So from “SmartID policies” > “Certificate Association Rules” > “New” > “New Partnership Rule”
In “Certificate Authority” Select “AC DNIE 001”, in “Certificate Ownership” Select “Affair”, We wrote the “Attribute OID” What is it “2.5.4.5”, we enable it and “Accept”,
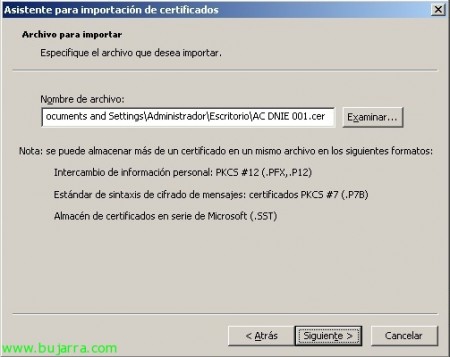
And now all that's left is in the properties of each user of the Active Directory to add the DNIe certificate that we will have exported first, on the “SmartID Associations” since “Add from file”.
We select the certificate of the user in question, “Open”,
Perfect, Accept.
Now, from the “SmartID policies”, Click on “Proving Certificate Against Partnership Rules”, to check that everything is correct,
We select one of the DNIe certificates & “Accept”,
OK, It gives us the right!
Now all that's left to do is try it, on a domain computer with a smart card reader or SmartCard. We enter the DNIe…
We introduce the PIN (Personal Identification Number) or PIN (Personal Identification Number)…
And we reintroduce it for the DNIe authentication application and that's it! it will load our desk, Profile… (I have not managed to remove this, I guess it's normal, In any case, the laboratory environment was to see him) 😉