Connecting to Active Directory with Citrix Access Gateway Using RADIUS
If instead of using local users with Citrix Access Gateway what we want is to take advantage of our Windows Active Directory, our domain users to validate us when connecting from abroad, we must install the IAS service on a server in our network (Internet Authentication Service), configure it and indicate in the CAG that it is so. Be careful, if the CAG is in the DMZ, we need to map the RADIUS ports to the IAS server, What are the 1812 and the 1813, TCP both.

Well, lo primero de todo en un servidor de nuestra red es instalar el servicio de IAS, for this, We install it from “Panel de Control” > “Add or remove programs” > “Add or remove Windows components” > Click on “Network Services” y después en el botón de “Details…” para poder seleccionar el componente “Internet Authentication Service”, lo marcamos y aceptamos todo para instalarlo.

Once installed, We open it, from the “Administrative Tools”, Select “Internet Authentication Service”,

Lo primero de todo es crear el cliente, que será el CAG, for this, from the console, envelope “RADIUS Customers” with right click select “Nuevo cliente RADIUS”,

Le indicamos un nombre descriptivo cualquiera que sirva para que nosotros le podamos identificar; y le ponemos la dirección IP del CAG o el nombre completo DNS del CAG, “Following”,

In “Cliente proveedor” Select “RADIUS Standard”, y aquí es donde le indicaremos cual será el secreto para que se puedan validar entre el IAS y el CAG, este secreto posteriormente será el que le indiquemos al CAG, “End”,

Ahora debemos indicar una directiva para el CAG, We are going to “Directivas de acceso remoto”, con el botón derecho y seleccionamos “New remote access policy”,

“Following”,

We select the second option “Set up a custom policy” and we provide a descriptive name, we will use the policy to indicate who can connect using the CAG, “Following”,

Click on “Add…”

We select at the end “Windows-Groups” and click on “Add…”

Click on “Add…” to select the Windows groups, from the DA that we want to allow to connect to the CAG,

We write the name of the group where we have the users we want to connect to the VPN, in my case in my D.A. I created a group called “UsuariosCAG” where I will add all those I want to grant access to. We select the groups of interest and click on “Accept”,

We check that our groups appear and click on “Accept”,

“Following”,

Select “Grant remote access permission” to give this group of users access to the connection, “Following”,

Click on “Edit profile…”,

On the “Authentication” we must uncheck the first two checks “Microsoft Encrypted Authentication version 2 (MS-CHAP v2)” and “Microsoft Encrypted Authentication (MS-CHAP)”; and we check the other two boxes “Encrypted Authentication (CHAP)” and “Unencrypted Authentication (PAP, SPAP)”,

On the “Advanced options” we delete what is selected by selecting them and clicking on “Remove”; and then we click on “Add…”,
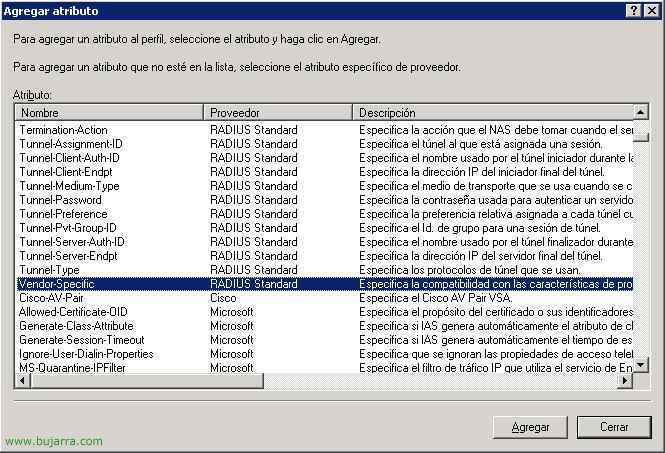
We select the attribute “Vendor-Specific” and click on “Add”,

Click on “Add”,

In “Select from the list” Indicate “RADIUS Standard” and below, we must indicate that “Yes meets” the RADIUS RFC standard, Click on “Configure attribute…”

We must add the “Attribute value” with the following data: “CTXSUserGroups=” (No quotation marks) followed by the name of the user group from the Windows domain that we added earlier, in my case it was UsersCAG, so it would look like this: CTXSUserGroups=UsersCAG. If for any reason we have more than one group, we will separate them with a semicolon (;), Accept,

Accept,

We indicate that “No”,

And we can continue, Click on “Following”,

Comprobamos que todo está bien y finalizamos,

Vemos que la directiva que hemos creado se queda como máxima prioridad con Orden 1. Ya hemos acabado con la parte de Windows, ya no hay más que configurar aquí, ahora todo será desde la consola de Administración del CAG.

