Creating a High Availability Cluster on Microsoft Windows Server 2008
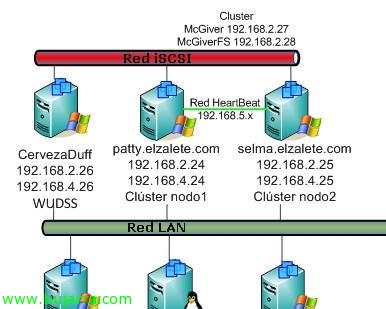
After viewing a document on how to create shared storage for a cluster, Why not create one? Well, the process is similar to Windows 2003, now we will do it for Windows 2008, A new cluster, and it will be for a file server, failover clustering, The process for another type of cluster is similar. With this we will achieve high availability, that if one of the servers falls (node) Don't worry., since there are other nodes that can take the resources and lift the services so that users can work practically without noticing the fall of the node they were working against. Also comment that maintaining a cluster is expensive, This is, We will always keep in mind that both servers will have the same applications installed, in the same way and with the same versions, all this to avoid future problems. It is also advisable to balance the cluster […]