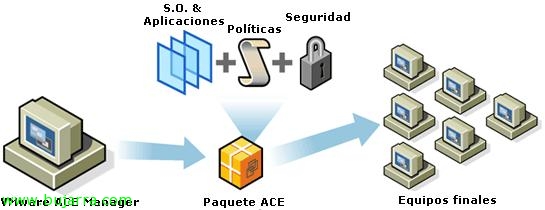
Creating and Distributing VMware ACE Packages
Ok, once we are clear about how VMware ACE works, we have a VMware ACE server mounted and we have an instance of a virtual machine created, ready for distribution, and we have configured your policies, In this document, shows how to create packages and how certain policies we've previously configured would affect you. Being able to later distribute these packages to be able to run the virtual machines of it.