Abrimos la consola para administrar el CAG, “Access Gateway Administration Tool”, we go to the tab of “Authentication”, podemos dejar ambas autenticaciones, la de usuarios locales y crear una nueva para los usuarios de RADIUS, Anyway, in this example, solo aceptaré usuarios RADIUS así que la autenticación que trae por defecto la borrare, To this end, from “Action” > Click on “Remove Default realm”,

“Yes”,

Ahora en “Add an Authentication Realm” indicaremos una llamada “Default” and click on “Add”,

Seleccionamos en tipo de Autenticación “RADIUS authentication” and click on “OK”,

Debemos indicarle al CAG cual es el servidor RADIUS, for this purpose in “Primary RADIUS Server Settings” in “IP address” pondremos la dirección IP del servidor RADIUS, The default port is the 1812, and now we must set the secret we created earlier on the RADIUS server when creating the RADIUS client. Click on “Submit” to save your changes. If for some reason we have another RADIUS server, we will indicate it below, on the secondary server.

“OK”
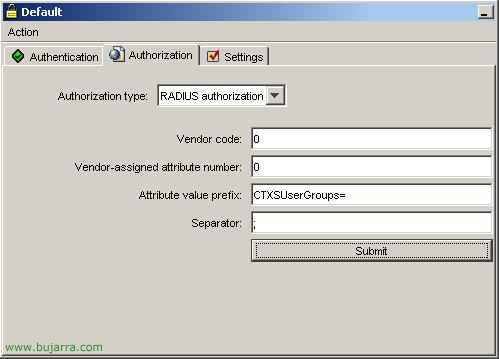
And we check that in the tab of “Authorization” everything is the same as in the upper image:
“Vendor code” = 0
“Vendor-assigned attribute number” = 0
“Attribute value prefix” = CTXSUserGroups=
“Separator” = ;
Click on “Submit”,

“OK”, there shouldn't be anything else to do, now try to connect from the outside to verify that everything is fine.

To check any events we will see them on the RADIUS server, in the “Event Viewer”, it will indicate who is connecting properly or who has tried to connect and could not.
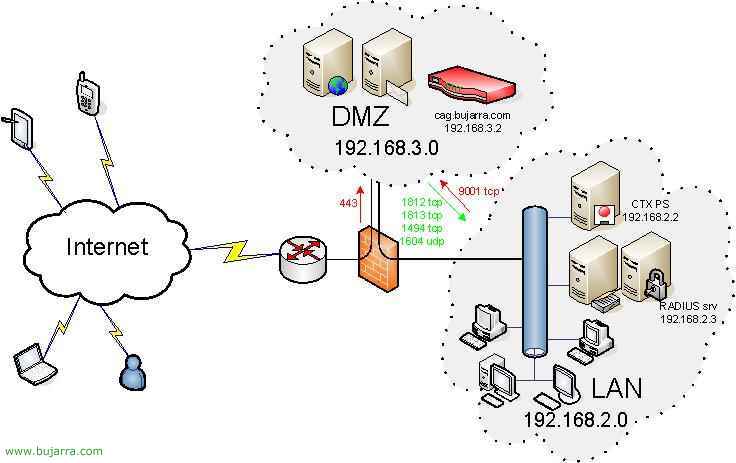
Está sería la configuración final del CAG en la DMZ apuntando al servidor RADIUS:

From the internet FW side, we should only open the port 443 tcp to the CAG so that clients can access to download the client software and connect to the VPN. From the LAN network to the DMZ network, we should only open the port 9001 tcp to the CAG to be able to manage it remotely with the Administration Tools. And from the DMZ network to the LAN network, we should open the ports that we are interested in, if we use RADIUS we will redirect the 1812 tcp and the 1813 tcp to the IAS server. The 1494 TCP (or the 2598 tcp if we use “Session reliability”) to the Citrix server and if we are interested in the 1604 TCP for when from the Citrix client (PN or PNA) we browse to look for the Citrix community.
www.bujarra.com – Héctor Herrero – Nh*****@*****ra.com – v 1.0