Installing and configuring Citrix Secure Gateway 3.0 – CSG 3.0
This procedure explains how to secure a Citrix environment over the Internet using CSG or Citrix Secure Gateway, This will also allow us not to have to open the typical ports 1494 and 2598 firewall, but simply with the 443 or the one we want will pass everything to the CSG and it will manage it. It will be a secure connection using a server certificate installed on the web server.
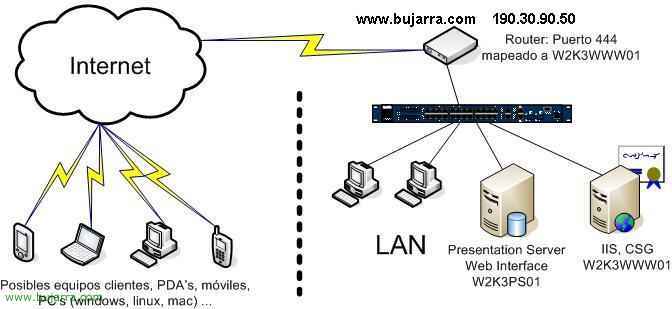
My case, I have a simple network, without DMZ or anything, a LAN, A normal network, Where do I have a server (Or as many as we want) with Presentation Server and in one of them with the web interface installed (Web Interface), in W2K3PS01, What I want is for my offline customers to connect to it securely, for this I install CSG on a server (can be the same as the Presentation Server – PS, But it's not my case), Since I have a published web server I'll take advantage and install it on it, since CSG requires IIS with a server certificate. Me on my web server (W2K3WWW01) I have a company website (port 80) and a secure extranet (port 443), I need a port to make my clients connect from outside to my CSG, I'll use the 444 with secure layer. More data, I touch everything, I changed the XML port of the 80 to the 82, so my XML port is the 82. Once the whole configuration process is finished, when someone wants to connect to my Web Interface from the outside, they must put https://www.bujarra.com:444, if we don't want them to only connect with the web client and we do with the Program Neighborhood, we will specify it during the configuration of the CSG. The normal thing is to have the W2K3WWW01 in a DMZ and map the ports 443, XML (82 in my case), 1494 and 2598 to the W2K3PS01.
Vale, First things first, to install CSG on W2K3WWW01 we must put the component CD in it, We will select the second option “Secure Gateway”.
And again “Secure Gateway”.
An assistant will jump us, It is a very fast installation and takes up hardly any space and/or performance on the server, Click on “Next”.
We accept the agreement and “Next”,
Select “Secure Gateway”, the first option and “Next”,
The path where you will install it by default, If we agree, click on “Next”,
Which user the Secure Gateway services will start with?, the normal thing is to indicate “LocalSyatem”, Continue.
… wait a few seconds while it installs…

Vale, already, So simple is it installed, “Finish”,
But now it remains to configure it, Click on “OK” to skip the setup wizard,
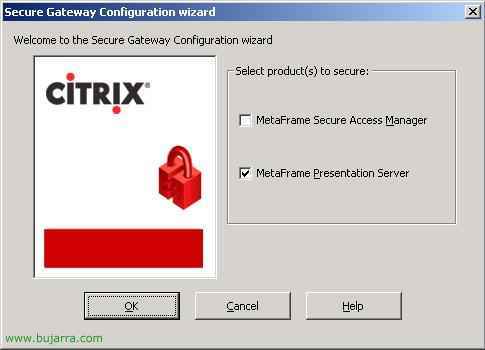
What products we will insure, in my case, only “Metaframa Presentation Server”, We give “OK”,
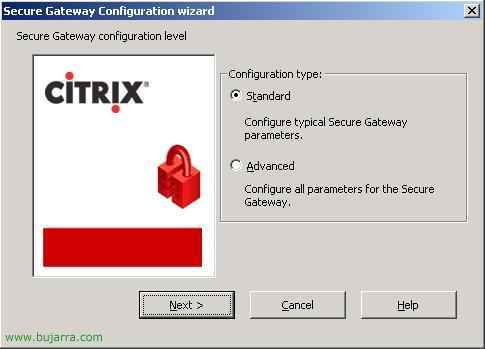
“Standard” and “Next” (If we want to customize a little more we can do the advanced assistant),
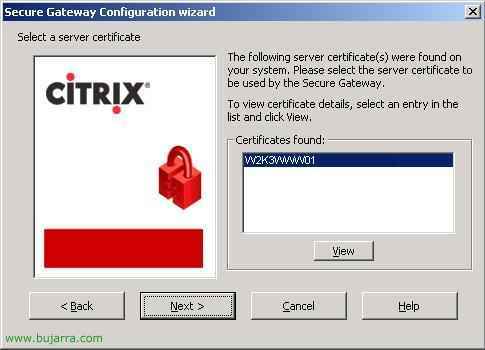
Here it will show us the server certificates installed in this IIS, if we don't get any we must either generate it with a CA, or buy them from an issuer such as Verisign, If a valid certificate we can't continue, to install one or generate it if we don't know we can look at these procedures: Install an AC –HERE o Install a certificate – HERE. We give “Next”,
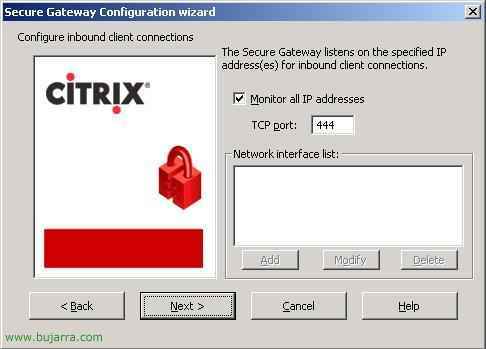
Vale, This will be the port to which customers will connect us from outside (From the Internet), In my case I will use the 444 (and not the 443 which is that it comes by default, It's because I have it in one with a company extranet). “Next”.
