Requiring Client Certificates for Citrix Access with NetScaler
In this document, we will see how to configure from the Citrix NetScaler appliance that it is mandatory for client computers to have a certificate installed locally (they could also have it on a pen drive) so they can access the Citrix portal, to your applications; without the certificate they would not even see the corporate portal.
This is an additional complement to further secure our environments, we will be able to give certificates to our users by generating them from our CA and we will be able to revoke them when necessary, at that time without a valid certificate the user would not be able to enter the Citrix web portal, is an Access Gateway that goes against a StoreFront or a Web Interface.
GOOD, on our AC that we have already installed, we will need to make a backup, for this “Certification Authotity” > “All Tasks” > “Back up CA…”
We mark that you export at least the private key “Private key and CA certificate” and we store it in a directory that we create for that purpose.
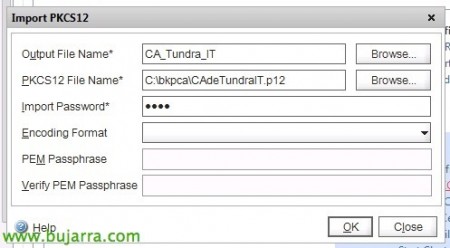
GOOD, already in the Night Stalker, We're going to “SSL” > “Import PKCS#12”,
In 'PKCS12 File Name’ we must select the .p12 file that has generated the backup of the CA; Be careful with spaces, Needless to say in a Night Stalker, ¿No? 😉
We give you a name in 'Output File Name’ and we assign the password we set when backing up the CA & “OK”,
Let's go back to “SSL” > “Manage Certificates/Keys/CSRs” and we confirm that we have two new files, both the .p12 and the imported CA certificate, “Close”.
In “SSL” > “SSL Certificates” > “Install…”
We give a name to the certificate that we are going to install, something that refers us to our AC. Under 'Certificate File Name’ and in 'Private Key File Name’ we will indicate the path of the generated file when we import the PKCS12 file. “Install” and we confirm that not only has he created well.
The next thing will be to register the CRLs (Certificate Revocation List) to be able to later force it to check whether the certificates are valid or not. Since “SSL” > “CRL” > “Add…”
We indicate a 'CRL Name’ and a file, we select DER format, select the CA certificate, check 'Enable CRL Auto Refresh’ and configure the access method against our certificate authority's CRL, we can easily do it through HTTP and against the URL of the .crl file that we will easily obtain within the web environment of management of the CA (the spaces of the URL can be entered with ' ', if we have) & 'Port’ to the 80 which is usually the most normal (Also be careful with the firewall rules that we may need, if the NS is in the DMZ and the CA in the Server Network). We will mark 'Interval’ a “NOW” to force the check and see if what you entered is correct or not. “Create”,
And that's it! we confirm that in 'Validity Status’ we have 'Valid'!
If in 'Days to Expire’ We have something other than '1', we need to modify the CRL publishing interval within our CA. We go to the Certification Body, Right-click 'Revoked Certificates'’ > Properties > in the tab 'Parameters for the publication of revocation lists', We changed the interval to 1 day/time & We don't make differentials. We will update it with a right button on 'Revoked Certificates'’ > 'All tasks’ > 'Publish'.
If it's correct, We modify the CRL and schedule the check against the CRL unless it is daily and before the entry of the employees, so that all certificates revoked the previous day are invalid and deny them access.
Vale, to require in the CAG that the client must previously have a valid client certificate, we will select in “Access Gateway” > “Virtual Servers” > “Open…” our AG.
We will select the certificate of our CA, Click on “Add” > “As CA” to add it to the portal.
At the check-in we will indicate “CRL Mandatory” and we set up in “SSL Paramet…” that it is mandatory.
We must mark “Client Authentication” and we will say if the client certificate is 'Mandatory’ u 'Optional', the normal thing will be to demand it. “OK”. In principle, with the NetScaler we will have already finished. Eye! if at the time of completing the following steps, we have the certificates well deployed and we cannot enter the CAG portal, the website is blank and in the URL we see 'agesso.jsp’ will indicate that either the Web Interface or StoreFront cannot connect against the CAG and return authentication to the clients, since the CAG is requiring certificates and the WI or SF does not have it, it could be solved quickly by duplicating the CAG of the NS but without the requirement of a certificate and the WI or SF will be connected to it (Modifying your hosts file).
