Allowing connection to our VMware View desktops 4.6 from abroad
By default, PCoIP connections are direct between the VMware View client and the final virtual desktop (where the View Agent resides), this from the version 4.6 changes allowing you to connect through a server that acts as a reverse proxy as it does not ensure the connectivity of the UDP frames that are sent if you do not redirect PCoIP through the Security Server. This Security Server will allow us to connect from the outside without VPN's and without having to open PCoIP to each virtual desktop, since he will be in charge of connecting to the Connection Server and the Connection Server to the virtual desktop.
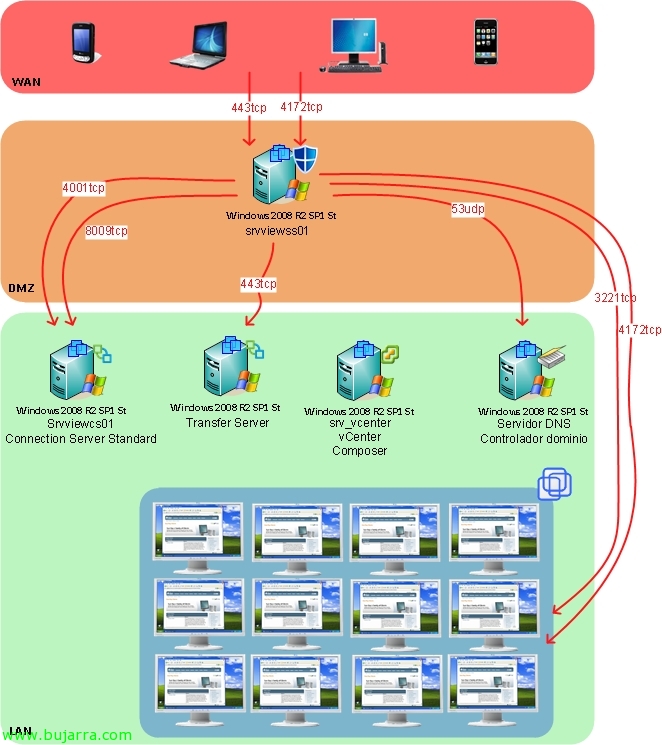
As you can see in this image this will be the stage that we will set up, a VMware View Connection Server with the Security Server feature in the DMZ that will enable connectivity from the outside to our virtual desktop infrastructure. Authentication will be carried out using HTTPS (sure) and then the PCoIP connectivity will start with 4172tcp and finally use UDP since the size of the packets it sends will be larger. So at no time does this server offer us security at the PCoIP level simply for authentication, since PCoIP by default is already encrypted (with a 128 bits in an AES algorithm). This server will connect to the Conection Server (The broker) and present you with the desktop, so we will need to allow 4172tcp and 4172udp traffic between the client and the security server, as well as from the Secure Server to the 4172udp client. Now, from the Security Server to the virtual desktops we must be able to reach through 4172tcp and 4172udp while the virtual desktops to the Security Server with 4172udp.
Basic bandwidth consumption using PCoIP on a basic computer with office automation, No videos, Not even 3D, and more or less default installation of Windows consumes between 200kbps and 250kbps, Even so, we must always consider that at any given time one of these devices can give us a peak of 500kbps/1Mbps, all this considering that it is a continuous work with said desk, since even this consumption could stabilize at 100kbps. If we will have teams watching videos (480p) We will think about 1mbps of joint. The bandwidth we will need will therefore be calculated with the following formula: (XXXkbps/0.80) x No. of teams. Obviously, the better we tune the client operating system, the less we will need, both bandwidth and CPU, memory, disk access…
In principle, this computer should not belong to any domain, it is not a requirement and with it we will obtain a somewhat more secure DMZ. We begin the installation of the Security Server from the VMware View Connection Server installer, “Next”,
We accept the US patent agreement, "Next",
"I accept the terms in the license agreement" & "Next",
The default path of the Security Server installation will be: "%ProgramFiles%VMwareVMware ViewServer", "Next",
Select “View Security Server” & “Next”,
…
The Security Server must be associated with a Connection Server on the LAN that will be the one to pass all the external requests, on this Connection Server we will enable the Gateway to allow such connections (We will take into account what has been said, it must be a Windows 2008 R2). We indicate the name of the CS & “Next”,
GOOD, It asks us for a password to be able to pair both servers, we indicate the one we are interested in but before continuing we must configure it in the corresponding Connection Server.
To do this, from the web the VMware View Administrator
We will go to “View Configuration” > “Servers” Select the server we are pairing to “More Commands” > “Specify Security Server Pairing Password…”,
We type a couple of times the key we want for this pairing & “OK” & We continue with the installation wizard,
Now we must indicate the external URL that is the one that users must type to connect from the outside. In addition to the fixed public IP address that will be the one that will resolve said FQDN name that will be the one to connect via PCoIP, this personally I think is not good since there are environments that through GSLB balance their sites responding to different public IPs depending on several internal factors. But, well…
It tells us that it will open those ports at the Windows firewall level, well “Configure Windows Firewall automatically” & “Next”,
“Install” to begin installation,
…
List!
If we go back to the web administration console of the VDI environment in “View Configuration” > “Servers” we can confirm that in the “Security Servers” the new server that we have just installed appears and if we enter its options we have correctly the external URL as well as the IP that we have perviously configured in the installation wizard. Now what we will do is allow the Connection Server to which it connects the Gateway function, so about the CS > “Edit…”
Mark “Use PCoIP Secure Gateway for PCoIP connections to desktop”, we must take into account that in the Connection Server in which we will enable this parameter, all internal clients connecting through this CS will be connected using the gateway, so it may be an option to have at least two Connection Servers, one for external access and the other internal; in order to arrange them replicated. We therefore configure the “External URL” and “PCoIP External URL” with the parameters indicated above & “OK”, this would provide external access to our VDI organization through VMware View Client!