I won't use restrictions, So “Next”,

Vale, now I need to indicate who the STA server is (STA is the Metaframe server that has the Presentation Server database, if we only have one HP it will be that, or if we have more, it will be the first SP to be installed in the community) So to add it we click on “Add” and in FQDN we must indicate its full name, the “Path” We leave it as it is and in “Protocol settings” we indicate the port with which the CSG will communicate with the PS, What is XML, In my case the 82. Traffic between the STA and CSG does not need to be safe, since that's our LAN, We give “OK” and then “Next”,
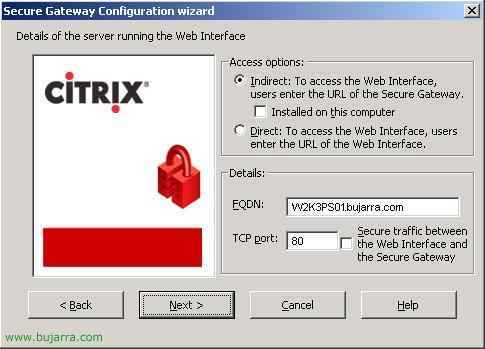
Ask us about the Web Interface, where it is and in what form, in my case the Web Interface is in W2K3PS01 (It has to be the default website of the website) and in the port 80, So I put the first option “Indirect” and unchecked the check because it is not installed on this server. I indicate below the data you ask me for and we give “Next”
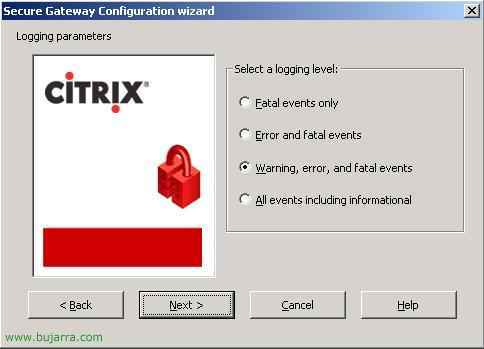
What kind of events do we want it to put in the Event Viewer?, it will create a section just for it in Secure Gateway, in my case I indicate errors and 'fatal' events, We give “Next”,
We mark the check of “Start the Secure Gateway” to start the CSG service for us. And click on “Finish”.
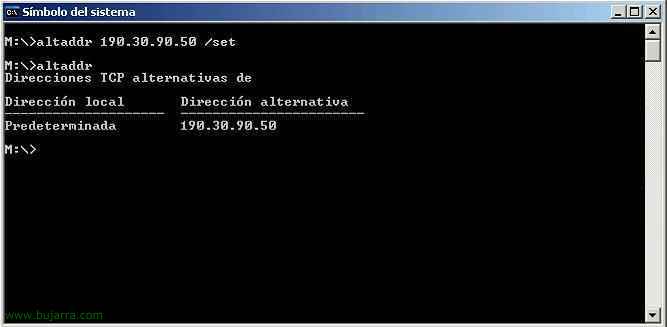
GOOD, the CSG part is already finalized, now some tweaks in the PS, when a customer from the internet connects to Citrix, connects to our public IP (in my case 190.30.90.50) and from that IP it is forwarded to the PS server, the PS responds to the IP of the request that is not the client's, so the connection would fail because it returns your private IP instead of the public and from the outside logically you cannot connect to the private one. In the PS an MSDOS console is opened and we add the CSG's public address as an alternate address, with ALTDDR, so from an MSDOS console on the PS: “altaddr IPPUBLICA /set” and we check that she is well involved with “High”.