If our CA is on Windows 2003 Standard we will not be able to use the modification of certificate templates since they are generated for Enterprise version. We would have to generate the certificates by accessing the certificate request page (HTTP://CA_SERVER/certsrv), generate an advanced certificate request on our CA, where in the template type we will select 'User’ and the format of the application will be in PKCS10 format, once generated, We will export the certificate with a private key and rename it with the name we are interested in to install it to the corresponding user.
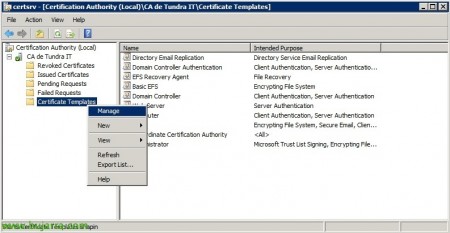
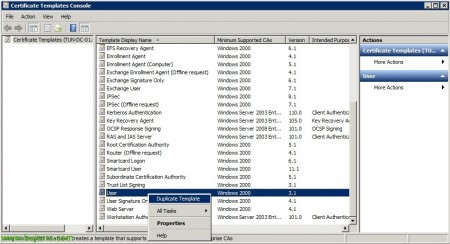
If our CA is on Windows 2003 Enterprise or Windows 2008 or higher, in these versions the CA would accept to modify the templates, so we can generate our certificate templates to taste. So, open the Certificate Authority console > “Certificate Templates” > “Manage”.
We will double the “User”,
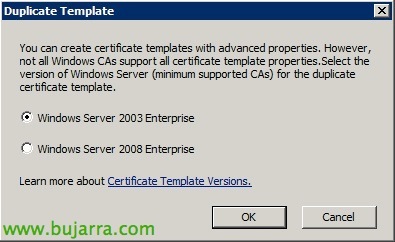
Select “Windows Server 2003 Enterprise” & “OK”
The first thing will be to give a name to the template so that Citrix administrators when they generate certificates to users can relate it correctly. In addition to a validity period.
In this case, they will be templates that we will later fill in manually, no DA integration, So in the “Subject Name” Indicate “Supply in the request” and we will complete it with each certificate. On the “Issuance Requirements” o Issuance requirements, We could mark a check and that each certificate that is requested must be approved by the administrator, and it will not be valid until that happens (from the CMM of the AC should be accepted).
Once the template has been created, we must incorporate it into the CA, for this, since “Certificate Templates” > “New” > “Certificate template to be issued”.
We select the newly created template & “OK”,
Requesting certificates for users,
This would be the section that we should repeat as many times as users who have access from the outside to the organization, We must generate one certificate per user, What is the ideal, but not mandatory, since having a password the user will not be able to export the certificate or at least will not be able to import it on other computers without knowing the password; and if we revoke it, we only affect this user and not all of them..
We open http://CA_SERVER/certsrv, We validate ourselves as an administrator, Click on “Request a certificate”,
“Advanced certificate request”
“Create and submit a request to this CA”,
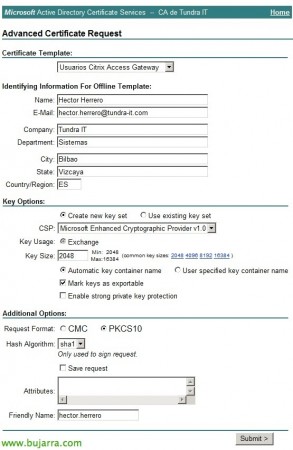
In “Certificate Template” We select the newly generated template, and having selected that we would enter the data manually, now we will have to complete them, We will indicate the details of each user; remember select PKCS10 as the format, at least 2048bits of key & “Submit”,
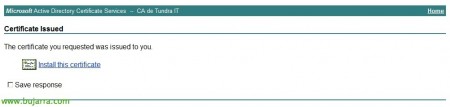
How we trust the site, the ActiveX plugin will have been executed that will allow us to create and install this certificate, Click on “Install this certificate”!
You will have installed the certificate on the computer from where you have just generated it, Normal, will be to export it (with private key & Password protected!) and install it on the user's computer. With this we have already forced that without a valid certificate from our CA, our organization's Citrix portal cannot be accessed, be to access applications (XenApp) or desks (XenDesktop).