Replacing Certificates in vSphere 6.5
To be able to manage certificates in vSphere 6.5, we'll see how to use the tool we have to manage the vCenter Server Certificate Authority. We must make the CA that brings the PSC a subordinate entity of our own CA of the domain and generate certificates in which we do trust and so not even the browsers will trust and other dependencies. At the end of the document, we'll look at how to change ESXi and vCenter certificates.
In this document, we'll use the VMware Certificate Authority or VMCA embedded in the vCenter Server Appliance!
vCenter CA as a subordinate to ours
The first thing will be to have a server in the role of a CA installed and configured, we will open the administration console in Windows and verify that we have the "Subordinate Certificate Authority" template available within the Templates.
The process will be done in a vCSA, but the process under vCenter with Windows is similar, We have the same tool. Well, we log in via SSH on the virtual appliance, We create a folder to drop off the certificates and run the certificate management tool:
[SourceCode]mkdir /root/SSLCerts</p>
/usr/lib/vmware-vmca/bin/certificate-manager[/SourceCode]
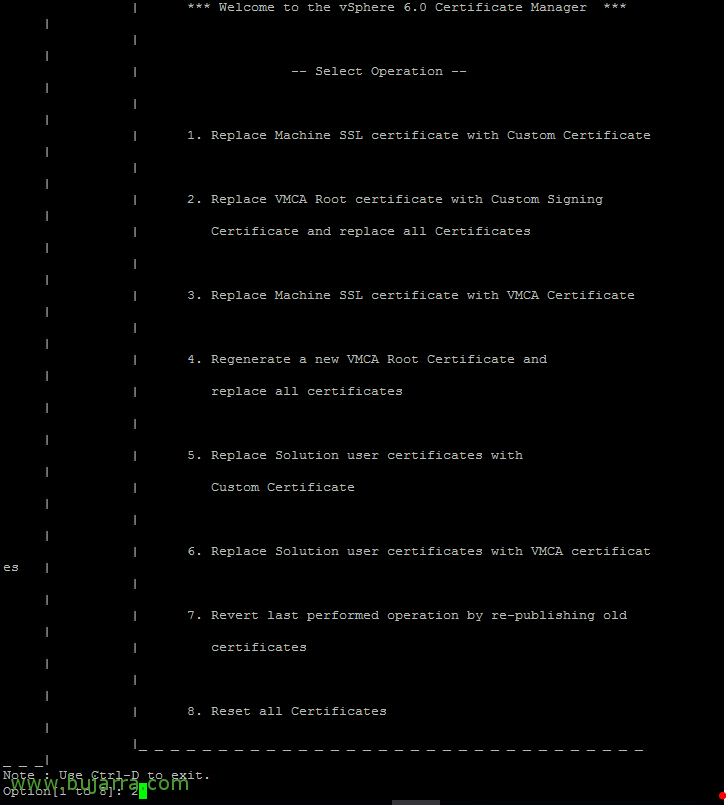
In the certificate management tool, we press "2" to replace the VMCA Root certificate with our own,
Options:
N – To not generate the certificate with the data in the config file.
We enter the credentials of Ad***********@*****re.local
And we enter the data of the certificate that it asks us and remember to write well the Hostname that corresponds to the FQDN
And select "1" to generate the CSR
We specify the directory where you will leave the certificates: /root/SSLCerts
And press "2" to exit,
We verify what he has left us, we have a file with the private key and another with the CSR, we make a cat on the CSR file and copy the certificate request!
About the Active Directory Certificate Management Web, HTTP://FQDN/CERTSRV normally. We will go to "Request a certificate",
We paste the CSR that we have copied and select "Subordinate certificate authority" as the certificate template & click on "Send",
We will also have to "Download the CA certificate" in Base 64, we can find it on the 'Home' of the AD certificate portal.
About the /root/SSLCerts/ folder
[SourceCode]touch vmca_signing_cert.cer</p>
I saw vmca_signing_cert.cer[/SourceCode]
We edit, as we can see, with 'vi' a file to which we must paste the certificates that we have generated in the previous steps. We will paste the vCenter certificate first and then the CA certificate of our domain.
Recorded & We go out with :wq
We verify the files we have... With 'ls -ll'.
And we launched the vSphere Certificate Manager again to finish the process and install the certificate we just created
[SourceCode]/usr/lib/vmware-vmca/bin/certificate-manager[/SourceCode]
Option "2" to replace the VMCA root certificate.
We enter a privileged user, usually those of Ad***********@*****re.local
Option "2" to import the certificate we just generated.
Enter the certificate file: /root/CertSSL/vmcsa_signing_cert.cer
Enter the private key file: /root/CertSSL/vmcsa_issued_key.key
Y – To confirm and replace the certificate with this.
And we wait a few minutes while the process of installing the certificate finishes in all the services and restarts them to reload!
We will be able to verify that the browser no longer gives errors and the certificate is fully valid! We also see the certification chain,
What an eye, the certificate of the Subordinate CA must be installed on all the computers in the domain so that they trust it, or install it manually, but it's easier with a GPO!
Replacing the certificate on hosts
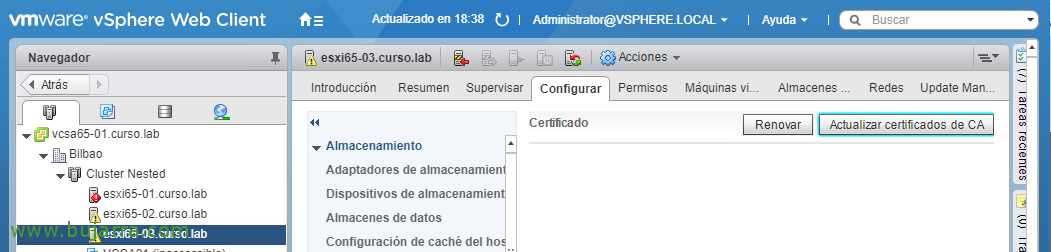
To replace a certificate on a host, We will do it in a very simple way, select it and from "Configure" > "System" > "Certificates", click on "Update CA certificates",
Select "Yes",
And now we can click on "Renew" to replace the certificate!
"Yes" to continue,
If we open a browser against an ESXi host that we have modified, We will be able to see how we have a fully valid and trusted certificate, where it has been signed by the VMCA CA of our PSC!