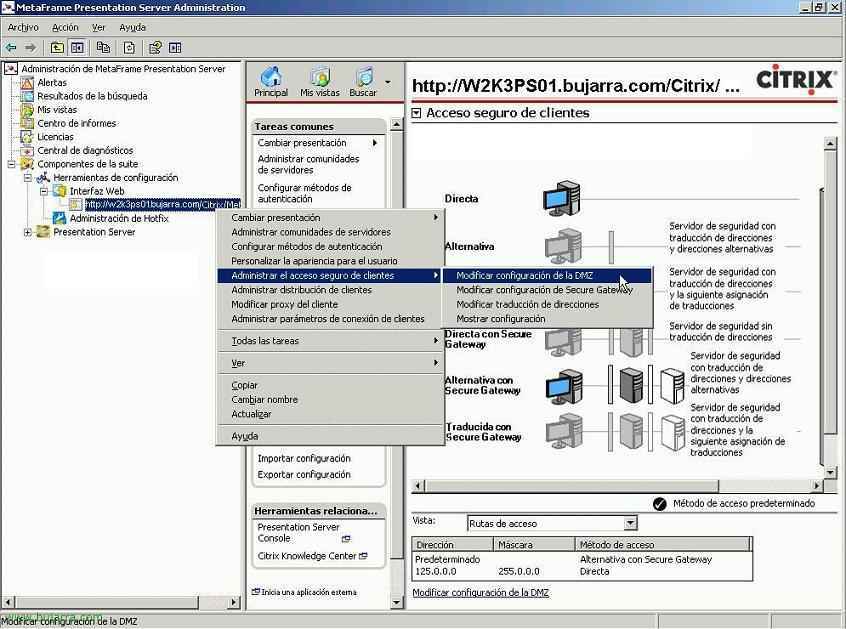
Vale, now from the server that has the Web Interface, We open the console: “Home” > “Programmes” > “Citrix” > “Metaframe Presention Server” > “Access Suite Console for Presentation Server”. And we go to “Components of the suite” > “Configuration Tools” > “Web interface” and on ours, Right Button “Manage secure client access” > “Modify DMZ settings”
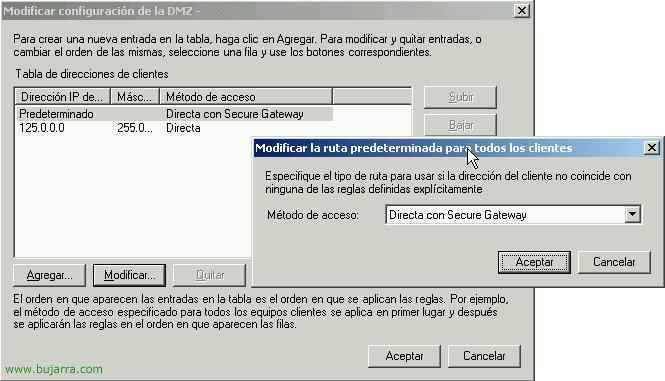
On the Connection “Default” We click on the “Modify” and instead of being “Direct” Will “Direct with Segure Gateway” and We Accept. If from our LAN the workstations also access the Web Interface and we do not want them to use CSG (since they are on the LAN), we can add an IP range and tell you it's a direct connection (we would click on “Add…” and we put the IP range of our LAN with its mask, we indicate in the access method that it is “Direct”. We accept everything.
