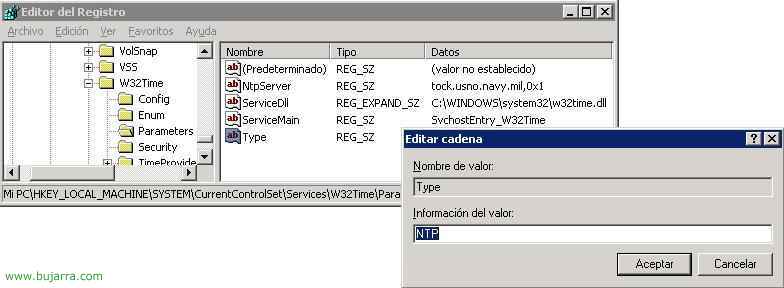
Installing Microsoft Windows 2003 + Domain Migration 2000 a 2003 + Promote yourself as a primary domain controller
In this procedure we will see how to install a server with S.O. MS Windows 2003, How to update a domain 2000 a 2003 and how to promote this server to Domain Controller. To do this, we boot a PC with the Windows CD 2003 and in the BIOS enabled CD boot.