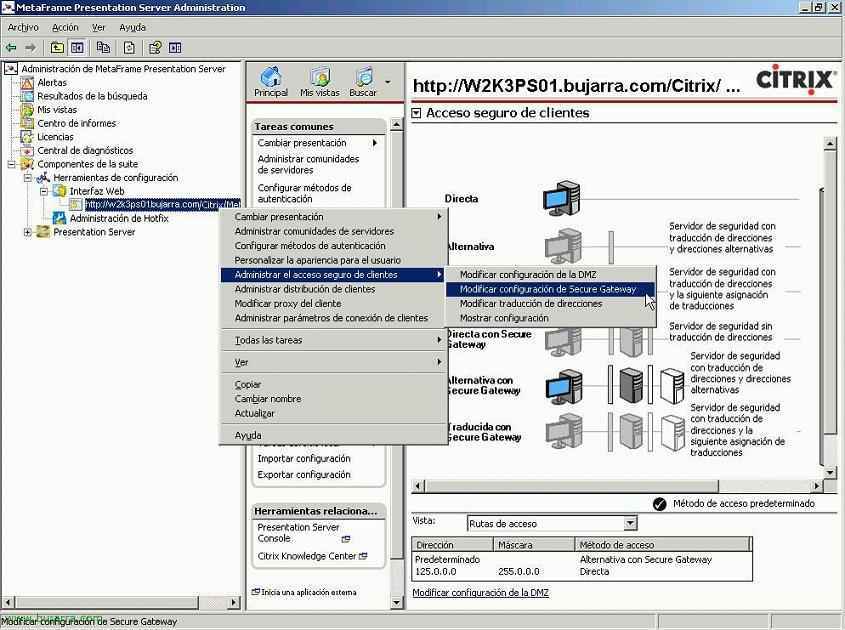
And now again, since, “Components of the suite” > “Configuration Tools” > “Web interface” and on ours, Right Button “Manage secure client access” > “Modify Secure Gateway Settings”.
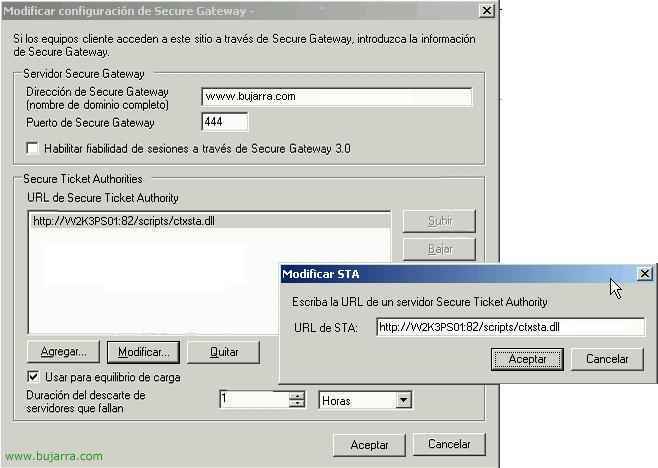
In “Secure Gateway Server” we will put who is the CSG server (I put www.bujarra.com why it is my public name and the one named after by my IIS certificate, If the certificate names the server name, we would put W2K3WWW01, For example), in the “Secure Gateway Port” We'll put the one we've set during setup, the 444 in my case. And in “URL de Secure Ticket Authority” we check that it is our STA server (The first PS) with XML port (In my case the 82), We accept everything.
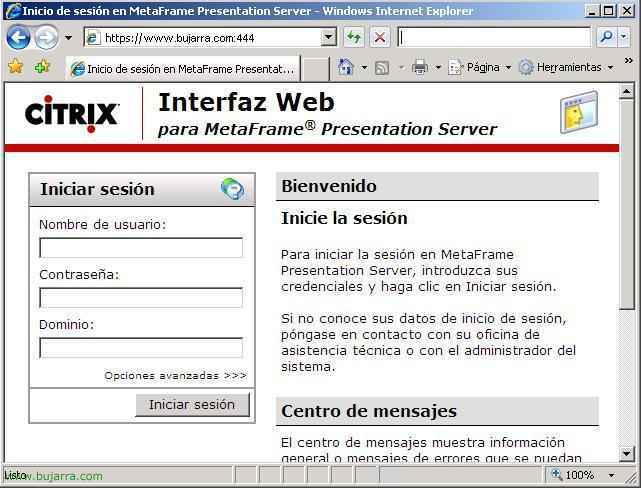
GOOD, Now to try it out, we need to logically map the port 444 from firewall to CSG server, Once that's done, We go to the internet with a laptop with a modem, or whatever, that we are not on their LAN, to try it out, We open a website to https://www.bujarra.com:444 and you must open the web interface, we authenticate and open a published application.

To check if the CSG is really working, we open the bar icon on the client PC.
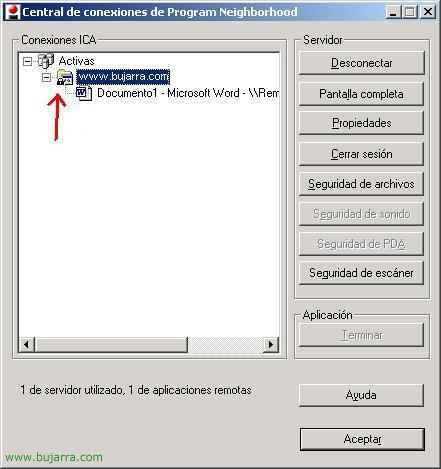
And we'll see a lock come out, that indicates that the connection goes through the CSG.